
VP / Distinguished Engineer at Amazon Web Services. Also: Open Source and Apache, Cryptography, Irish Music, mediocre Photography.
9 subscribers
How to get URL link on X (Twitter) App


https://twitter.com/campuscodi/status/1531656724708474880A big difference is that PSP aims to be full end to end solution, replacing TLS and network-level encryption, while VPC encryption is intended to provide additional defense in depth for AWS customer traffic, which mostly already uses TLS, SSH, etc.
https://twitter.com/colmmacc/status/1481670721449385984Our response to issue reports always includes a search for any prior attempts to use the issue. We found none. 2/n
https://twitter.com/matthew_d_green/status/1433451378391883782In s2n, we decided to have separate (per-thread) RNGs for "public" data that would appear on the wire - that's mostly Initialization Vectors, the random sections from "hello" messages, and the random jitter we add to errors - and for secret data used for keys.

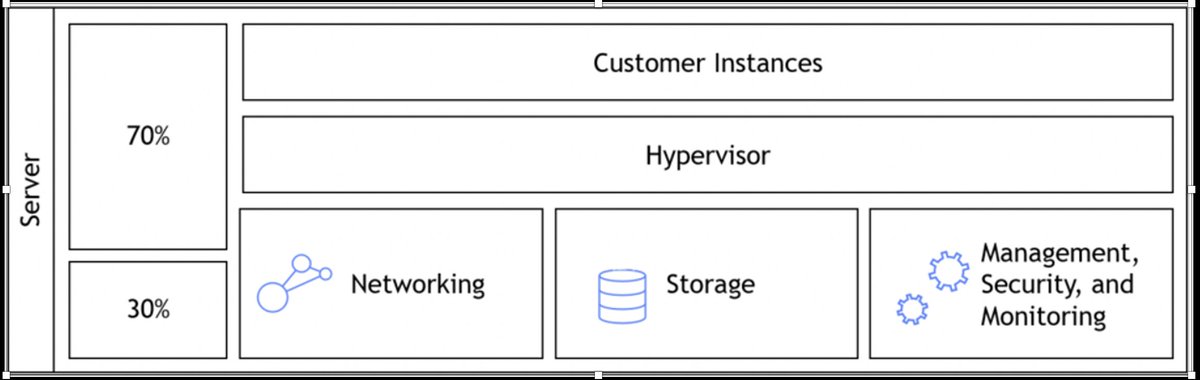
https://twitter.com/ric__harvey/status/1326194491452256257GWLB let's you spread incoming or outgoing traffic over multiple firewalls, intrusion detection devices, packet inspectors, etc. It's horizontal scaling for network appliances, running on EC2 Instances. So far so good ... that sounds like ECMP.

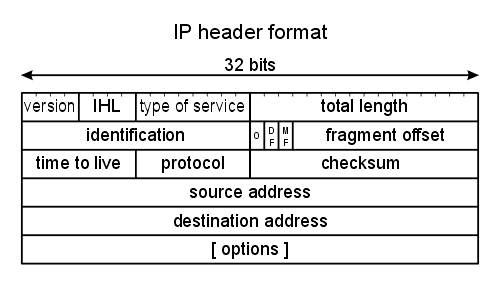
https://twitter.com/dandago2/status/12247727697092198401. If there is any layer that is actually between layer 4 (like TCP) and layer 7 (like HTTP or SMTP) ... *surely* it is TLS. But that's not a layer in the OSI model.

https://twitter.com/colmmacc/status/1143572552180277248The root of trust in any cryptographic or authentication system is usually based on one or two things: key distribution, and high-quality randomness. With Nitro we also have our own high-quality hardware secure random number generators. Key distribution is a harder problem.