
How to get URL link on X (Twitter) App





 "Socket Takeover" should be familiar to traffic nerds. Transferring the listening socket over a Unix Domain Socket with ancillary message (CMSG) + SCM_RIGHTS is *precisely* how HAProxy does seamless reloads.
"Socket Takeover" should be familiar to traffic nerds. Transferring the listening socket over a Unix Domain Socket with ancillary message (CMSG) + SCM_RIGHTS is *precisely* how HAProxy does seamless reloads.



https://twitter.com/gergelyorosz/status/1289971748725719040Some more things to consider:

https://twitter.com/mattklein123/status/1288884133704286208Still remember the days when @mattklein123 claimed “developer productivity was one of the highlights of modern C++” when introducing Envoy and people raising eyebrows at this claim.
https://twitter.com/mattklein123/status/793982852694016000
https://twitter.com/copyconstruct/status/1210097597186076673Cloud vendors have the personnel and the resources to easily keep up with the latest and greatest in the OSS world and roll out things like “serverless pods” (by, I suspect, making things like their custom FaaS runtimes OCI compatible) or whatever the next fad is.
https://twitter.com/shl/status/1143147990485360640There are exceptions, of course. There are some “startups” with an exceptional quality of engineering (Hashicorp comes to mind), and there’s garbage code/engineering to be found at large companies.



 CockroachDB is a distributed replicated transactional database.
CockroachDB is a distributed replicated transactional database. 




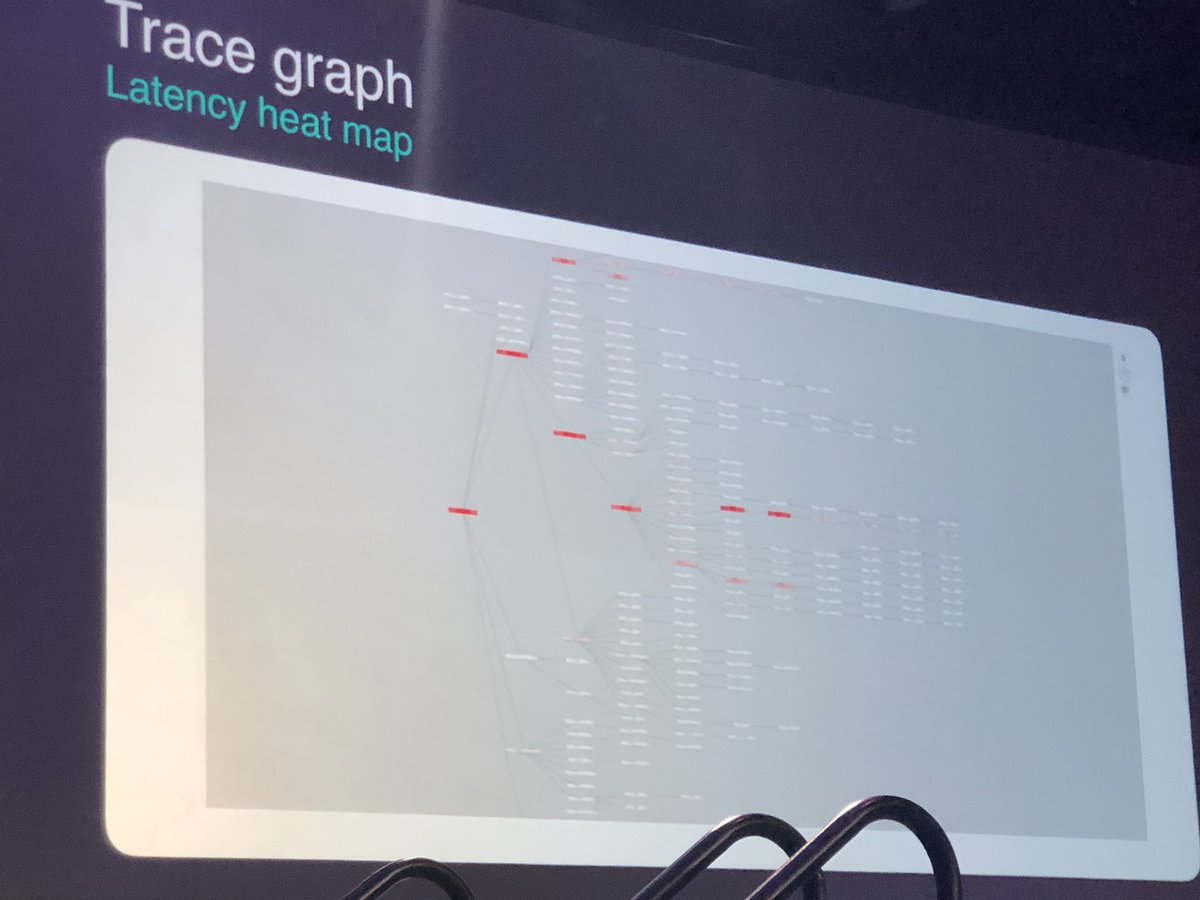 Now @YuriShkuro is talking about a tool that compares traces.
Now @YuriShkuro is talking about a tool that compares traces. 


https://twitter.com/copyconstruct/status/1075086886610169857?s=21There’s been a bunch of research on serverless recently - and Hacker News trashes all of it.




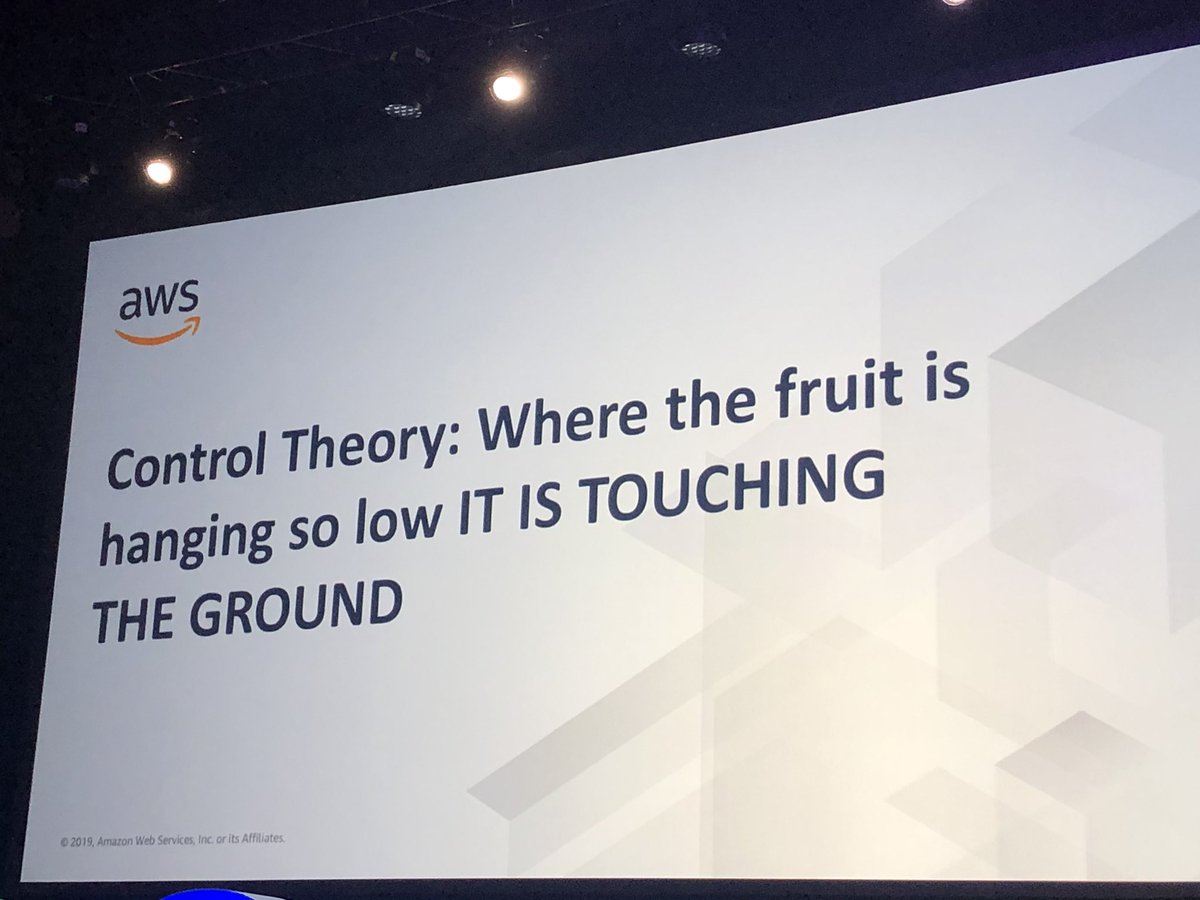 Haha @colmmacc put my DM to him the slides - as an example of observations and feedback in practice! 😁 #QConNYC
Haha @colmmacc put my DM to him the slides - as an example of observations and feedback in practice! 😁 #QConNYC 




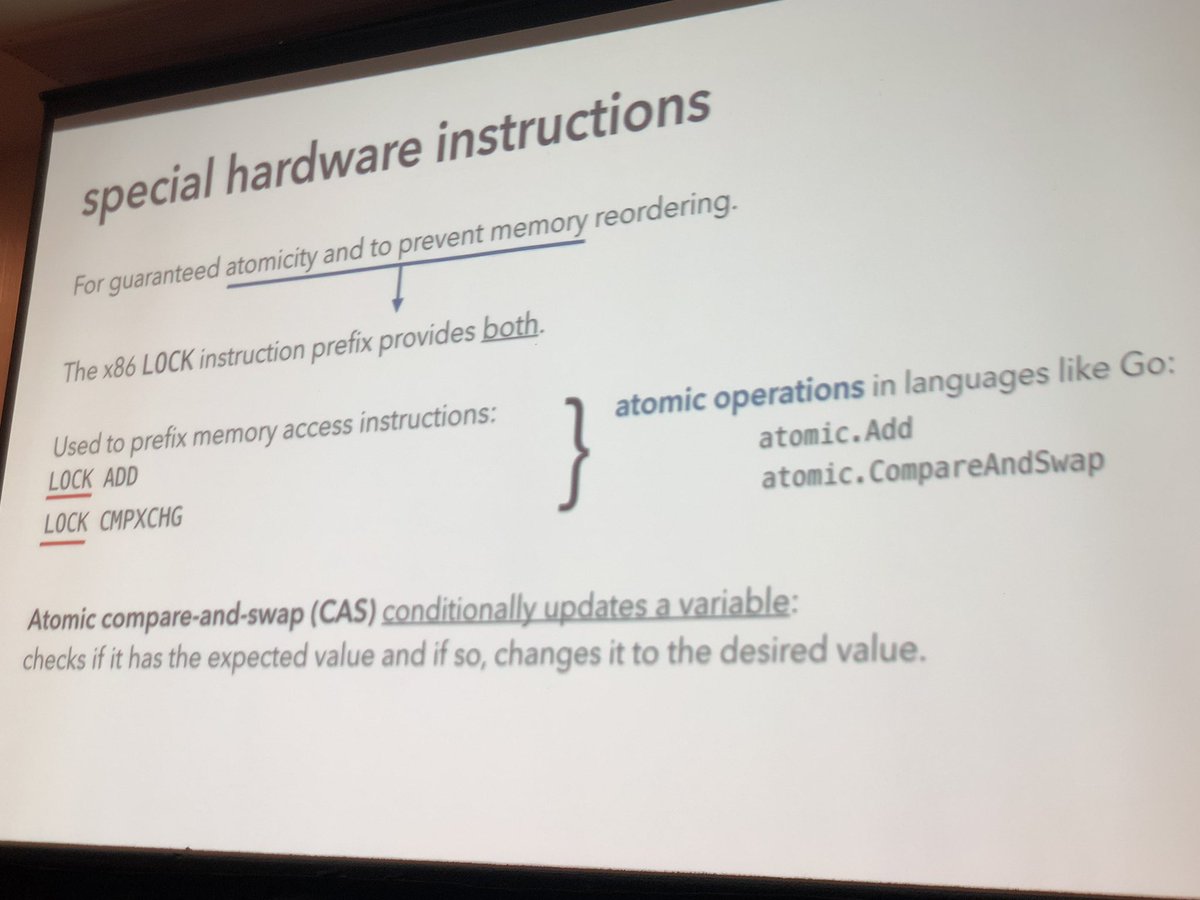
 The compiler and processor reorder instructions. It helps to know the rules. @kavya719 at @qconnewyork
The compiler and processor reorder instructions. It helps to know the rules. @kavya719 at @qconnewyork 
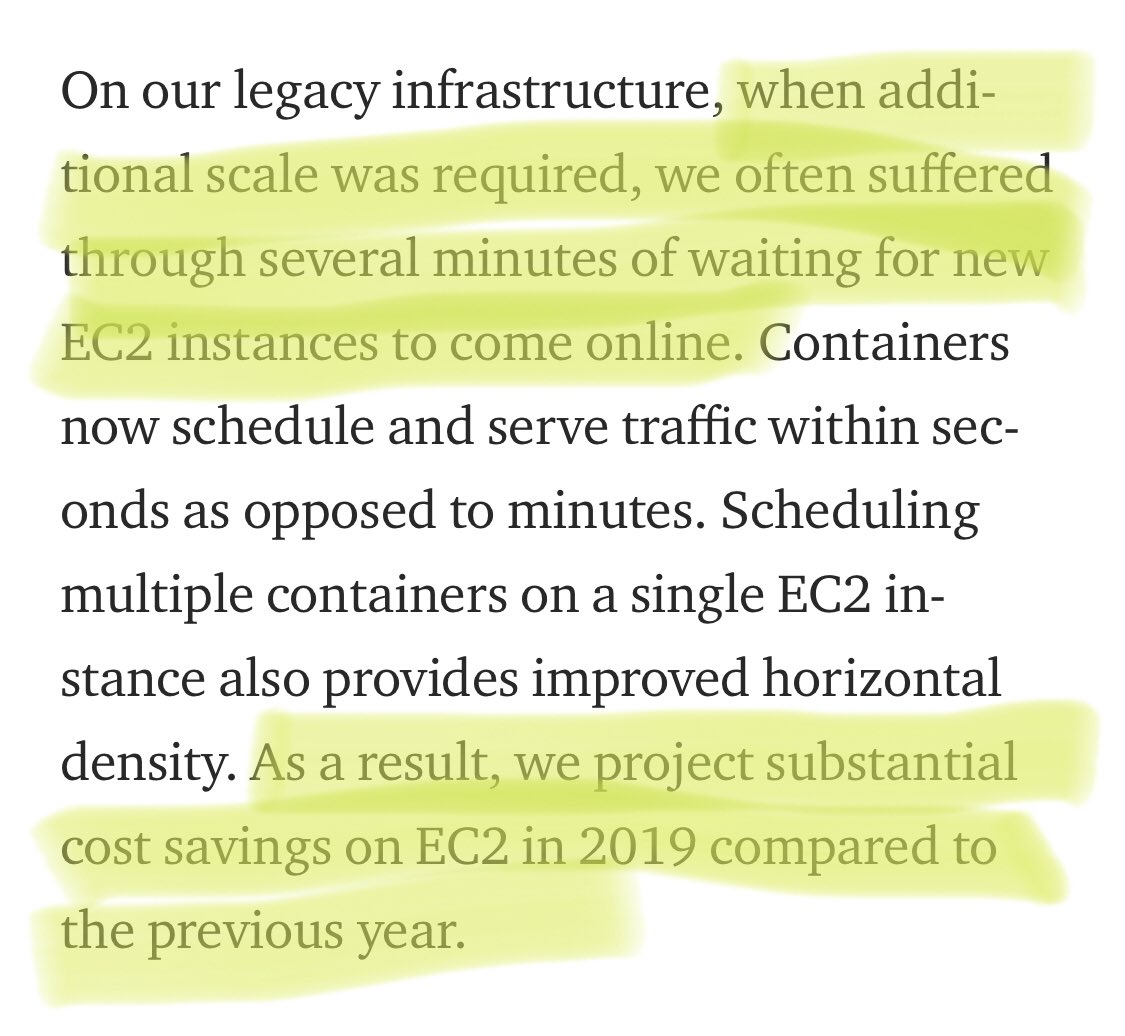
 EC2 startup times alone isn’t very convincing to justify a 2 year effort to make this move.
EC2 startup times alone isn’t very convincing to justify a 2 year effort to make this move. 

https://twitter.com/copyconstruct/status/1072580506892554245Where queries are akin to grep against time partitioned files. One of the important aspects of observability is refining the search space (I believe @el_bhs was the one who mentioned this in one of his recent talks) - which isn't to be confused with visualizing the search space.