
A 'by Hackers for Hackers' podcast focused on technical content ranging from bug bounty tips, to write-up explanations, to the latest exploitation techniques.
How to get URL link on X (Twitter) App


 The UTF-8 visualiser is a must, it shows you UTF-8 encoded bytes, raw bytes, Unicode code points and glyphs all at once.
The UTF-8 visualiser is a must, it shows you UTF-8 encoded bytes, raw bytes, Unicode code points and glyphs all at once. 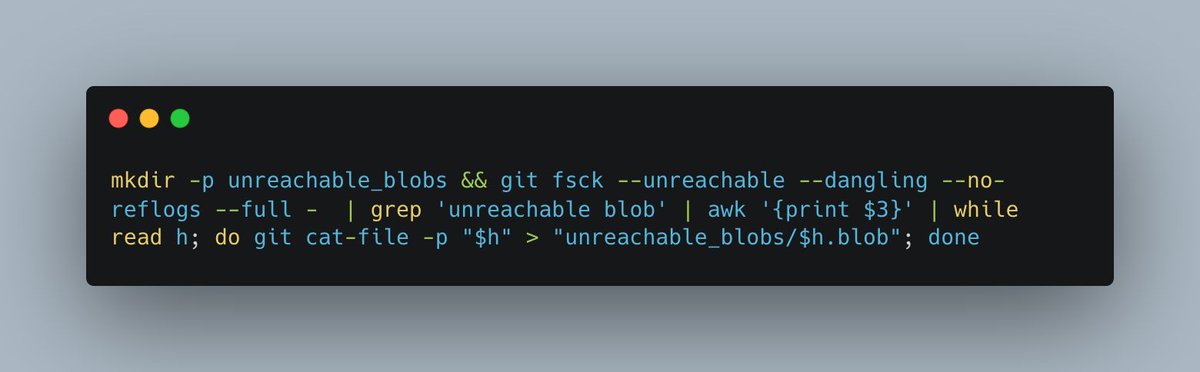
 Methodology:
Methodology:https://twitter.com/slonser_/status/1919439373986107814First, this can be done recursively and, since we can specify multiple URLs per Link header (or multiple Link headers, if you prefer), we can create a continuous stream of requests to our server from a single attacker-controlled image being loaded.

 @joaxcar @garethheyes 1️⃣ Understanding the URL Credential Discrepancy
@joaxcar @garethheyes 1️⃣ Understanding the URL Credential Discrepancy

 @0xLupin @Rhynorater 1. Focus on the main app
@0xLupin @Rhynorater 1. Focus on the main app