
How to get URL link on X (Twitter) App



 Our current tools worship flexibility, extendability, composability, and minimal gas use.
Our current tools worship flexibility, extendability, composability, and minimal gas use.
 Thanks to yourfriend for noticing this! 2/8
Thanks to yourfriend for noticing this! 2/8https://x.com/yourfriend_btc/status/1851707644764991927

 The hardware wallets actually signed `transferOwnership()`, giving control of the lending pool to the attackers.
The hardware wallets actually signed `transferOwnership()`, giving control of the lending pool to the attackers.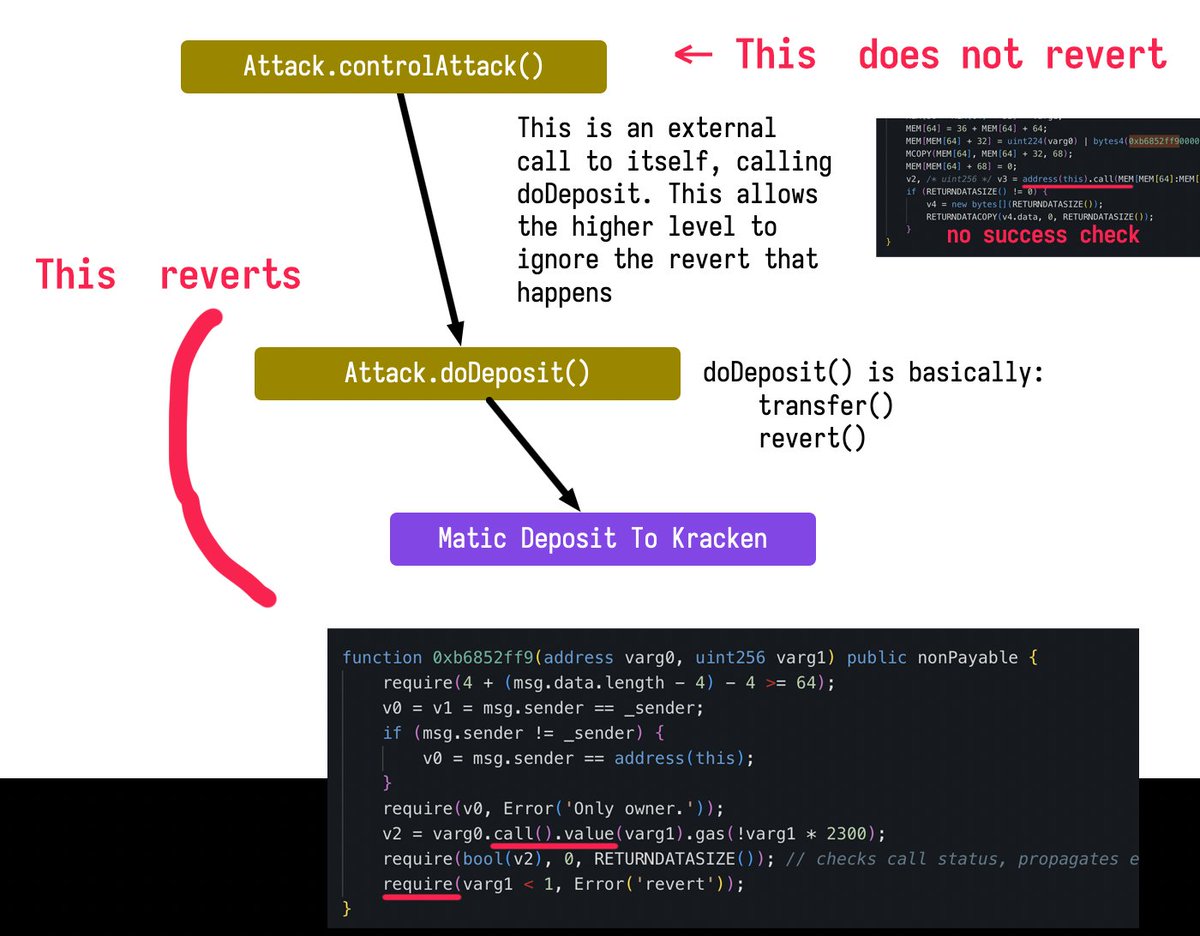
 At this point we had a transaction trace with a transaction to the deposit contract, that was inside a successful transaction. And that's what Kracken was looking for.
At this point we had a transaction trace with a transaction to the deposit contract, that was inside a successful transaction. And that's what Kracken was looking for.
 The price oracle used took 11 different prices, and used the median price as the price oracle. However, 5 of these prices were spot prices and directly under the control of the attacker.
The price oracle used took 11 different prices, and used the median price as the price oracle. However, 5 of these prices were spot prices and directly under the control of the attacker.
 This same design should work for both exchange rate tokens with fixed amounts and for rebasing tokens with changing total supply.
This same design should work for both exchange rate tokens with fixed amounts and for rebasing tokens with changing total supply.
 A rounding donation attack requires the things:
A rounding donation attack requires the things:

 The bugged remove liquidity methods give the attacker execution, while the balances and total supply are in a partially updated state.
The bugged remove liquidity methods give the attacker execution, while the balances and total supply are in a partially updated state.
https://twitter.com/danielvf/status/1647291784848867330Secondly, after the attacker donated to the pool, the exchange rate was massively inflated. redeemUnderlying wrongly rounded down on the tokens to remove from the mini attack contract.

https://twitter.com/danielvf/status/1572963306725318657

 The attacks were designed to exploit this behavior by alternately acquiring and burning the token. These huge fees caused massive over-rebasing. In the end the attacker used the extra coins to run away with all the ETH in the coin's uniswap pool. 2/5
The attacks were designed to exploit this behavior by alternately acquiring and burning the token. These huge fees caused massive over-rebasing. In the end the attacker used the extra coins to run away with all the ETH in the coin's uniswap pool. 2/5 

 The attacker forgot to code any way collect the funds after stealing them, so the funds were locked in the attack contract.
The attacker forgot to code any way collect the funds after stealing them, so the funds were locked in the attack contract.
 USDS has at least three different accounting systems, two separate auto-migration systems, and all share the same variables, just interpret their meaning differently. Thus, all account variables have to be updated together in order to accurately calculate a user's balance.
USDS has at least three different accounting systems, two separate auto-migration systems, and all share the same variables, just interpret their meaning differently. Thus, all account variables have to be updated together in order to accurately calculate a user's balance.
 The EFLeverVault handles withdraws by making a flash loan to itself for that amount, when it receives the flash loan, it withdraws that amount of funds, and leaves it in eth on the contract. After the flash loan is over, the contracts sends all ETH on the contract to user. 2/4
The EFLeverVault handles withdraws by making a flash loan to itself for that amount, when it receives the flash loan, it withdraws that amount of funds, and leaves it in eth on the contract. After the flash loan is over, the contracts sends all ETH on the contract to user. 2/4

 The weekend after I found the config issue, I fired up google's bigtable ethereum database and searched the last 400 days for contracts that had granted the timelock admin power, never revoked it, and had at least one timelock execution. Same query on Dune for Poly, BSC. 2/18
The weekend after I found the config issue, I fired up google's bigtable ethereum database and searched the last 400 days for contracts that had granted the timelock admin power, never revoked it, and had at least one timelock execution. Same query on Dune for Poly, BSC. 2/18


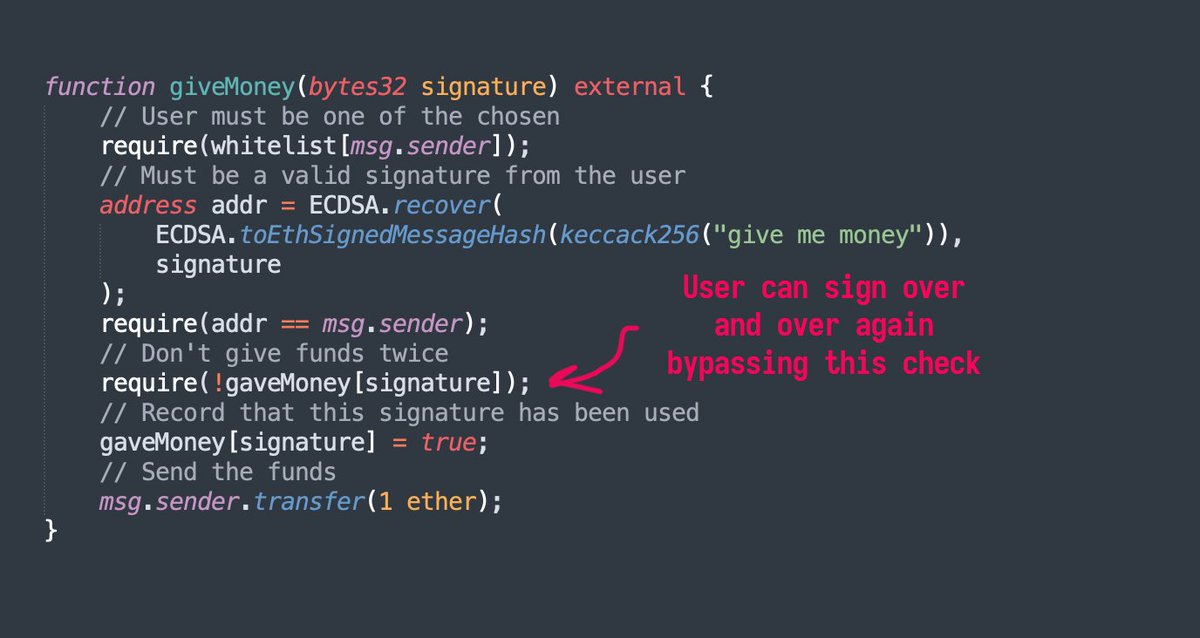
 In the above case, the user can keep calling `giveMoney` with a new signature each time and drain the contract.
In the above case, the user can keep calling `giveMoney` with a new signature each time and drain the contract.
 @paradigm_ctf The signature "checker" allows calls to other contracts, and sends the signature to it, then checks the response.
@paradigm_ctf The signature "checker" allows calls to other contracts, and sends the signature to it, then checks the response.