How to get URL link on X (Twitter) App


https://twitter.com/zachfb/status/1296838707849375745
 G-forces
G-forces


https://twitter.com/netspooky/status/1289606589121359872This isn’t as straight forward as it may seem.

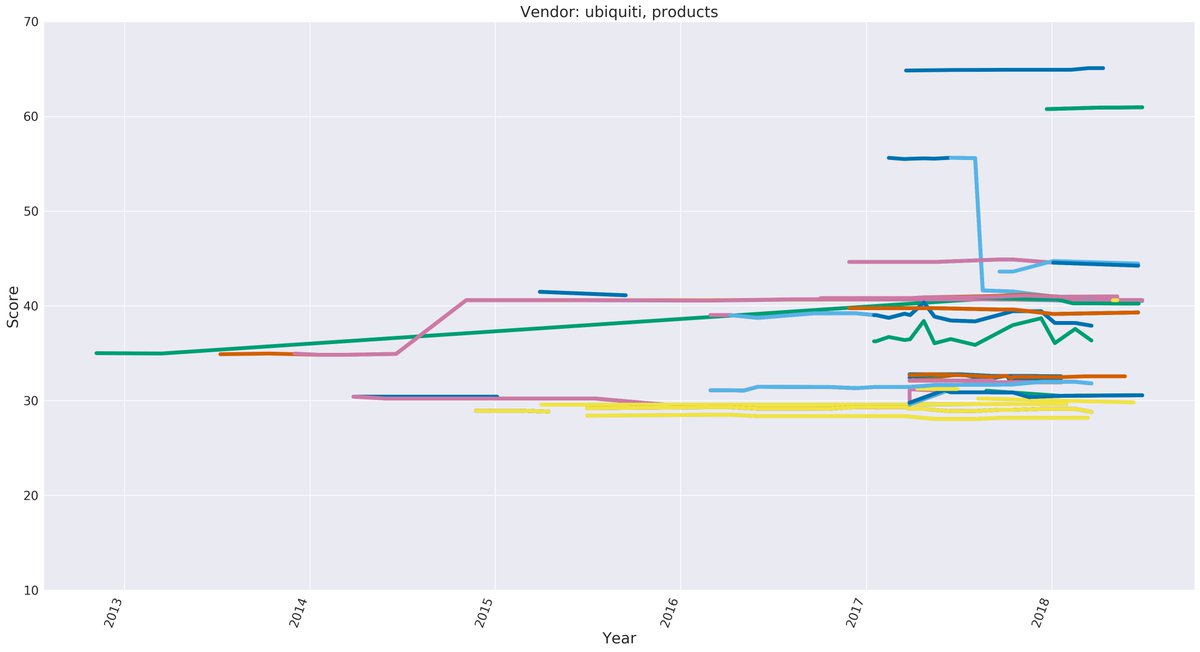
https://twitter.com/largecardinal/status/1274433398141042688Left to their own accord vendors of embedded systems are not demonstrating that they improve basic security hygiene in their products.
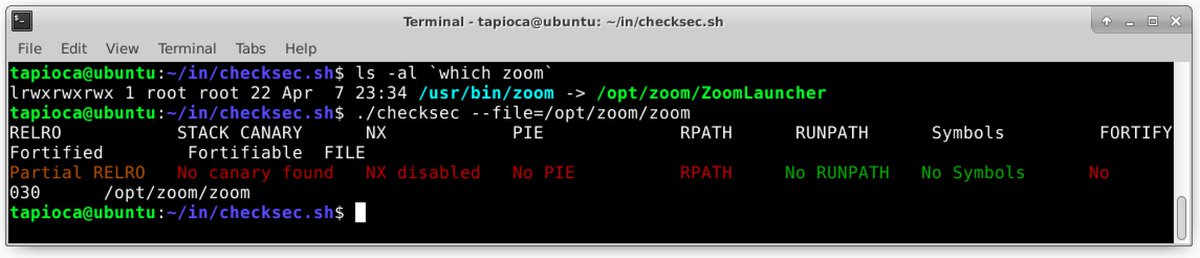

https://twitter.com/vmyths/status/1234003592069165056My name, Peiter Zatko, was a closely held secret both in the hacker community *and* the government.


https://twitter.com/thegrugq/status/1196792443447889921It was an OpenBSD system.

https://twitter.com/DethVeggie/status/1165684033092825088I should have been a bit more specific.


https://twitter.com/billstewart415/status/1154110139127009280Might do the thread later. It gets a bit ‘blue’.

 I dislike flying, so we rented a Dodge Ram 3500 15 passenger van to drive down to the US Senate.
I dislike flying, so we rented a Dodge Ram 3500 15 passenger van to drive down to the US Senate.


https://twitter.com/leakissner/status/1066761697254289408The old certificate needs to be revoked.
https://twitter.com/ericgeller/status/1049736259797770240to the public Internet, and found by scanning the IP range of the sub-contractor who did the work.

