
Co-Founder @MyHackerHouse 💾 | Cybersecurity & Web3 🌐 | Author of Hands-on Hacking (ISBN 9781119561453) 📖 | Offensive Lua 💻 | ✝️
3 subscribers
How to get URL link on X (Twitter) App


https://twitter.com/SkyNews/status/1898024629148561660



 When police raided the hotel as part of an operation, codenamed Skirp, they found it packed with technical equipment including 495 SIM cards, 221 mobile phones, 258 hard drives, 55 visual recording devices, 33 audio devices, 16 radios and 11 drones.
When police raided the hotel as part of an operation, codenamed Skirp, they found it packed with technical equipment including 495 SIM cards, 221 mobile phones, 258 hard drives, 55 visual recording devices, 33 audio devices, 16 radios and 11 drones.

 That eBay seller must have gotten his hands on some liquidated government-backed monitoring equipment. This is old equipment but a bargain at $600 - frequency counter, AOR wide-band receiver and numerous antennas for wireless signal detection and monitoring. Used to cost $1000's
That eBay seller must have gotten his hands on some liquidated government-backed monitoring equipment. This is old equipment but a bargain at $600 - frequency counter, AOR wide-band receiver and numerous antennas for wireless signal detection and monitoring. Used to cost $1000's 



 When generating "secure random" passwords in "SecretKeeper", it's important to always seed random number generator qsrand() with the current time. That way you can easily recover your passwords for sensitive Russian environments in case you were ever logged out of them....
When generating "secure random" passwords in "SecretKeeper", it's important to always seed random number generator qsrand() with the current time. That way you can easily recover your passwords for sensitive Russian environments in case you were ever logged out of them.... 



 This isn't the only bug of course, it's not possible on Linux to read the environment of a root owned process but as systemd creates a service in the system slice, you can query D-BUS and learn sensitive information passed to the process env, such as API keys or other secrets.
This isn't the only bug of course, it's not possible on Linux to read the environment of a root owned process but as systemd creates a service in the system slice, you can query D-BUS and learn sensitive information passed to the process env, such as API keys or other secrets.


https://twitter.com/passthehashbrwn/status/1740367435264627128I do not consider GCHQ or NSA TAO as APT in the traditional sense, they are vastly superior threat when compared to contractor hired by say the FSB to steal western secrets through drive-by downloads. There is cross-over but one is a wide industry threat, the other very specific.




 This shows the complete workflow that an analyst would use when creating malware at the CIA using Marble for string obfuscation. An attacker could essentially now follow leaked wiki instructions to obfuscate their strings in runtimes they create. More: wikileaks.org/ciav7p1/cms/pa…
This shows the complete workflow that an analyst would use when creating malware at the CIA using Marble for string obfuscation. An attacker could essentially now follow leaked wiki instructions to obfuscate their strings in runtimes they create. More: wikileaks.org/ciav7p1/cms/pa…
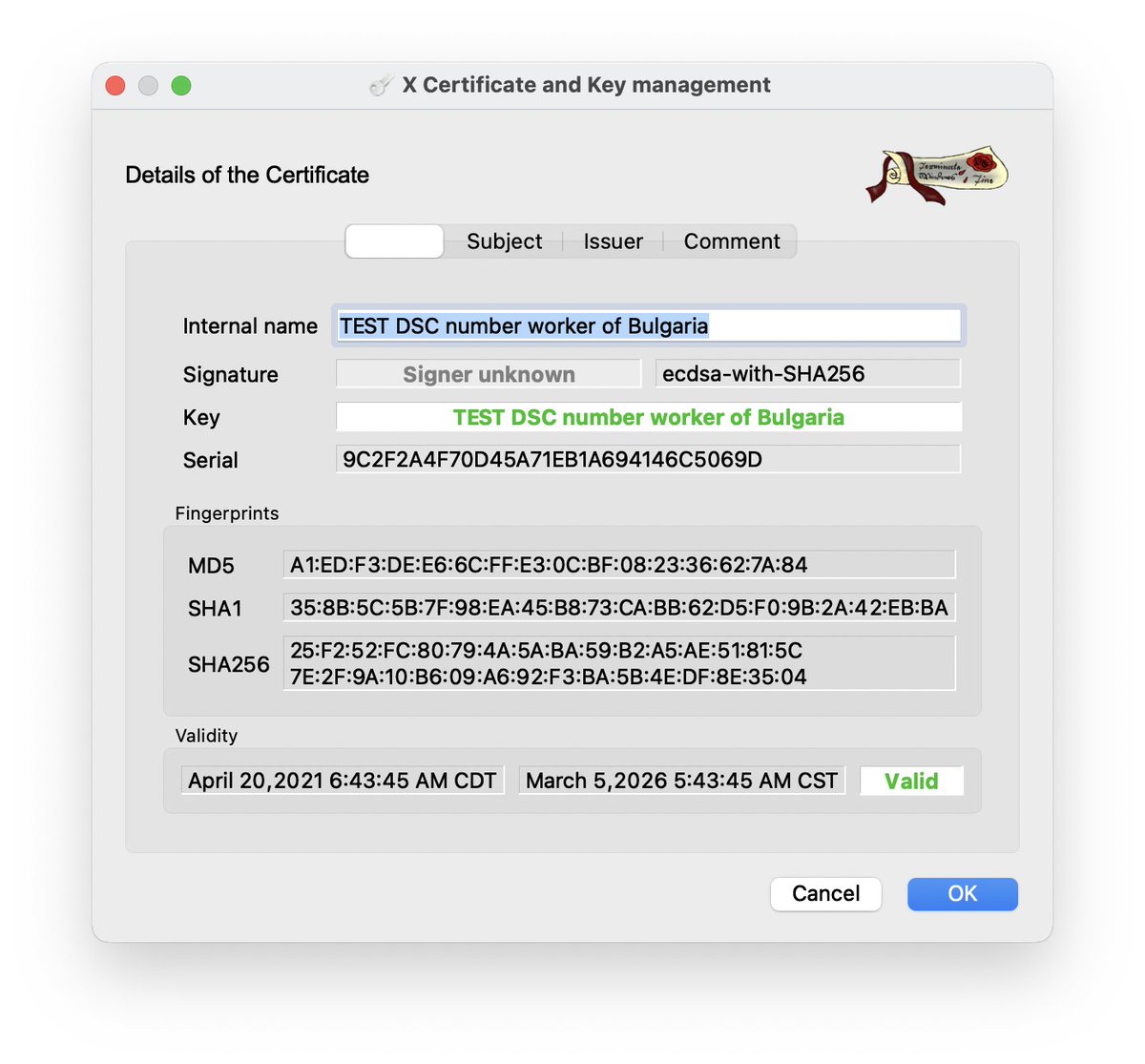

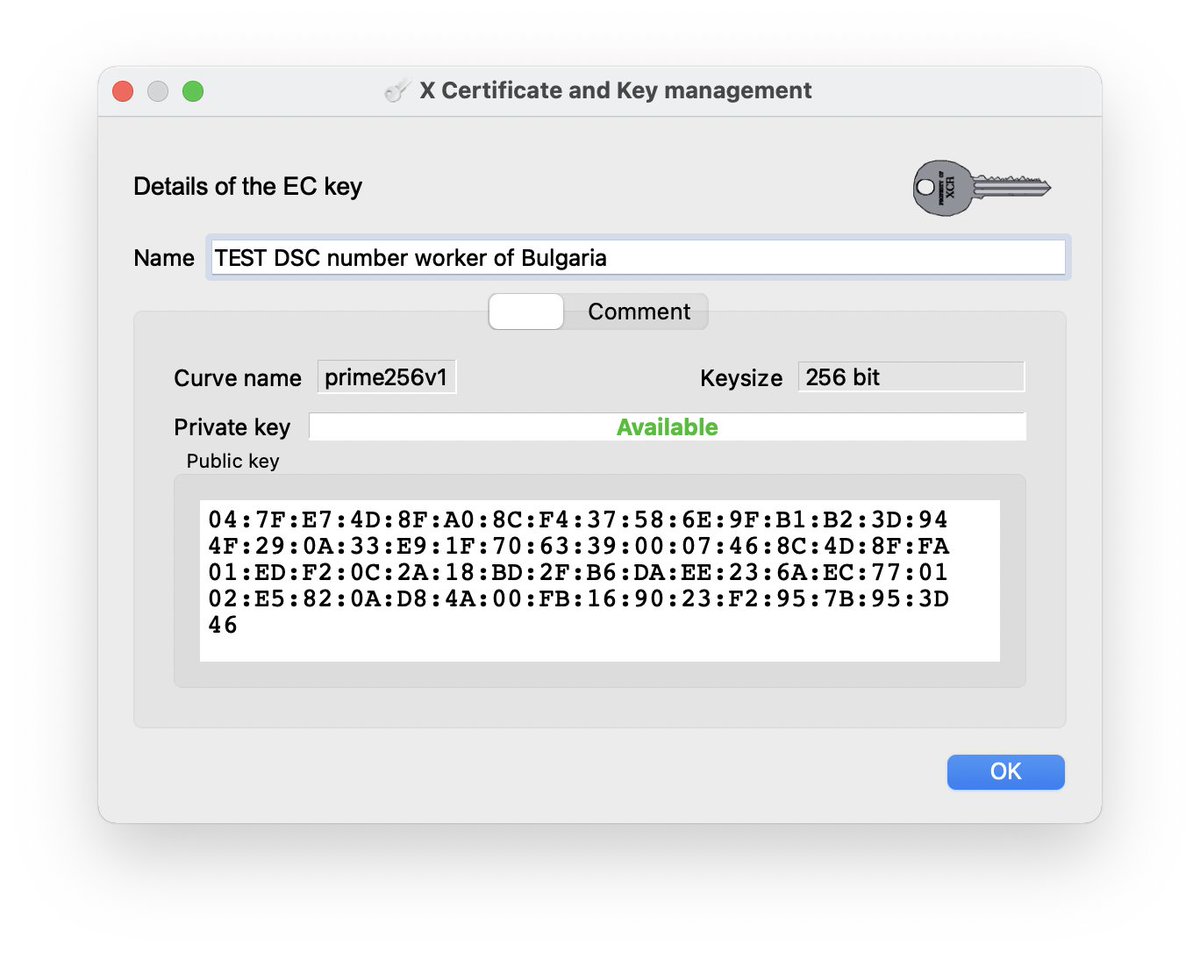 The above private key could be used to authenticate to the "on-boarding gateway" and falsify health records as authentic & valid from Bulgaria, additionally as it allowed authentication it could've been used to exploit Log4Shell (post-authentication) which was patched last year.
The above private key could be used to authenticate to the "on-boarding gateway" and falsify health records as authentic & valid from Bulgaria, additionally as it allowed authentication it could've been used to exploit Log4Shell (post-authentication) which was patched last year.

https://twitter.com/AmauryBucco/status/1608931645587087360It's so beautiful, power modules on top, fans for cooling, what look like modular radio blocks, amp, filter, SDR radio and the icing on the cake is the "decoy" antenna system made to look like a hotspot. Whatever they are hacking with this, someone spent money to build it.



 "clandestine" operations....
"clandestine" operations.... 