
Security consultant and investigative journalist. I am not a lawyer and this is not legal advice. 🇺🇸 🗽
16 subscribers
How to get URL link on X (Twitter) App

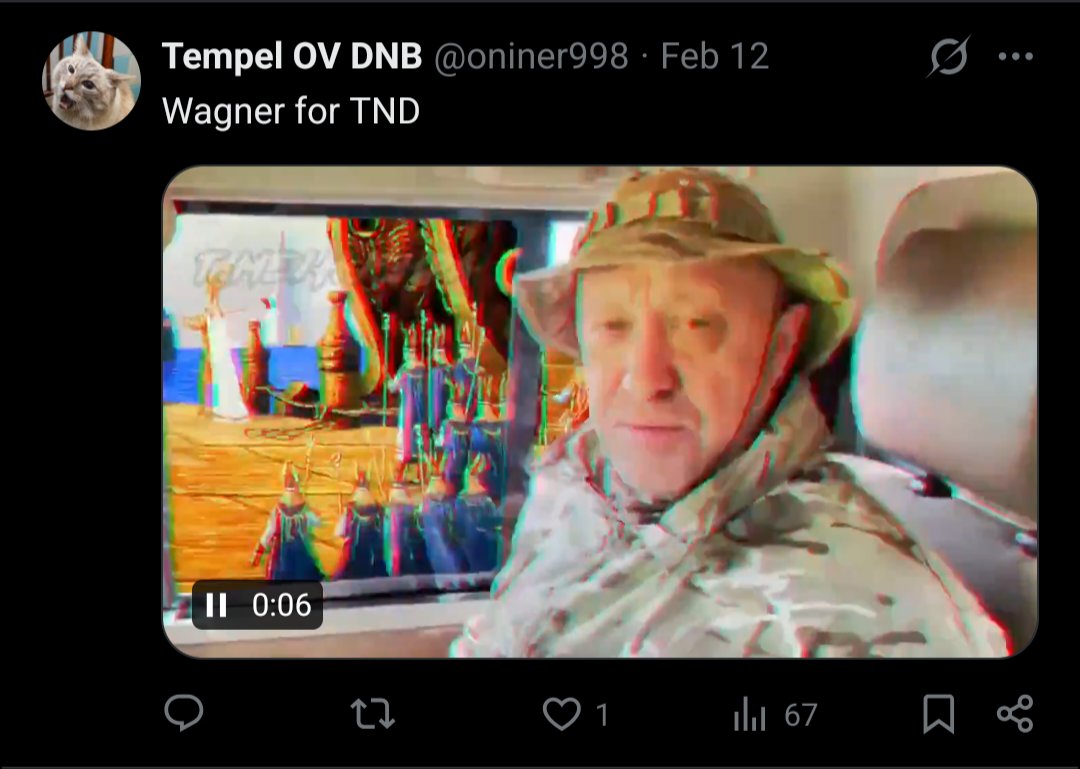
https://twitter.com/stevanzetti/status/2023056154226782277
 They also appear to have a woman deployed to perform narrative control on this topic. The goal is to ensure the public is not aware of the relationship between Russia and the child abuse conducted from afar.
They also appear to have a woman deployed to perform narrative control on this topic. The goal is to ensure the public is not aware of the relationship between Russia and the child abuse conducted from afar.
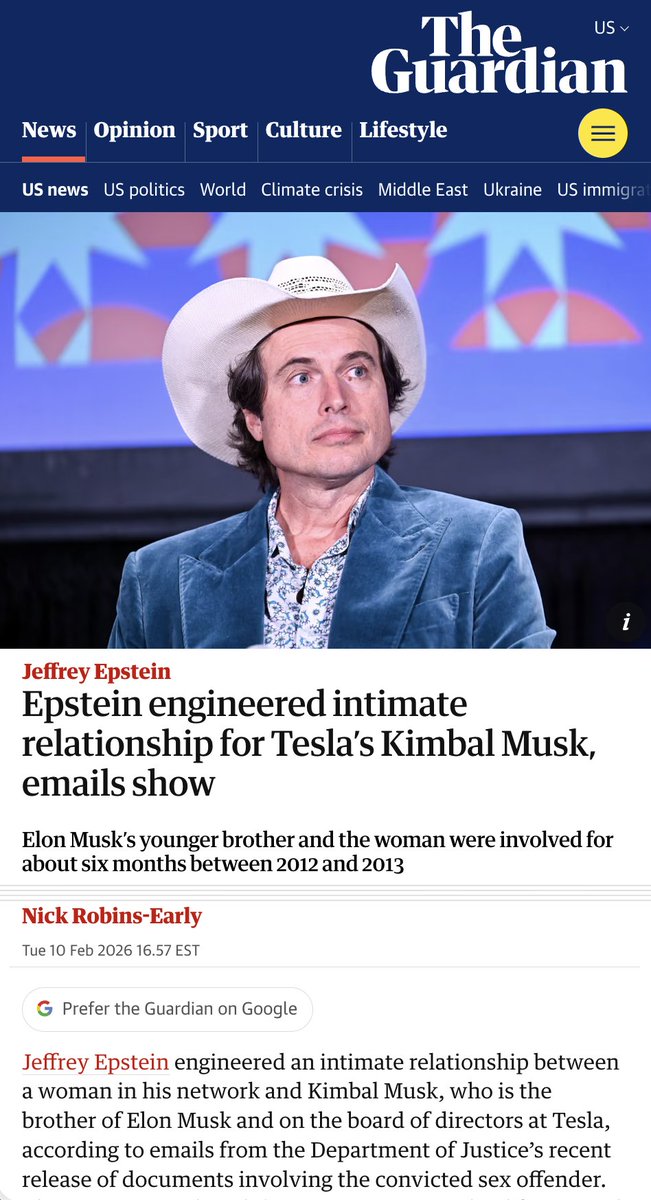
https://twitter.com/HackingButLegal/status/2021705769570144748
 2/🚩 The behavior described looks very similar to how powerful people are identified, studied, and slowly drawn into compromising relationships—
2/🚩 The behavior described looks very similar to how powerful people are identified, studied, and slowly drawn into compromising relationships— https://twitter.com/TheMaineWonk/status/2021549844632842705Reopening the airspace was the START of resolving the travel backlog. People were having trouble buying flights and the airports were packed.
https://twitter.com/phildstewart/status/20191932010648334872/ Between Feb 1–4, Gabbard told Congress her Georgia role falls under ODNI's election security authority and is tied to a long running assessment of electronic voting systems.
 Keith Ingersoll is an associate of Matt Gaetz.
Keith Ingersoll is an associate of Matt Gaetz.https://twitter.com/HackingButLegal/status/19961211680429795522/ Bc they’re habituated to community violence, not lone gunmen in mass shooter scenarios, they arrived fast yet unequipped, then failed to properly assess/secure the scene and find the gunman. The key witness who saw the shooter exited to seek a paramedic to help his dying son.
https://twitter.com/doggintrump/status/19935391766215967112/ The outfit immediately drew comparisons to 17th-century Puritan dress, specifically the clothing women may have worn at the mythologized "First Thanksgiving" in 1621. Media called it "full cosplay" and "pilgrim-core." But dismissing it as a fashion miss understates the matter
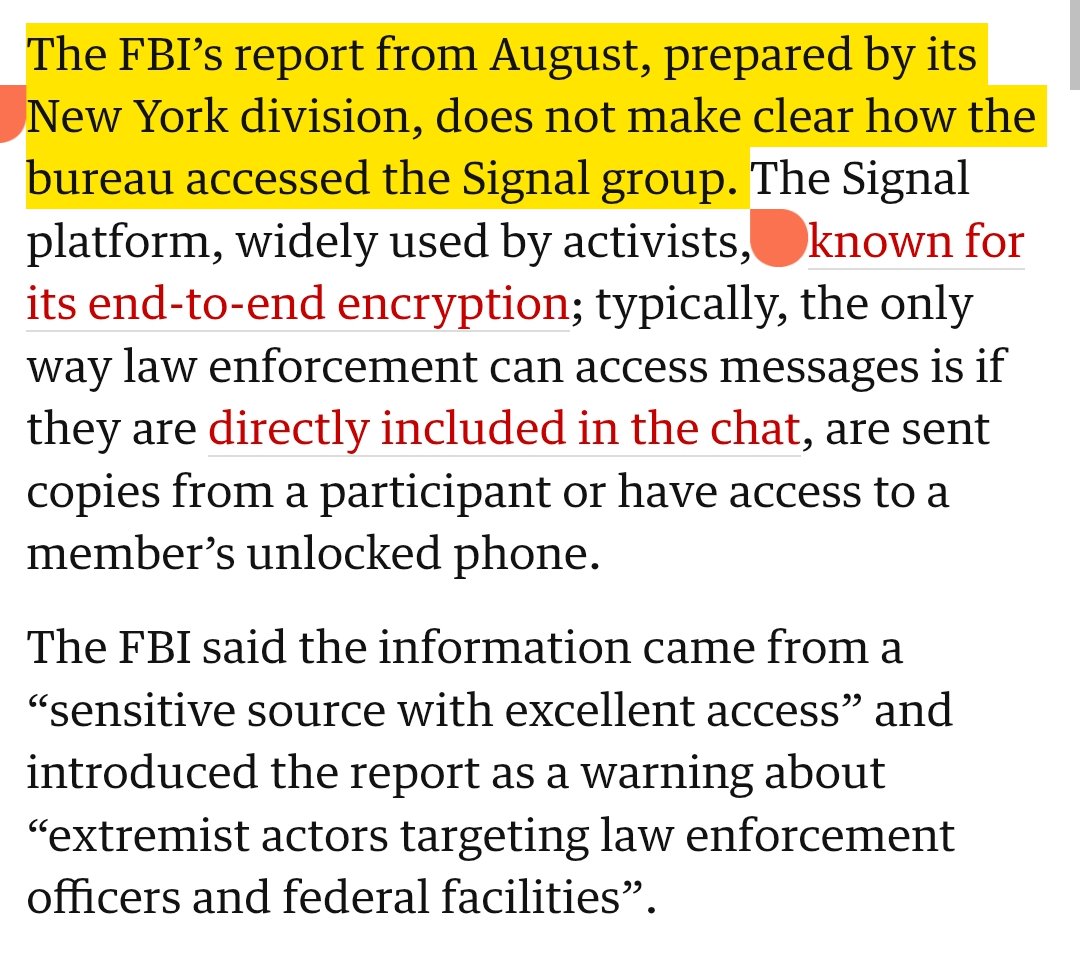
https://twitter.com/ReichlinMelnick/status/1991853132960399480
 2/ They may try to use people of color to lure you in, or use some other commonality between you and their surveillance persona. They may appear on the surface to be genuine activists. Ask a lot of questions, act legally in your dealings, and follow your gut.
2/ They may try to use people of color to lure you in, or use some other commonality between you and their surveillance persona. They may appear on the surface to be genuine activists. Ask a lot of questions, act legally in your dealings, and follow your gut.
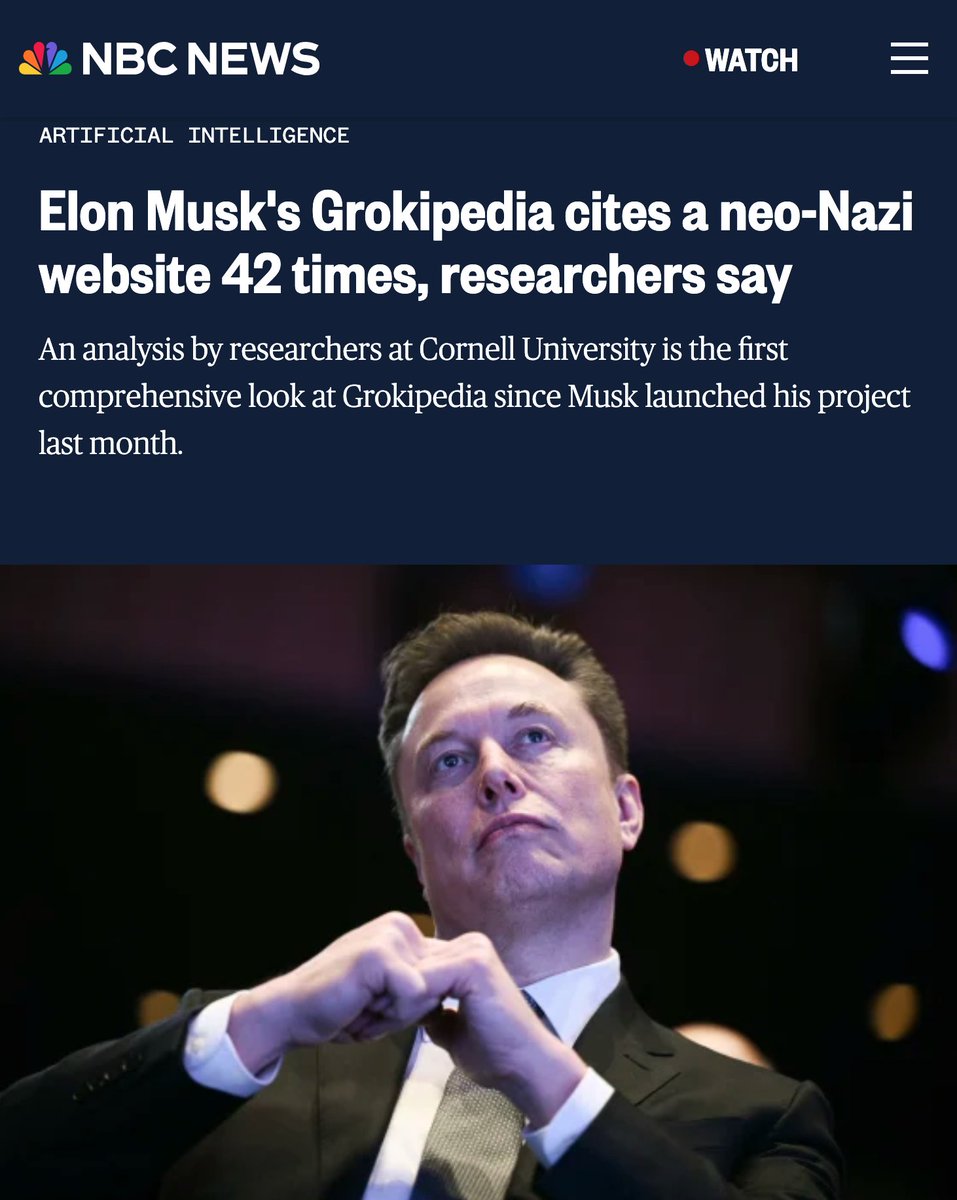
 2/ Their analysis of over 880K articles revealed 12,522 citations to sources deemed low-credibility by academic research (3x higher than Wikipedia). They found ~5.5% of Grokipedia articles have citations to sources strictly blacklisted by the Wiki community for unreliability.
2/ Their analysis of over 880K articles revealed 12,522 citations to sources deemed low-credibility by academic research (3x higher than Wikipedia). They found ~5.5% of Grokipedia articles have citations to sources strictly blacklisted by the Wiki community for unreliability. 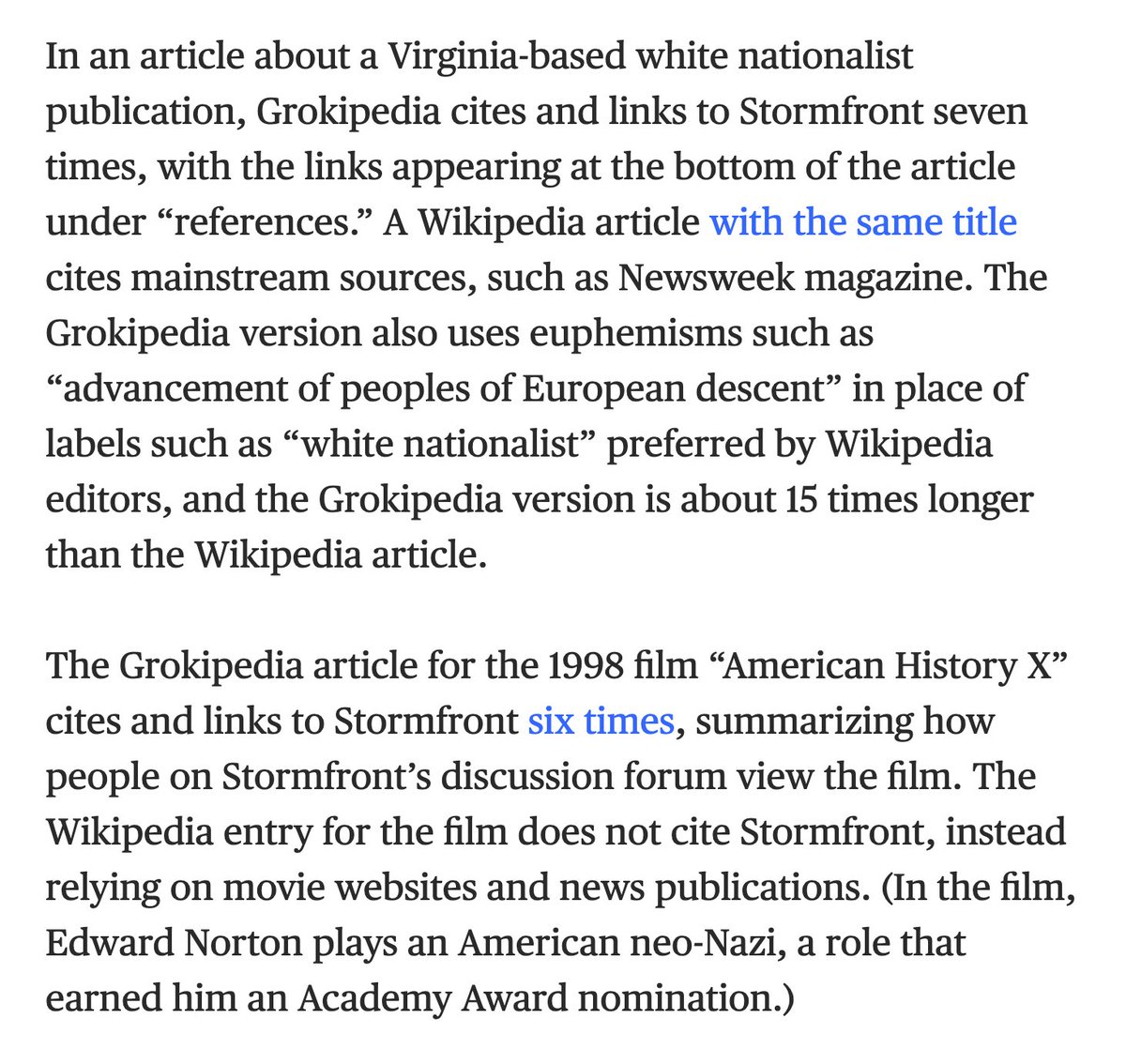
https://twitter.com/CJR/status/1991509199445193018Legacy reporters ignored while the new MAGA-friendly press corps boasts of a direct hotline to officials. Access is now a reward for loyalty. The govt has created an information asymmetry where approved narratives get speed and access; critical inquiry gets the silent treatment.