
Dad/@SlowMist_Team CISO/#Web3 Security Researcher/RedTeam/Pentester.
Do it #bitcoin
How to get URL link on X (Twitter) App

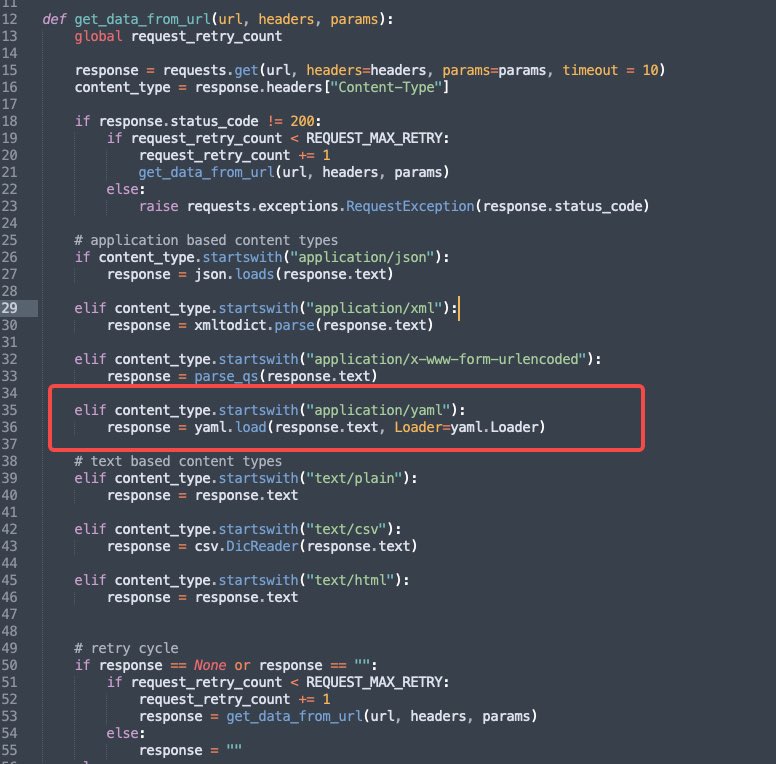
 the Lazarus hackers first found the targeted employees through social engineering, added private GitHub repository access to the victims or victimized employees through live chat tools, and tricked the users into running the code that contained the backdoor.
the Lazarus hackers first found the targeted employees through social engineering, added private GitHub repository access to the victims or victimized employees through live chat tools, and tricked the users into running the code that contained the backdoor.

https://twitter.com/michaelwong123/status/1659091817206300673总之一句话,硬件钱包一定要从 官方渠道!官方渠道!官方渠道 (重要的事情说三遍) 购买!👈







https://twitter.com/vxunderground/status/1615613680460402688Rhadamanthys is another group using Google Ad for phishing after Redline, also targeting the cryptocurrency user community.




 @SlowMist_Team @evilcos
@SlowMist_Team @evilcos 
https://twitter.com/keenz_eth/status/15661063201549393921.如果你在币圈玩,首先建议基础硬件上,推荐iphone,不推荐安卓手机,苹果手机的权限控制更严格;如果你是电脑用的多,推荐Mac,不推荐windows电脑,因为针对windows的各种木马病毒已经太成熟了。
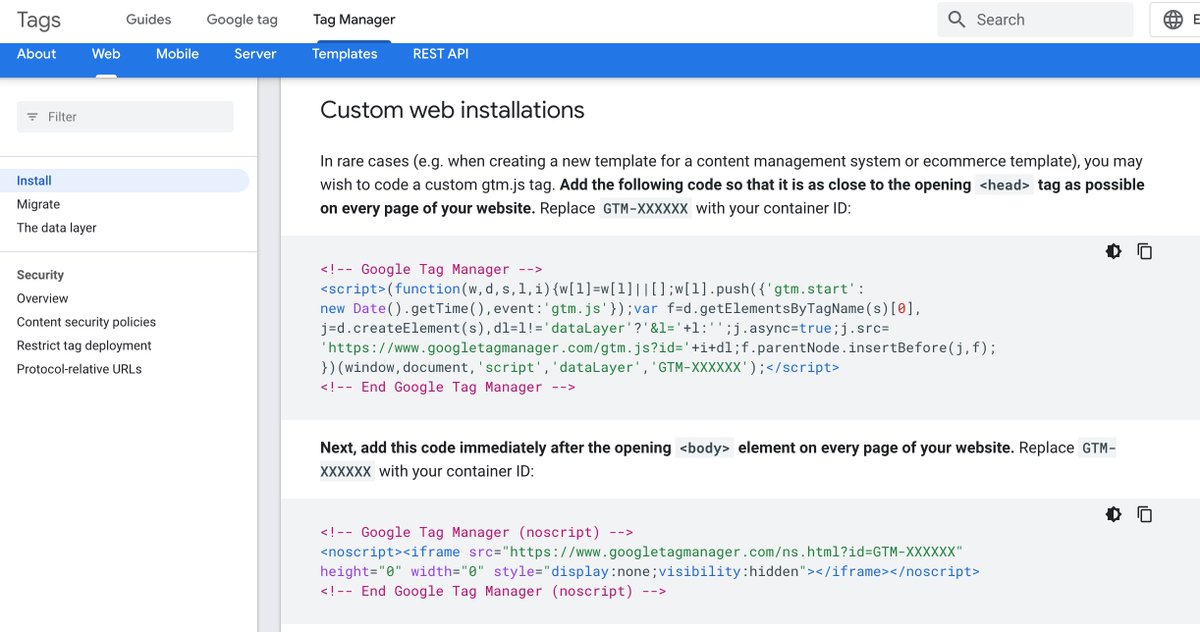
https://twitter.com/IM_23pds/status/1565500524807344129@Foresight_News @evilcos @sniko_

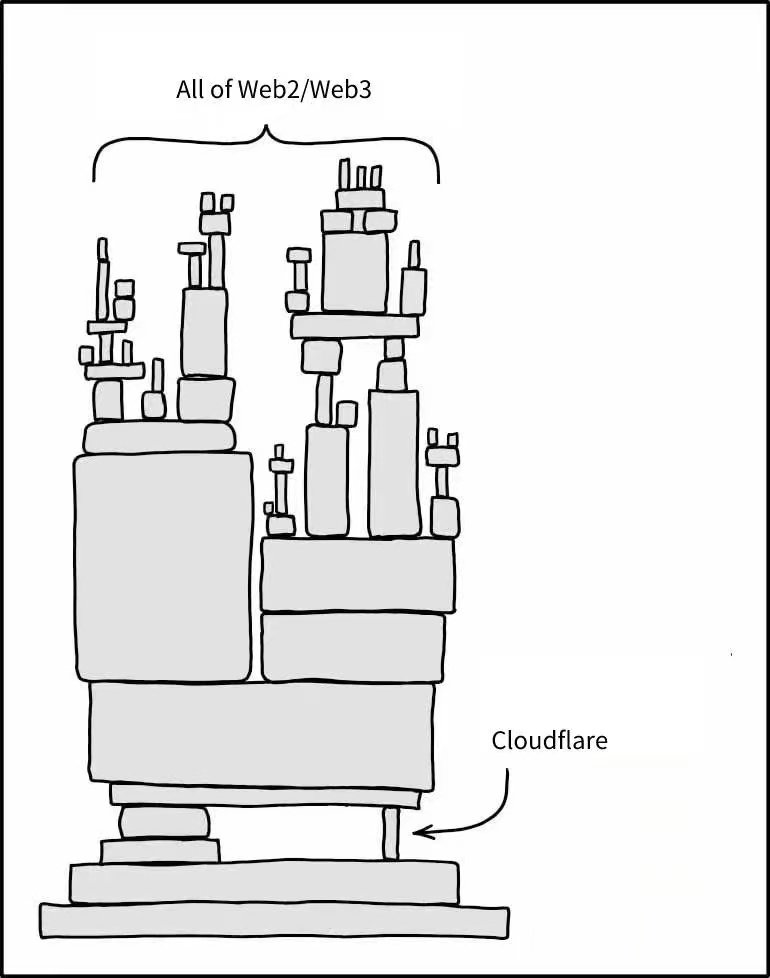
 @SlowMist_Team @0xfoobar @officer_cia @sniko_ @Mudit__Gupta 1/web3 still needs a domain name, which is the entrance to the Internet. And the domain name needs to be registered with the domain name service provider, there is a risk here: the domain name service provider may be attacked by social engineering
@SlowMist_Team @0xfoobar @officer_cia @sniko_ @Mudit__Gupta 1/web3 still needs a domain name, which is the entrance to the Internet. And the domain name needs to be registered with the domain name service provider, there is a risk here: the domain name service provider may be attacked by social engineering