Bredt Family Professor of Computer Science and Engineering, @UMich: Security and privacy, election security, and Internet freedom. Co-founded @LetsEncrypt
4 subscribers
How to get URL link on X (Twitter) App


https://twitter.com/kevincollier/status/1672281225933860874
 (This looks to me like a botched website redesign, rather than a hack, but still, lol. If Voatz is careless enough to flip its core talking points, why should anyone trust them with their votes?)
(This looks to me like a botched website redesign, rather than a hack, but still, lol. If Voatz is careless enough to flip its core talking points, why should anyone trust them with their votes?)



 2/ OmniBallot is a web-based platform that can be used in three ways:
2/ OmniBallot is a web-based platform that can be used in three ways: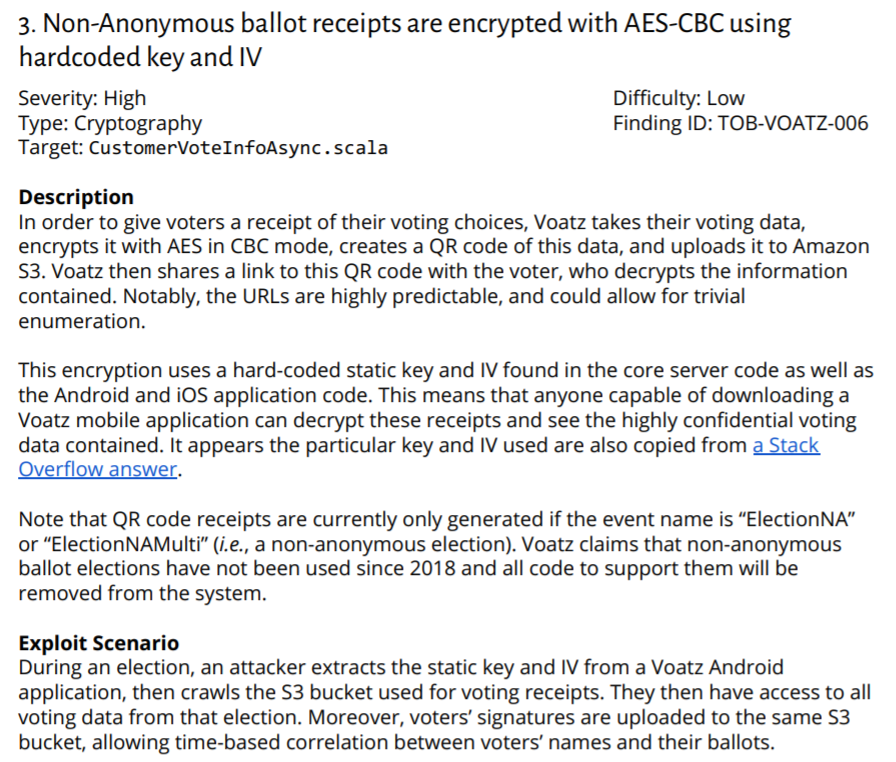
https://twitter.com/trailofbits/status/12384327883884789792/ Notably, this time @Voatz commissioned the analysis itself, as @rachelegoodman1 and I recently advocated slate.com/technology/202….