
Director of Intel at @redcanary. SANS Certified Instructor for FOR578: CTI. Senior Fellow at @CyberStatecraft. She/her. Mastodon: @likethecoins@infosec.exchange
How to get URL link on X (Twitter) App


 Let's talk detection opportunities! Here a couple that stand out for me in their excellent TTPs table... reGeorg appears to be open source, so that's a good opportunity to dive into that and figure out how you'd detect it github.com/xl7dev/WebShel…
Let's talk detection opportunities! Here a couple that stand out for me in their excellent TTPs table... reGeorg appears to be open source, so that's a good opportunity to dive into that and figure out how you'd detect it github.com/xl7dev/WebShel… 
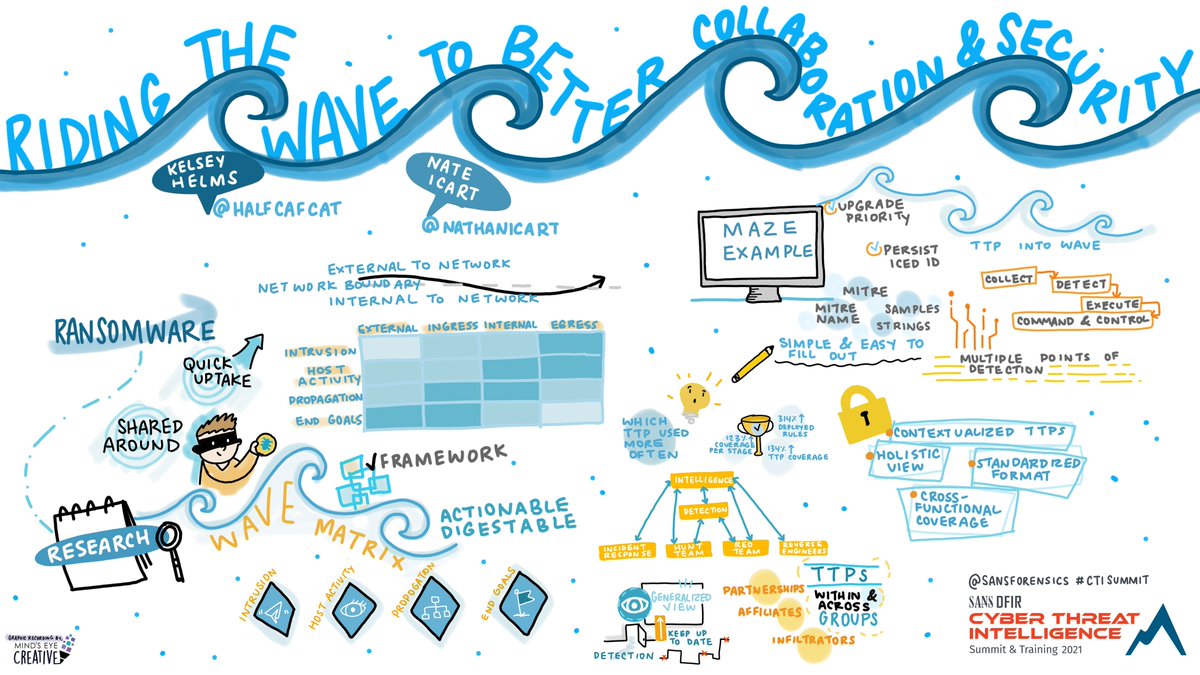
 #CTISummit
#CTISummit 

 Why do I talk about naming things so much? This is why! CrowdStrike DOES NOT CALL THE ADVERSARY A BEAR. They call this an activity cluster named StellarParticle. This is important. It's also important to note that this is a different name than Solorigate...
Why do I talk about naming things so much? This is why! CrowdStrike DOES NOT CALL THE ADVERSARY A BEAR. They call this an activity cluster named StellarParticle. This is important. It's also important to note that this is a different name than Solorigate... 

 I've been on a "drawer" kick, so I ordered another set of small drawers that I previously got to organize hardware/screws. Viola! So much better! I like to use dry erase markers first, then live with it for a bit before making permanent labels. Oversized stickers go on top.
I've been on a "drawer" kick, so I ordered another set of small drawers that I previously got to organize hardware/screws. Viola! So much better! I like to use dry erase markers first, then live with it for a bit before making permanent labels. Oversized stickers go on top. 

 I think a lot of this we already knew, but lmk if there are nuggets in here that popped out.
I think a lot of this we already knew, but lmk if there are nuggets in here that popped out. 

 .@Robert_Lipovsky kicking off with something I believe as well...crimeware is a greater threat to most orgs than state-sponsored threats. Even this week!
.@Robert_Lipovsky kicking off with something I believe as well...crimeware is a greater threat to most orgs than state-sponsored threats. Even this week!

 Tracking Time to RYUK! This is a good metric to track as much as you can.
Tracking Time to RYUK! This is a good metric to track as much as you can. 

 They also mentioned other group aliases. A reminder to consider @RobertMLee's valid points about how group names can't be exact overlaps due to different visibility and analysis methodology between companies (sans.org/webcasts/threa…). (2/n)
They also mentioned other group aliases. A reminder to consider @RobertMLee's valid points about how group names can't be exact overlaps due to different visibility and analysis methodology between companies (sans.org/webcasts/threa…). (2/n) 