
Official MHT Twitter account.
Check out ID Ransomware (created by @demonslay335).
More photos & gifs, less malware.
4 subscribers
How to get URL link on X (Twitter) App


 "using Russian-language elements to obscure its origin or intent"
"using Russian-language elements to obscure its origin or intent"

 So, the main leak site / blog of the LockBit ransomware gang is currently displaying this deface page. Same with all the mirrors of it.
So, the main leak site / blog of the LockBit ransomware gang is currently displaying this deface page. Same with all the mirrors of it. 
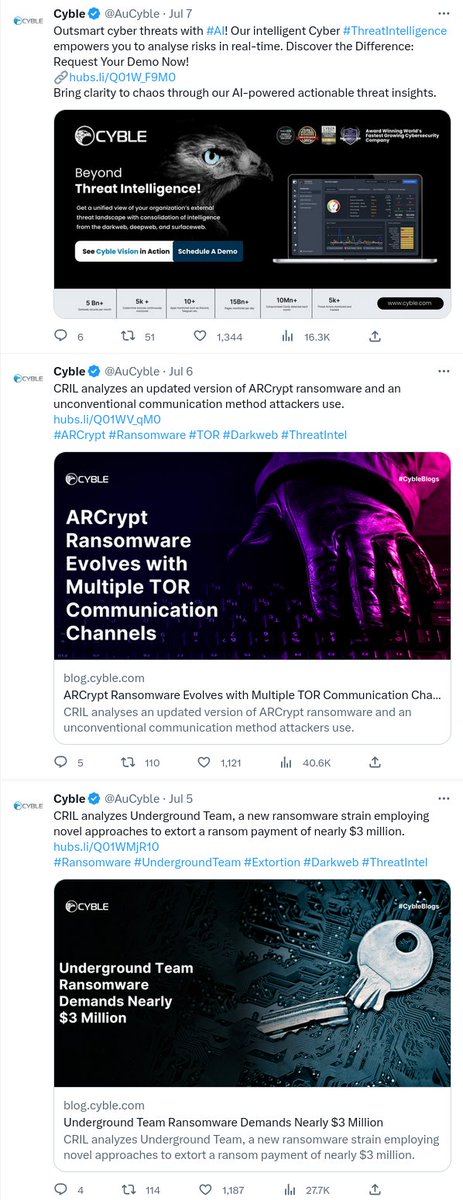



 What you think, @idclickthat @Iamdeadlyz @ULTRAFRAUD @JAMESWT_MHT (and everyone else I forgot that "likes" this company)?
What you think, @idclickthat @Iamdeadlyz @ULTRAFRAUD @JAMESWT_MHT (and everyone else I forgot that "likes" this company)?

 @elonmusk Can't even check if he tweeted anything about this shit as getting "429 Too Many Requests" response with "{ code: 88, message: "Rate limit exceeded." }" response content.
@elonmusk Can't even check if he tweeted anything about this shit as getting "429 Too Many Requests" response with "{ code: 88, message: "Rate limit exceeded." }" response content.




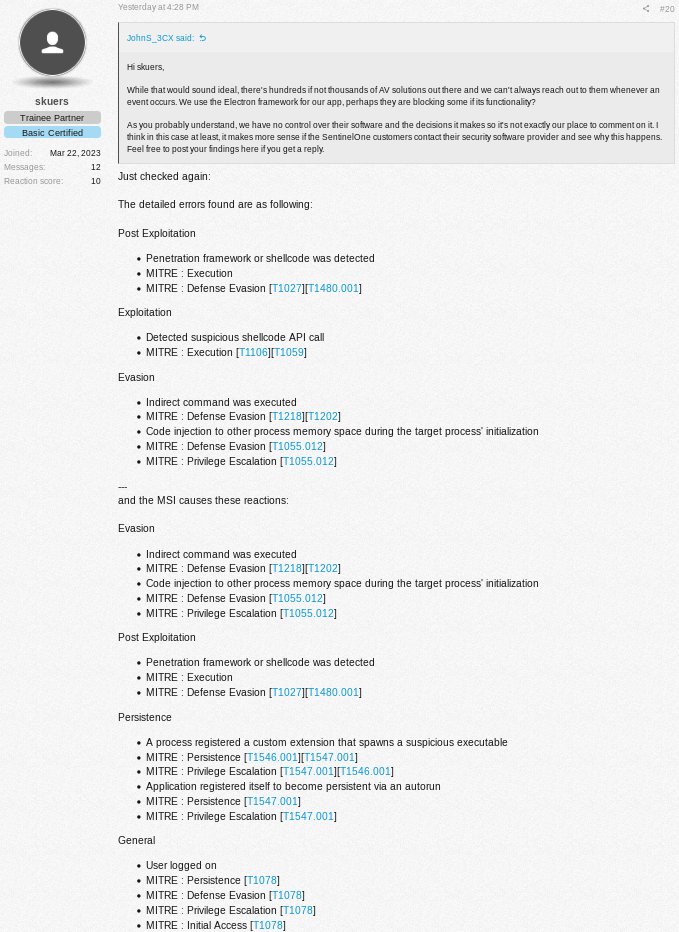 @cyb3rops Poor people/victims...
@cyb3rops Poor people/victims...

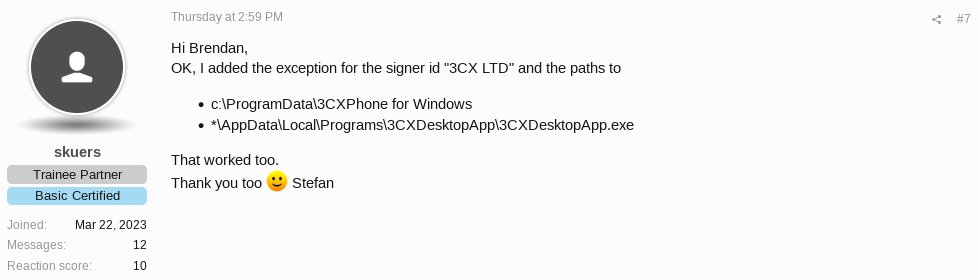






 In case anyone not knows her: she is doing lots mis/disinformation, spreading lies, etc.
In case anyone not knows her: she is doing lots mis/disinformation, spreading lies, etc.https://twitter.com/malwrhunterteam/status/1545723249690042368
https://twitter.com/malwrhunterteam/status/1555921621252284417"This is due to the fact that most of our developers and partners were born and grew up in the Soviet Union, the former largest country in the world, but now we are located in the Netherlands."

 The data storage site for old data (and the mirrors for that) are still working - but even the links in the header and footer (except the Twitter, obviously) are all too dead...
The data storage site for old data (and the mirrors for that) are still working - but even the links in the header and footer (except the Twitter, obviously) are all too dead...



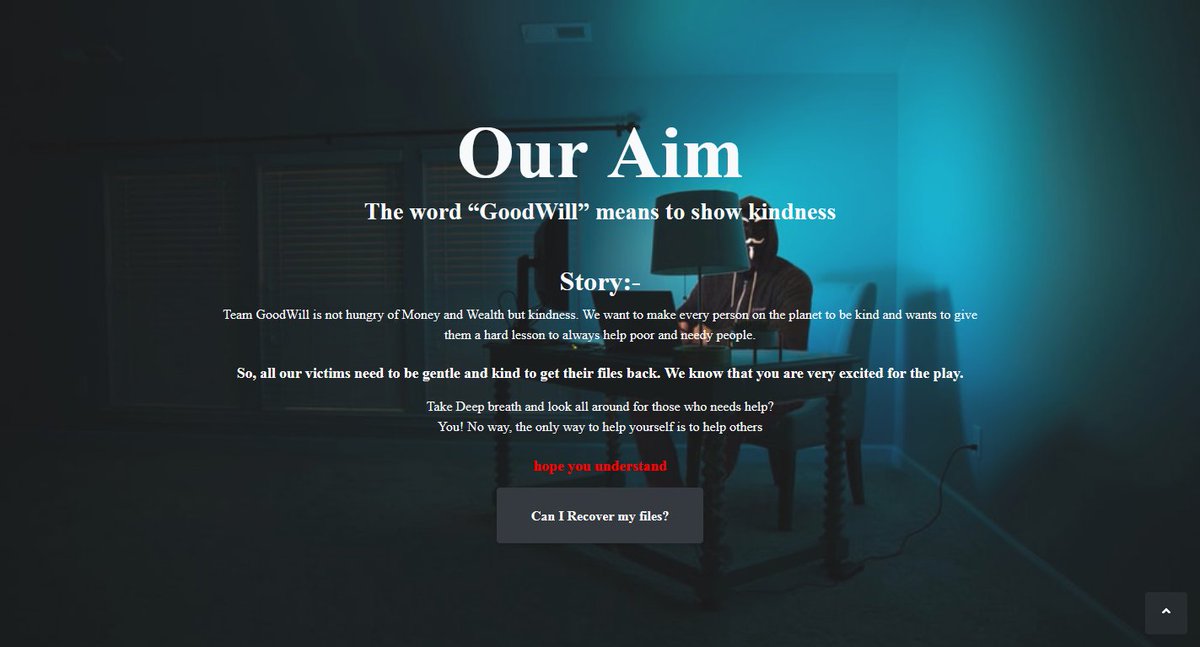
 "Team GoodWill is not hungry of Money and Wealth but kindness. We want to make every person on the planet to be kind and wants to give them a hard lesson to always help poor and needy people.
"Team GoodWill is not hungry of Money and Wealth but kindness. We want to make every person on the planet to be kind and wants to give them a hard lesson to always help poor and needy people.




https://twitter.com/ov3rflow1/status/1484968499688706048
 Other than the info it requires to user to enter, it collects so much info from the device... Crazy.
Other than the info it requires to user to enter, it collects so much info from the device... Crazy.



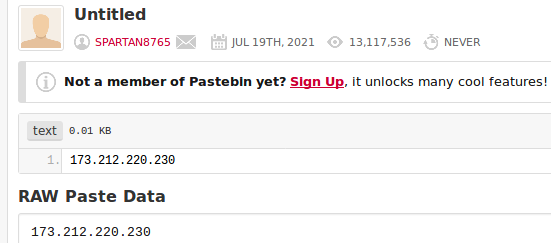
 Leaving the analysis for the experts (obviously b/c they are the experts & because I'm very busy), but let me quickly highlight something: the C2's IP is grabbed from https://pastebin[.]com/VfRCefzG - it was already accessed more than 13 million times!
Leaving the analysis for the experts (obviously b/c they are the experts & because I'm very busy), but let me quickly highlight something: the C2's IP is grabbed from https://pastebin[.]com/VfRCefzG - it was already accessed more than 13 million times!



 @GitHubSecurity Meanwhile I was looking at the samples @0x7fff9 just RT this:
@GitHubSecurity Meanwhile I was looking at the samples @0x7fff9 just RT this: https://twitter.com/impost0r_/status/1479600560240222208- so anyone is behind this also created looks a website too, not only the GitHub repo...