
Director, Incident Response @Databricks. Former @Mandiant / @Google Intel leader, IR Consultant, Security Researcher, Technical Intel Analyst, Endpoint TPM.
How to get URL link on X (Twitter) App

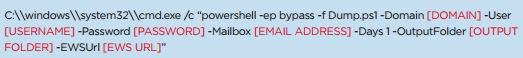
https://twitter.com/da_667/status/1028130149219356672A victim identifying a phishing doc or phishing backdoor doesn't necessarily mean the op is blown. In fact, it may give the victim a false confidence if they found the initial infection but didn't follow lateral movement. Same if an attacker loses a couple of implants out of many