Animal liberation activist & Reverse Engineer 🌟 Forbes 30 Under 30 •
Maintainer of Cutter and Rizin • Leading Research @ Check Point •
I don't eat animals.
How to get URL link on X (Twitter) App

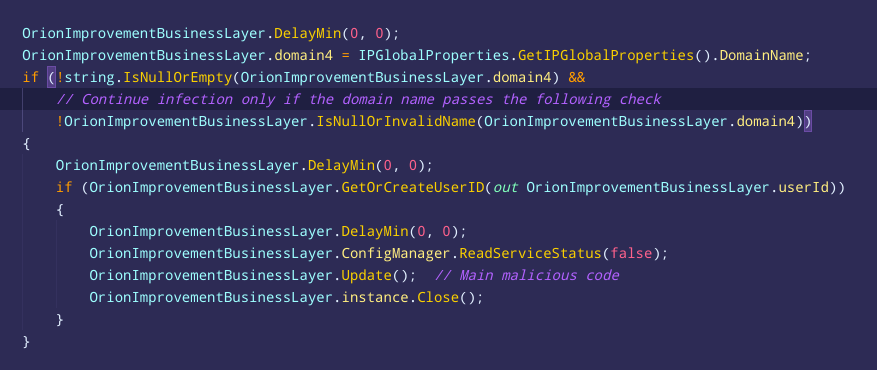
 When brute-forcing the FNV-1a hashes embedded in #SUNBURST, I noticed that some of the cracked strings look like domain names of #SolarWinds internal networks across the globe. If the domain of the infected computer ends with one of these names, the malware would not run >>
When brute-forcing the FNV-1a hashes embedded in #SUNBURST, I noticed that some of the cracked strings look like domain names of #SolarWinds internal networks across the globe. If the domain of the infected computer ends with one of these names, the malware would not run >> 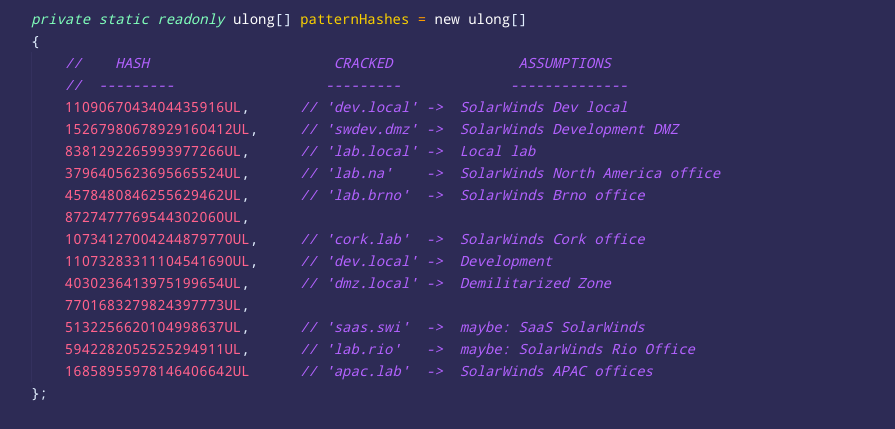

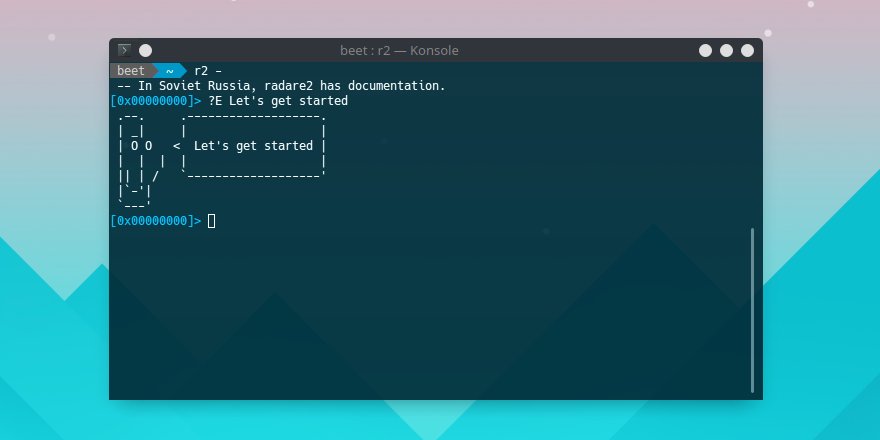
 First things first, some history. The radare2 project was created by @trufae in February of 2006 to provide a free and simple command-line hexadecimal editor. Starting from a one-man-show, radare2 nowadays gathered a huge community and a substantial number of contributors >>
First things first, some history. The radare2 project was created by @trufae in February of 2006 to provide a free and simple command-line hexadecimal editor. Starting from a one-man-show, radare2 nowadays gathered a huge community and a substantial number of contributors >>