
Author/Operator of @ScumBots. Blue Team by day, Blue Team by night. Opinions, typos, and bad grammar do not represent my employer. He/Him
How to get URL link on X (Twitter) App



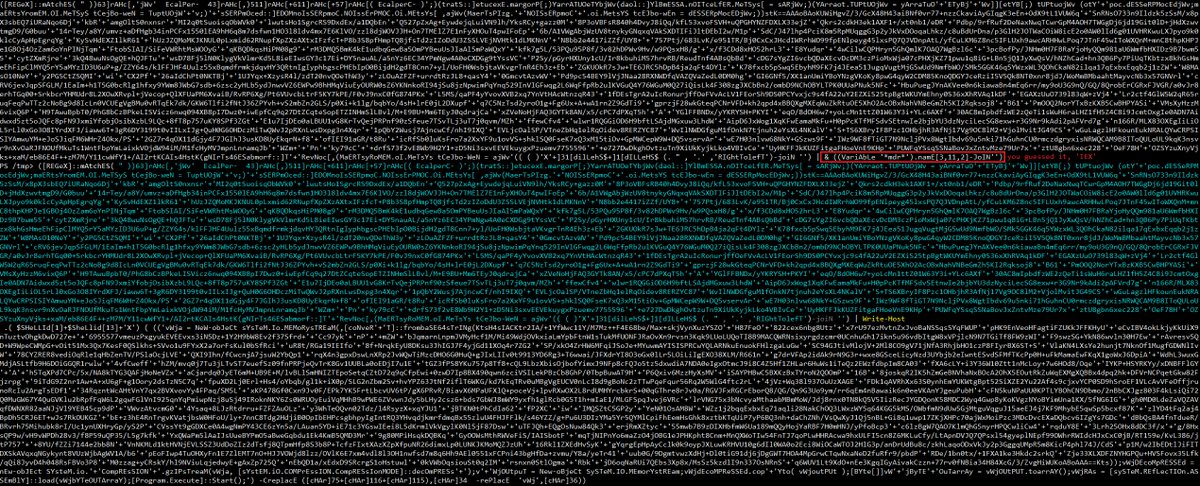
 Sure, we could walk through all of the string concatenation, bogon characters, base64, and compression. Or we could just make the code unpack itself, which is way easier. By replacing IEX (Invoke-Expression) with Write-Host, we can step through the obfuscation with minimal pain:
Sure, we could walk through all of the string concatenation, bogon characters, base64, and compression. Or we could just make the code unpack itself, which is way easier. By replacing IEX (Invoke-Expression) with Write-Host, we can step through the obfuscation with minimal pain: 



 The JavaScript decodes a blob of base64 data info a file and loads it in a document.body element (so to be viewed in a browser, the object is named "message.pdf" which is our first clue.
The JavaScript decodes a blob of base64 data info a file and loads it in a document.body element (so to be viewed in a browser, the object is named "message.pdf" which is our first clue. 

 The initial script has two lines: the first writes obfuscated code to the string variable0 $dz61UV and the second executes the contents of that string with Invoke-Expression after first reversing the order of bytes and stripping out unneeded spaces.
The initial script has two lines: the first writes obfuscated code to the string variable0 $dz61UV and the second executes the contents of that string with Invoke-Expression after first reversing the order of bytes and stripping out unneeded spaces. 

 Once we decode the base64 script from the macro, we can see that it further obfuscates its intention with more base64 encoding and gzip compression.
Once we decode the base64 script from the macro, we can see that it further obfuscates its intention with more base64 encoding and gzip compression. 




My first con of any kind was DC6 in 1998. At the time, I worked for a school, fixing Macs and LaserJets, resetting passwords, etc 2/
External Tweet loading...
If nothing shows, it may have been deleted
by @withzombies view original on Twitter