How to get URL link on X (Twitter) App

 First, what does this mean for Tornado Cash?
First, what does this mean for Tornado Cash?
 One of the core ideas behind Proposer-Builder Separation is that proposers cannot be allowed to see the contents of the block they're signing until they've signed the block. Proposers must trust mev-boost to return the most profitable header to them.
One of the core ideas behind Proposer-Builder Separation is that proposers cannot be allowed to see the contents of the block they're signing until they've signed the block. Proposers must trust mev-boost to return the most profitable header to them. 
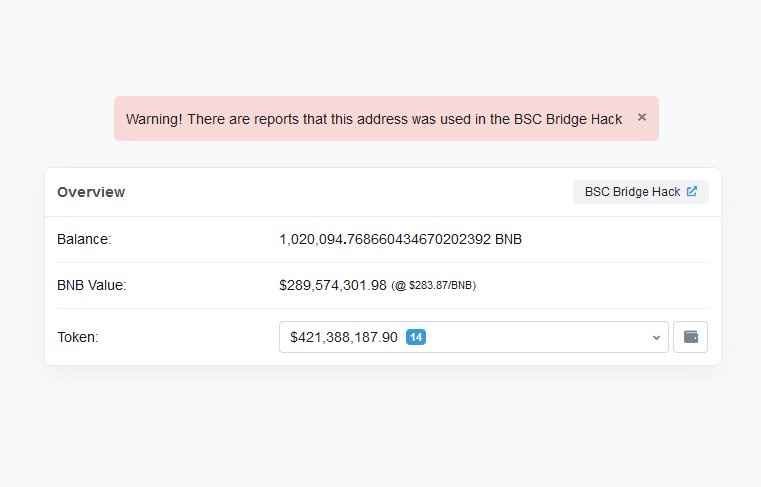
 It all started when @zachxbt sent me the attacker's address out of the blue. When I clicked into it, I saw an account worth hundreds of millions of dollars. Either someone had pulled off a huge rug, or there was a massive hack underway
It all started when @zachxbt sent me the attacker's address out of the blue. When I clicked into it, I saw an account worth hundreds of millions of dollars. Either someone had pulled off a huge rug, or there was a massive hack underway 

 2/ It all started when @officer_cia shared @spreekaway's tweet in the ETHSecurity Telegram channel. Although I had no idea what was going on at the time, just the sheer volume of assets leaving the bridge was clearly a bad sign
2/ It all started when @officer_cia shared @spreekaway's tweet in the ETHSecurity Telegram channel. Although I had no idea what was going on at the time, just the sheer volume of assets leaving the bridge was clearly a bad sign 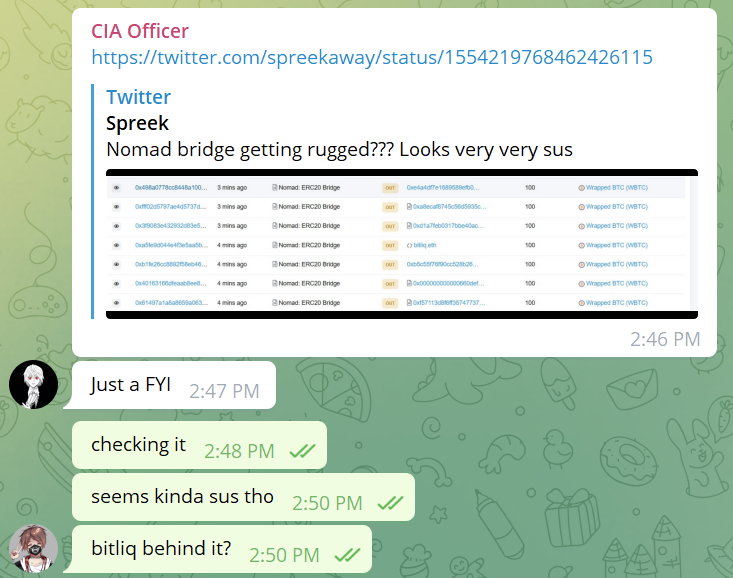

 2/ The first step is to create an urgent and compelling hook. When placed under pressure, even trained security professionals might act instinctively instead of rationally. This DM does both.
2/ The first step is to create an urgent and compelling hook. When placed under pressure, even trained security professionals might act instinctively instead of rationally. This DM does both.

https://twitter.com/samczsun/status/1506578902331768832So as I mentioned earlier, the two token accounts must hold the same token. The attacker forged accounts to bypass the validation on common.crate_collateral_tokens, but what about depositor_source?
https://twitter.com/samczsun/status/1506578904764583940

 In order to mint new CASH, you need to deposit some collateral. This cross-program invocation (CPI) will transfer tokens from your account to the protocol's account, but only if the two accounts hold the same type of token. Otherwise, the token program will reject the transfer.
In order to mint new CASH, you need to deposit some collateral. This cross-program invocation (CPI) will transfer tokens from your account to the protocol's account, but only if the two accounts hold the same type of token. Otherwise, the token program will reject the transfer. 
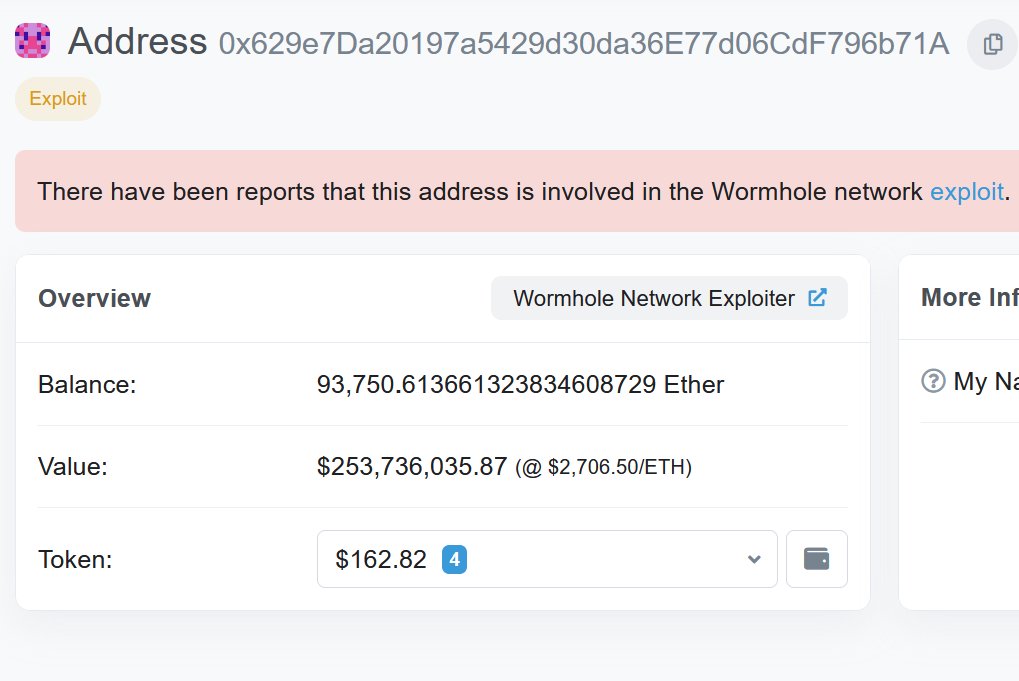
 First, we had to determine where the exploit occurred. Ethereum, or Solana? A quick check of the encoded VM that the attacker submitted showed that it contained valid signatures from the guardians. This meant that either they got the private keys, or they exploited the bridge.
First, we had to determine where the exploit occurred. Ethereum, or Solana? A quick check of the encoded VM that the attacker submitted showed that it contained valid signatures from the guardians. This meant that either they got the private keys, or they exploited the bridge. 
