How to get URL link on X (Twitter) App


 This service is a product by Cloudflare that helps images load quicker, but whenever used, inadvertently leaks a unique ID that ties back to the host's Cloudflare account. The unique ID that DOGE is using is the following: DzHG7ZU0tz6F1ZKEddmHuw
This service is a product by Cloudflare that helps images load quicker, but whenever used, inadvertently leaks a unique ID that ties back to the host's Cloudflare account. The unique ID that DOGE is using is the following: DzHG7ZU0tz6F1ZKEddmHuw 

 For about an hour they asked me vague questions related to a "high profile phishing campaign" and how my IP address could've end up being "tagged" to a threat actor, showing me a manila folder with my own photo, my home IP address, and some random social media accounts of mine.
For about an hour they asked me vague questions related to a "high profile phishing campaign" and how my IP address could've end up being "tagged" to a threat actor, showing me a manila folder with my own photo, my home IP address, and some random social media accounts of mine.

 After finding individual vulnerabilities affecting different car companies, we became interested in finding out who exactly was providing the auto manufacturers telematic services.
After finding individual vulnerabilities affecting different car companies, we became interested in finding out who exactly was providing the auto manufacturers telematic services.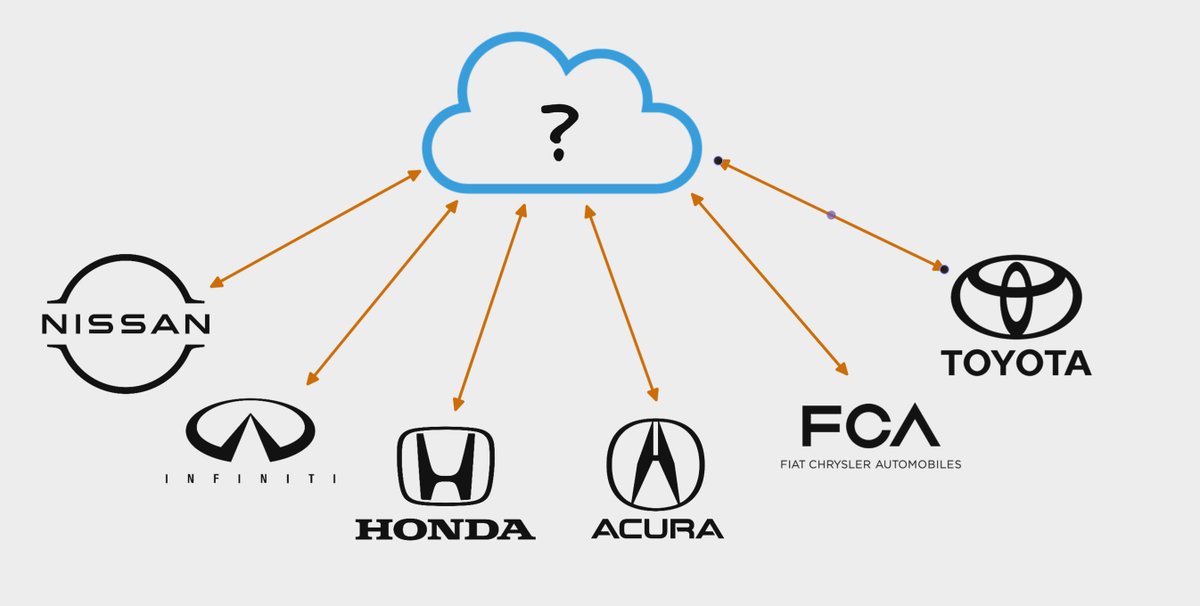

 Our finding began with @_specters_ reaching out to @bbuerhaus and myself to help explore potential security issues affecting vehicle telematics services.
Our finding began with @_specters_ reaching out to @bbuerhaus and myself to help explore potential security issues affecting vehicle telematics services.

https://twitter.com/WillyTheDegen/status/1509771063265091587

 an "@Everyone" message to be sent in a large public server using the Dyno bot, and I'm wondering if the hackers noticed this and began looking themselves? These bots have a massive amount of trust (admin roles on >1mm servers, people click URLs willingly, etc), and for /2
an "@Everyone" message to be sent in a large public server using the Dyno bot, and I'm wondering if the hackers noticed this and began looking themselves? These bots have a massive amount of trust (admin roles on >1mm servers, people click URLs willingly, etc), and for /2



 The "hs-fs" directory is pointed towards some CDN owned by Hubspot which all customers are allowed to add JavaScript and CSS to, but after registering to the Hubspot portal we found that you could deploy HTML files directly via a legacy API.
The "hs-fs" directory is pointed towards some CDN owned by Hubspot which all customers are allowed to add JavaScript and CSS to, but after registering to the Hubspot portal we found that you could deploy HTML files directly via a legacy API. 
https://twitter.com/RektHQ/status/1470431503045828614Over the last year or so we've hacked on tons of Web2


