
Senior Director @Fastly | software resilience + modern infosec | shortridge@hachyderm.io | https://t.co/68itNjq8tL | aka &void;
How to get URL link on X (Twitter) App




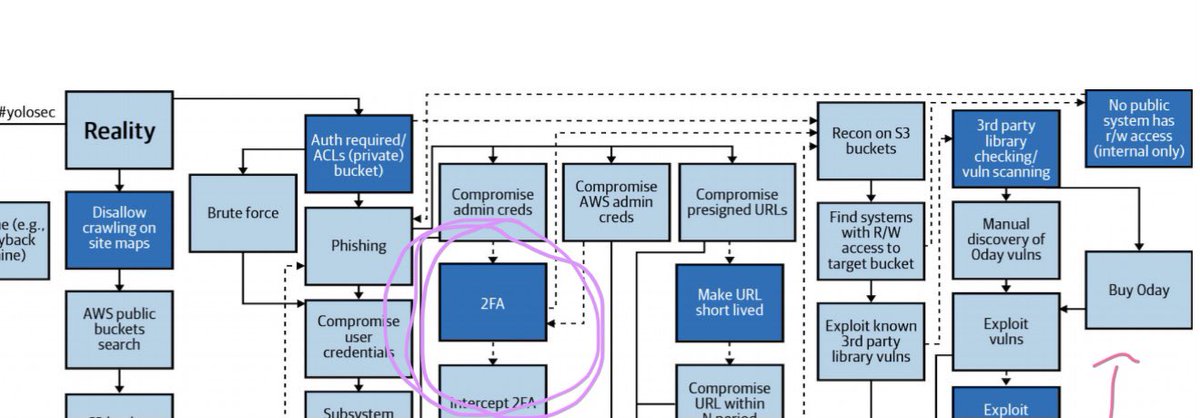
https://twitter.com/natashabertrand/status/13393805915994972161/8 First, let’s recall that Prospect Theory leads humans to overweight small probabilities (like attackers using 0day chains) and underweight large probabilities (like attackers intercepting 2FA).

 Social engineering isn’t all about charm and luck — it involves a strategy & a plan, always.
Social engineering isn’t all about charm and luck — it involves a strategy & a plan, always.


 SecOps hierarchy of needs was created in the 1970s, as pointed out by @argvee, & we’re constantly rethinking how to do detection. She thinks we’re in the early days of this current 5 year detection cycle — this time, catalyst is the cloud
SecOps hierarchy of needs was created in the 1970s, as pointed out by @argvee, & we’re constantly rethinking how to do detection. She thinks we’re in the early days of this current 5 year detection cycle — this time, catalyst is the cloud 
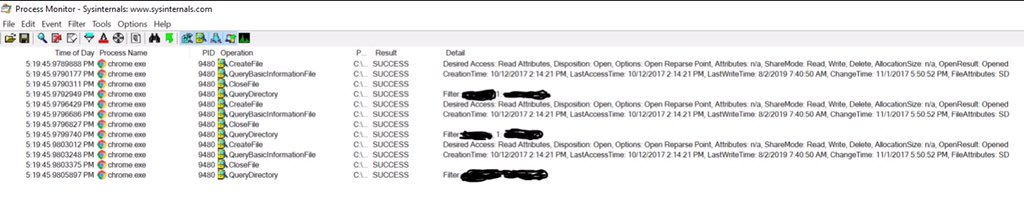
 Here’s the source on the Windows device scanning: support.google.com/chrome/answer/… “Chrome helps you find suspicious or unwanted programs on your Windows computer.”
Here’s the source on the Windows device scanning: support.google.com/chrome/answer/… “Chrome helps you find suspicious or unwanted programs on your Windows computer.”