
The creatures can see where each star has been and where it is going, so that the heavens are filled with rarefied, luminous spaghetti.
3 subscribers
How to get URL link on X (Twitter) App








 The WL email releases are made up of individual EML files. Every file has a last mod time and we can arrange them in last mod time order. We might expect to see a timeline that looks like this.
The WL email releases are made up of individual EML files. Every file has a last mod time and we can arrange them in last mod time order. We might expect to see a timeline that looks like this.


https://x.com/tralfamadorenik/status/1766509021580632431The plot thickens.



 Background: In the DNC emails we see some late dated emails (149 of them) sent locally via a server named DNCDAG2; for those emails we can subtract the sent time from the received time. Unfortunately, the times are accurate only to the nearest second.
Background: In the DNC emails we see some late dated emails (149 of them) sent locally via a server named DNCDAG2; for those emails we can subtract the sent time from the received time. Unfortunately, the times are accurate only to the nearest second.

https://twitter.com/tralfamadorenik/status/1766509021580632431Before we address that question directly, let's rule out a few possibilities. First, let's recall that the DNC's on site experts had no clue.


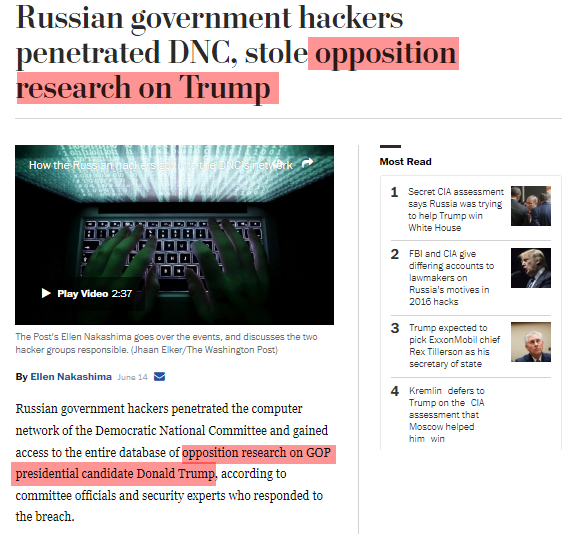

 tag: @News_Views_2020, @FOOL_NELSON, @ClimateAudit, @realexmaple, @walkafyre, @TrustIsEarnd, @bleidl, @ITGuy1959, @with_integrity , @Ty_Clevenger
tag: @News_Views_2020, @FOOL_NELSON, @ClimateAudit, @realexmaple, @walkafyre, @TrustIsEarnd, @bleidl, @ITGuy1959, @with_integrity , @Ty_Clevenger

 Alfa Bank sends a demand letter to Dagon, notably requesting "White Paper Comments: Time Series Analysis of Recursive Queries". We can't quite tell if this is the seminal paper or just Dagon's comments on same.
Alfa Bank sends a demand letter to Dagon, notably requesting "White Paper Comments: Time Series Analysis of Recursive Queries". We can't quite tell if this is the seminal paper or just Dagon's comments on same.

https://twitter.com/codyave/status/1497323436481277954



 IMO, the hacks caused the Alfa and Spectrum servers to ping the "Trump Server" in a seemingly mysterious pattern.
IMO, the hacks caused the Alfa and Spectrum servers to ping the "Trump Server" in a seemingly mysterious pattern.
 Which scenario in the chart best fits that description?
Which scenario in the chart best fits that description?
 We look at all gaps of less than 2 hours (7200 secs) and reduce their value to the next lowest 120 secs (2 mins) for the period > 7/24/2016 which is the day both Alfa and Spectrum are missing a day.
We look at all gaps of less than 2 hours (7200 secs) and reduce their value to the next lowest 120 secs (2 mins) for the period > 7/24/2016 which is the day both Alfa and Spectrum are missing a day.

 Tag: @FOOL_NELSON @ClimateAudit @bleidl @RyanM58699717 @walkafyre @ErrataRob @PeterSMagnusson @sempersecurus
Tag: @FOOL_NELSON @ClimateAudit @bleidl @RyanM58699717 @walkafyre @ErrataRob @PeterSMagnusson @sempersecurus



 @FOOL_NELSON @ClimateAudit @bleidl @walkafyre @RyanM58699717 @ErrataRob Consider: (1) the DNS search suffix list, (2) iterative name resolution, (3) DNS name caching both positive and negative.
@FOOL_NELSON @ClimateAudit @bleidl @walkafyre @RyanM58699717 @ErrataRob Consider: (1) the DNS search suffix list, (2) iterative name resolution, (3) DNS name caching both positive and negative.
