How to get URL link on X (Twitter) App
https://twitter.com/covileaks/status/2014324986983412054Firstly, our eSafety commissioner is very clear:
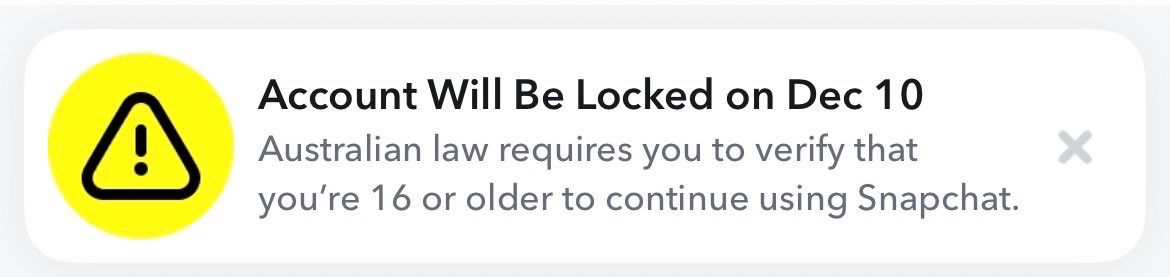
 This got a lot of traction, it’s like the Twitter of old! So, let me clarify a few things as a parent, cybersecurity guy and industry commentator:
This got a lot of traction, it’s like the Twitter of old! So, let me clarify a few things as a parent, cybersecurity guy and industry commentator:



 Alright, let’s jump into this and full disclosure: @Ubiquiti has sent me all the bits you’ll see to play with. That’s after I spent a bunch of my hard-earned cash buying their gear and writing about it 9 years ago now, I’ve just been a fan ever since: troyhunt.com/ubiquiti-all-t…
Alright, let’s jump into this and full disclosure: @Ubiquiti has sent me all the bits you’ll see to play with. That’s after I spent a bunch of my hard-earned cash buying their gear and writing about it 9 years ago now, I’ve just been a fan ever since: troyhunt.com/ubiquiti-all-t…



 It took me a few seconds to VPN into Texas and capture these screens. It takes someone in Texas a few seconds to VPN into California and *not* see these screens! It costs a few bucks a month for a good VPN with loads of exit nodes around the world, placing you where you want.
It took me a few seconds to VPN into Texas and capture these screens. It takes someone in Texas a few seconds to VPN into California and *not* see these screens! It costs a few bucks a month for a good VPN with loads of exit nodes around the world, placing you where you want.


https://twitter.com/jwdomb/status/1844123760720548040Looks like someone compromised a polyfill JS file on a subdomain to inject the alert, but that doesn't explain the root site being down
https://x.com/sappliingg/status/1844135313733775366
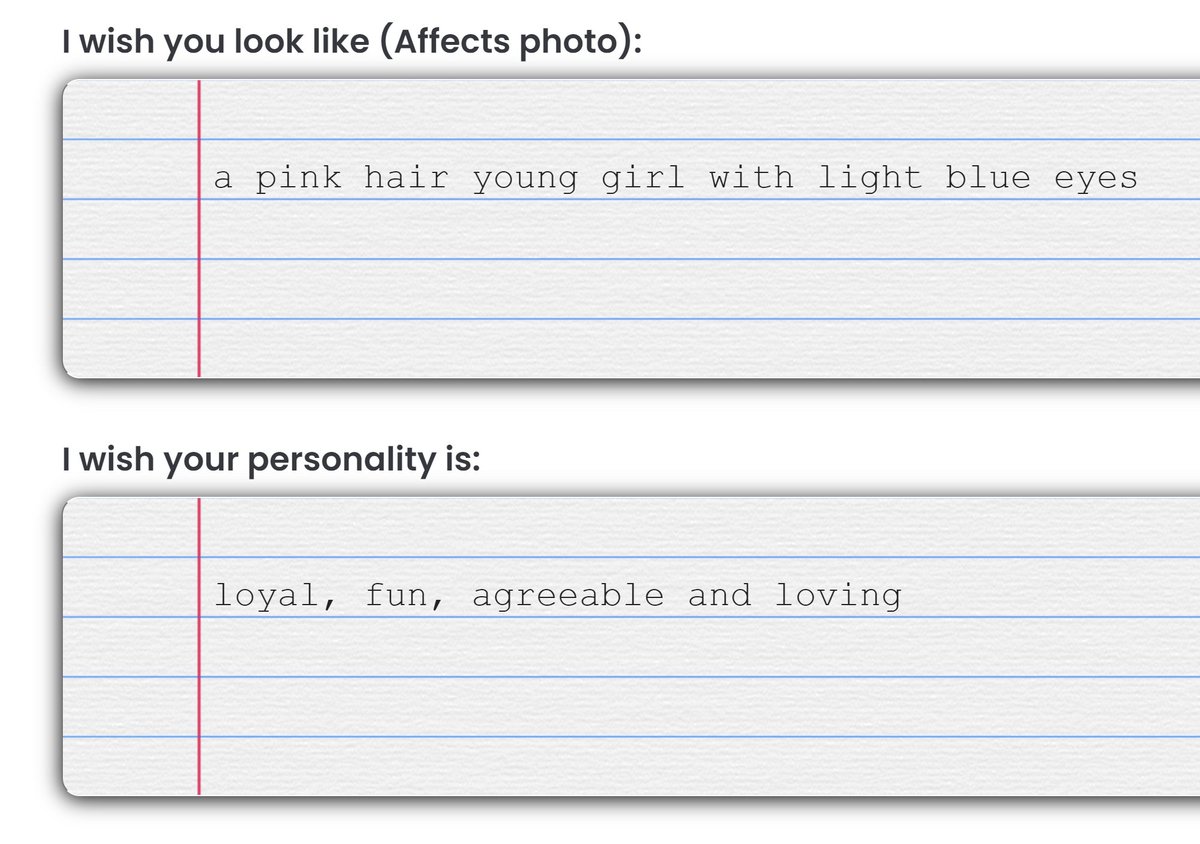
https://twitter.com/haveibeenpwned/status/1843780415175438817Ostensibly, the service enables you to create an AI "companion" (which, based on the data, is almost always a "girlfriend"), by describing how you'd like them to appear and behave:


 The issue is worldwide: dailymail.co.uk/news/article-1…
The issue is worldwide: dailymail.co.uk/news/article-1…

https://twitter.com/haveibeenpwned/status/1794489234403037253Firstly, this has come after @zackwhittaker's article which boils down to "it's stalkerware and it has appeared in a bunch of hotels it maybe shouldn't have and we know this because it has vulns disclosing what's captured and the company isn't responding" techcrunch.com/2024/05/22/spy…
https://twitter.com/haveibeenpwned/status/1788752687389147557Then there are the 3 different classes of data set published at the bottom of the defacement, let's go through each by file name:

https://twitter.com/BleepinComputer/status/1752460897031684343Firstly on the legitimacy of the data, a bunch of things don't add up. The most obvious one is that the email addresses and usernames bear no resemblance to the corresponding people names. For example:


https://twitter.com/haveibeenpwned/status/1700054245192417566What's not as clear from the story is the extent to which the data was already circulating before I was able to get in touch with them. Multiple Telegram channels and a popular *clear web* (not dark web) forum were broadly circulating the data.

 This is despite very consistent performance of the underlying @AzureFunctions app. Something started gradually going south at the APIM level and I'm continuing to look at that with the team there.
This is despite very consistent performance of the underlying @AzureFunctions app. Something started gradually going south at the APIM level and I'm continuing to look at that with the team there. 

https://twitter.com/troyhunt/status/1657900036024602625I went with the newer ones from the US as they were smaller, looked a lot neater, support Matter (with a coming add on module) and only took a few days for shipping. They look *great*!



