If intel community/Obama admin used report in attribution, it's worrying. If they were merely trying to gull public and incoming admin with nonsense, no better
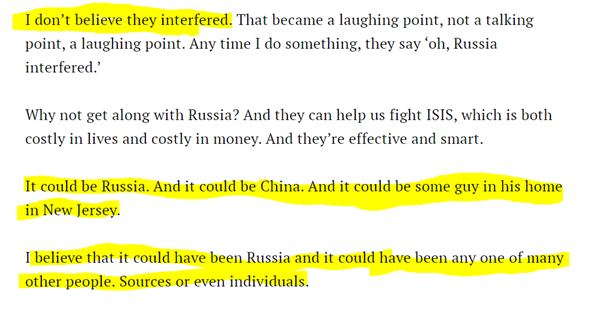
As of Nov 28, 2016, Trump remained skeptical of
time.com/4591183/time-p… intel community's attribution of DNC hack to Russia. He admitted possibility, but wasn't convinced based on then available information. This really annoyed media.
archive.is/PJhkH

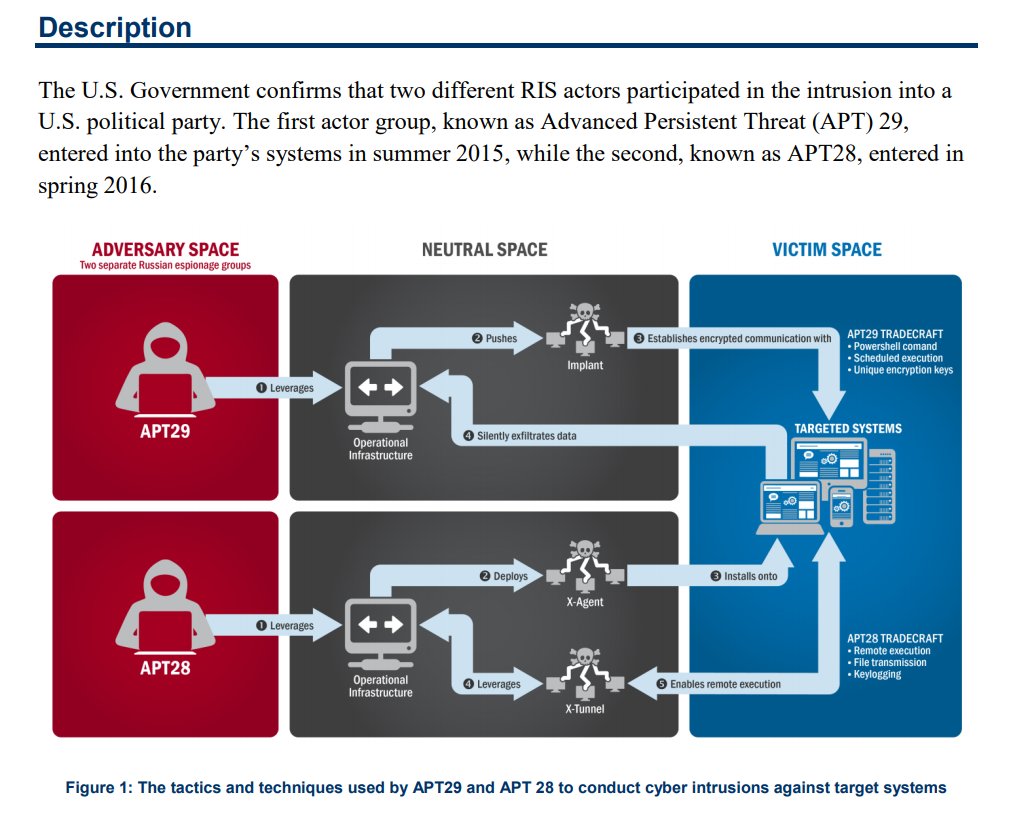
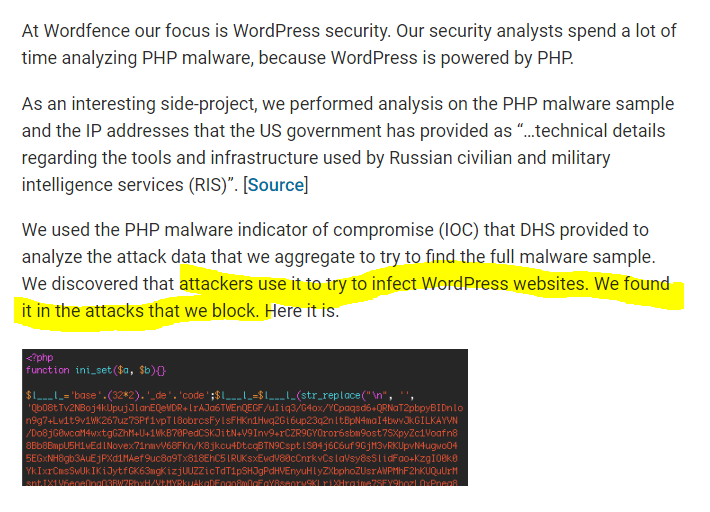
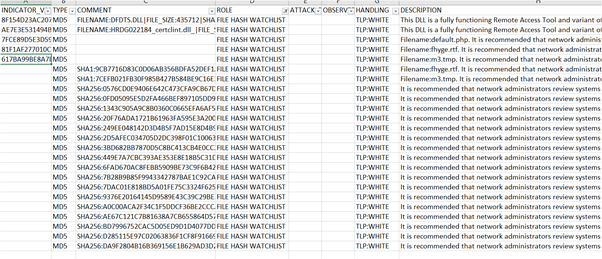
off-guardian.org/2017/01/09/did…

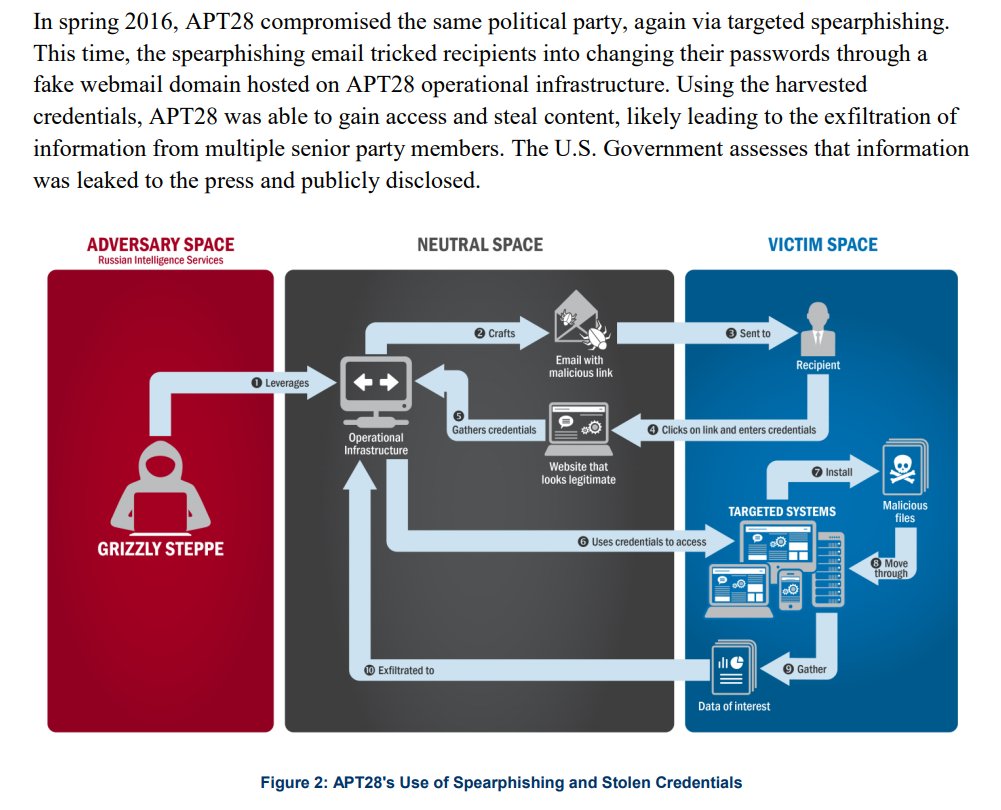
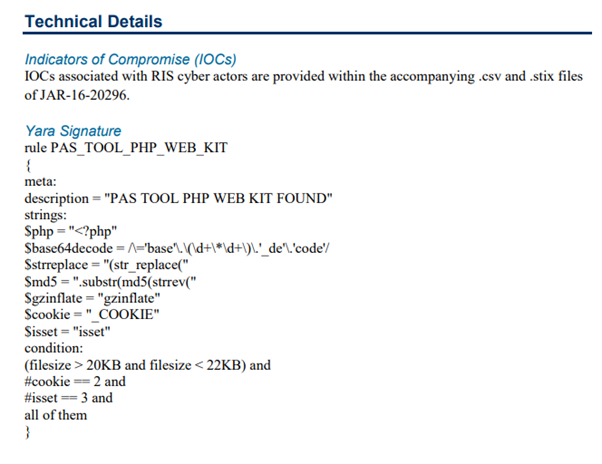
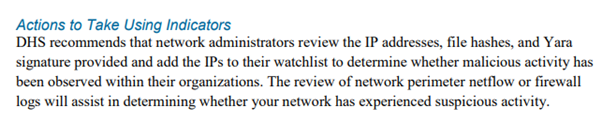
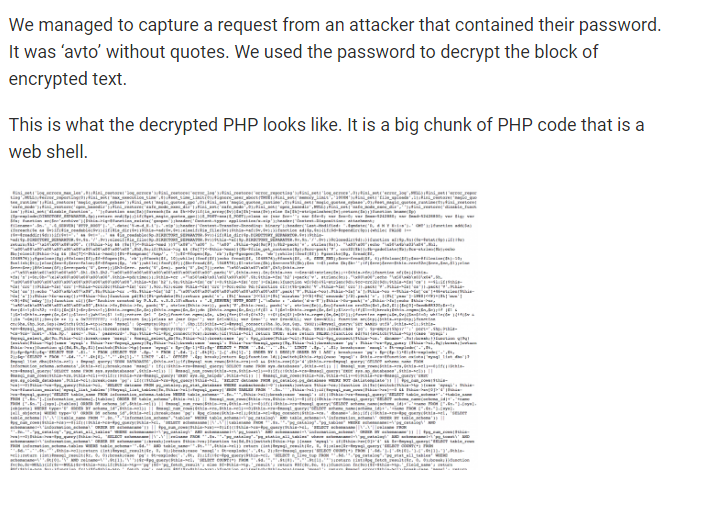
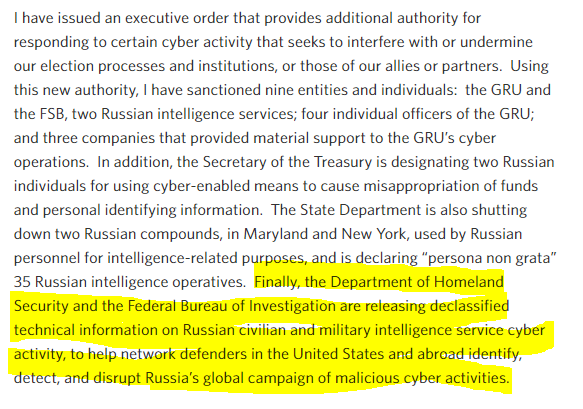
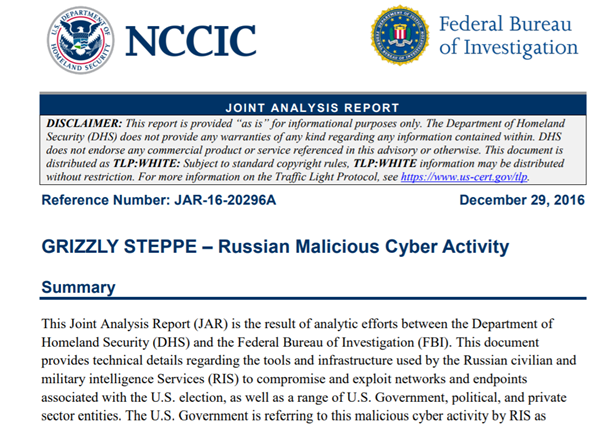
us-cert.gov/sites/default/… did nothing of the sort. They didn't connect anything in report to DNC hack, or even Russian state intel agencies.