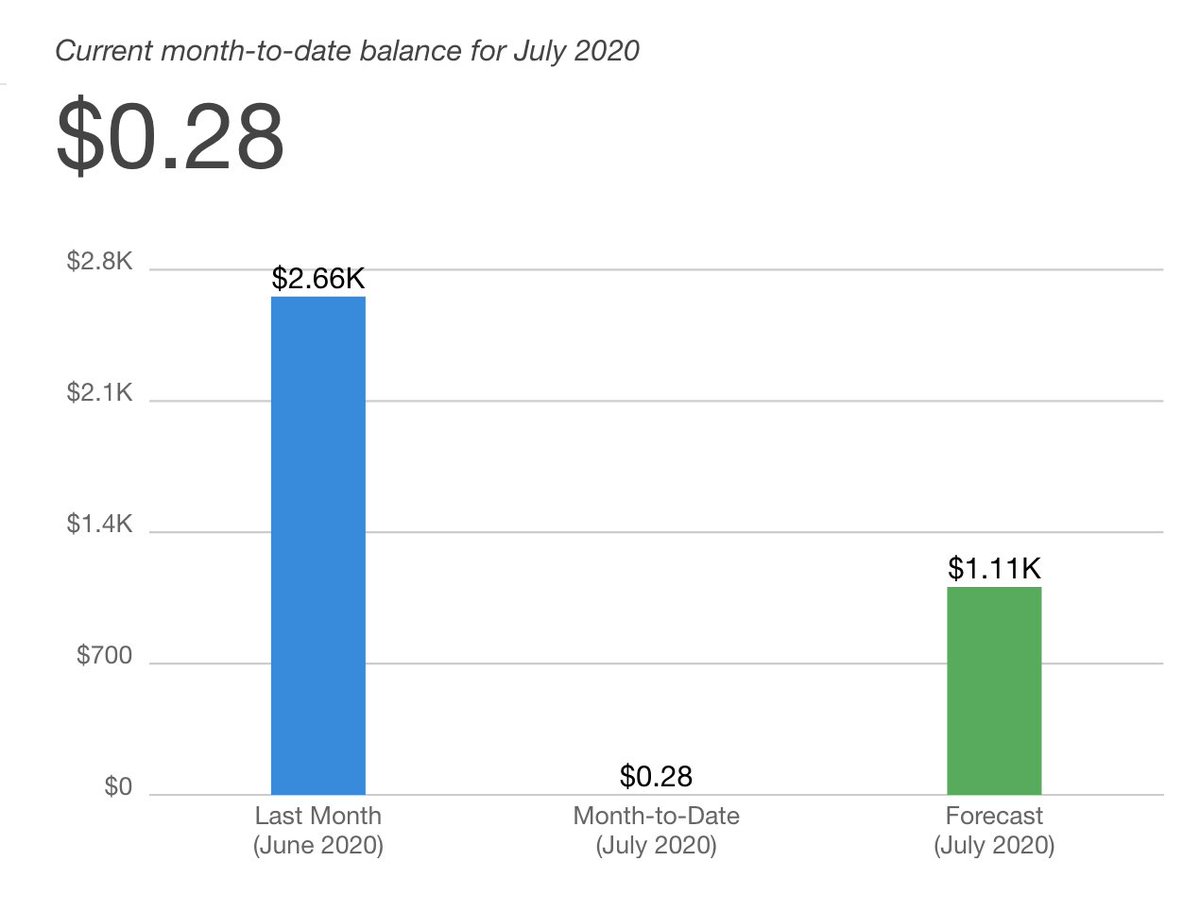
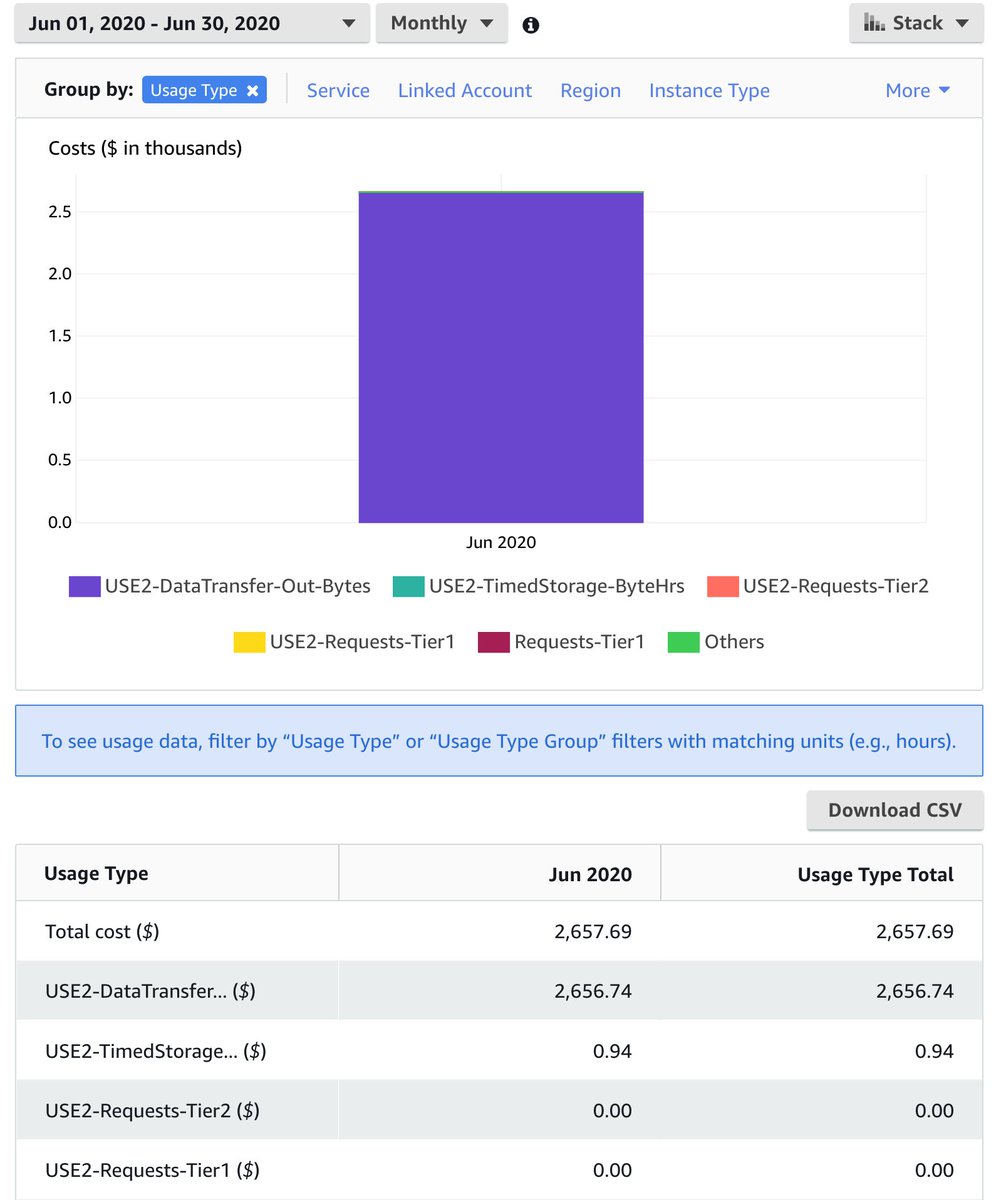
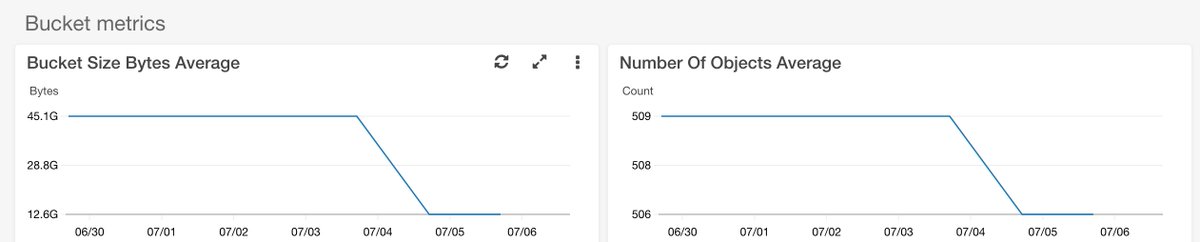
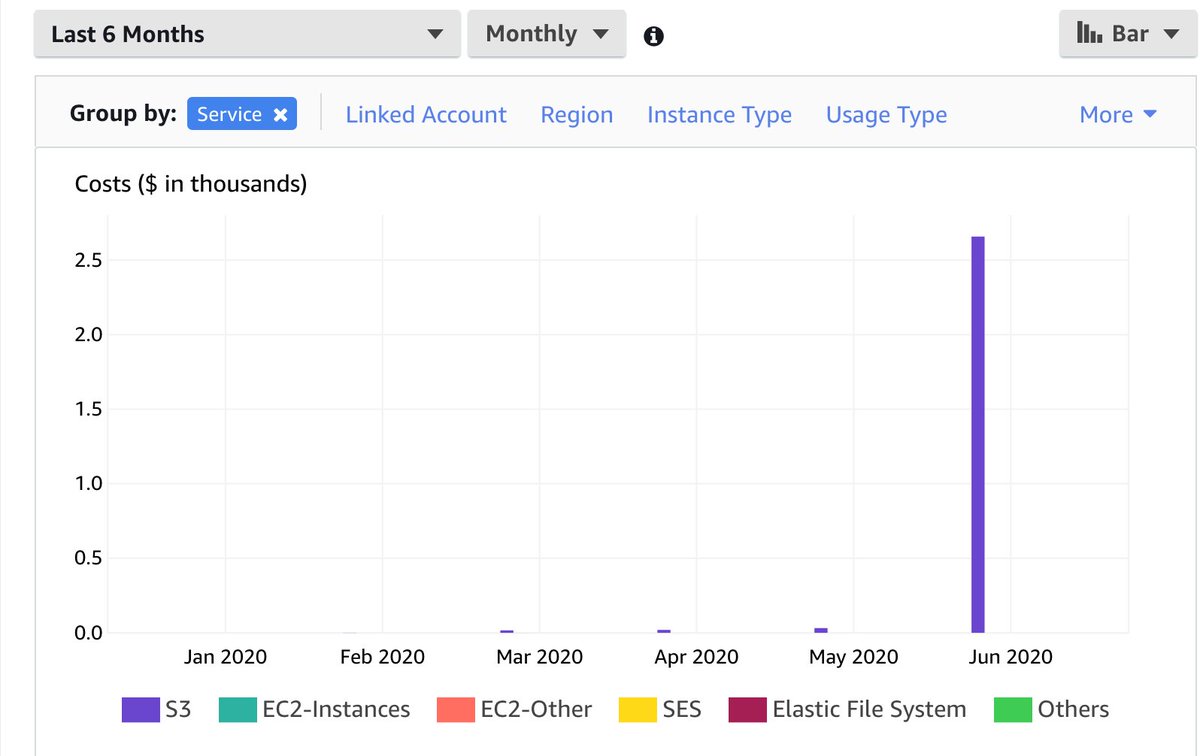
@chrisshort's surprise @awscloud bill of $2700 looks S3 driven...
Personal vs. corporate money is the difference between "HOLY POOP $80 FOR A BURGER" vs. "Can I get a receipt?"
Now seems an opportune time to mention that for all of their faults, this exact pattern on @oraclecloud would have caused Chris a $173 bill.

Nobody knows! Logging wasn't enabled on the bucket, so we can't see what objects or requestor IPs were involved. The entire response to @chrisshort here is a pile of Monday morning quarterbacking.
He's a @CloudNativeFdn Ambassador, works at IBM Hat, is deep in the Ansible community, etc.
"Surprise jackhole, your mortgage isn't your most expensive bill this month, guess you shoulda enabled billing alarms!" is crappy, broken, and WOULD NOT HAVE SOLVED THE PROBLEM!
What the hell kind of @awscloud "customer obsession" is this?
What do you imagine that does for his views of @awscloud moving forward?

"Surprise, here's a 100x bill multiplier over a 24 hour span from a billing system that aspirationally has an 8 hour resolution" is crap!
lastweekinaws.com/blog/its-time-…
Even in a corporate environment there's the fear of getting rage-fired for a bill surprise like this.
This wasn't a misconfigured bucket. This wasn't passing data back and forth 50 times. "Using system as intended / designed" and then a surprise bill out of nowhere hit.
This cannot be reasonably exploited to cause $1 million bill surprise, so it’s not in most companies’ risk assessments.

Enable the `BytesDownloaded` S3 metric for the bucket , then slap some decent deviation monitoring on it that alarms appropriately.
Asking someone to do this for a personal project is a fancy way of telling them to go f*ck themselves.
And this assumes you're ready to swing into action when you see it.