microsoft.com/security/blog/…
1/
2/
3/
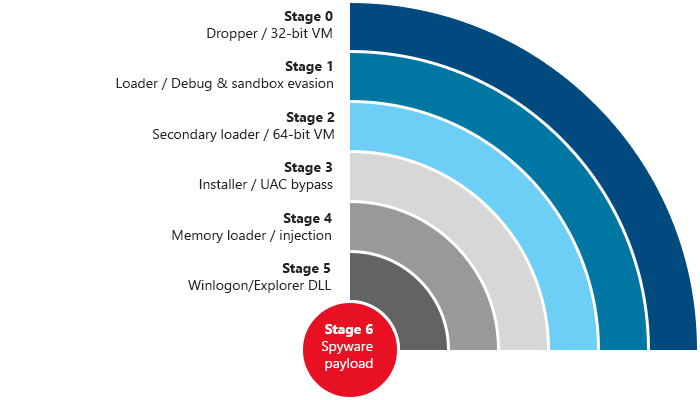
All of this code gets executed to load up a virtual machine with its own opcodes.
4/
5/
Next comes ANOTHER virtual machine with its own, different opcodes, which decrypts and loads more software.
6/
The injector also has countermeasures to defeat common detection methods.
7/
It's a very clever piece of puzzlemaking, and an even more clever piece of detective work to solve it.
8/
This may be the key to how Marcus "Malwaretech" Hutchins saved the world from Wannacry ransomware.
9/
10/
pluralistic.net/2020/05/13/mal…
11/
eof/





