Some AD admins may know how to fix these issues, but it's fair to assume some do not.
I'd also highly recommend using PingCastle by @mysmartlogon as it audits most of this and more.
Thread time!
Powershell: Set-ADDomain -Identity <Domain> -Replace @{"ms-DS-MachineAccountQuota"="0"} -Verbose
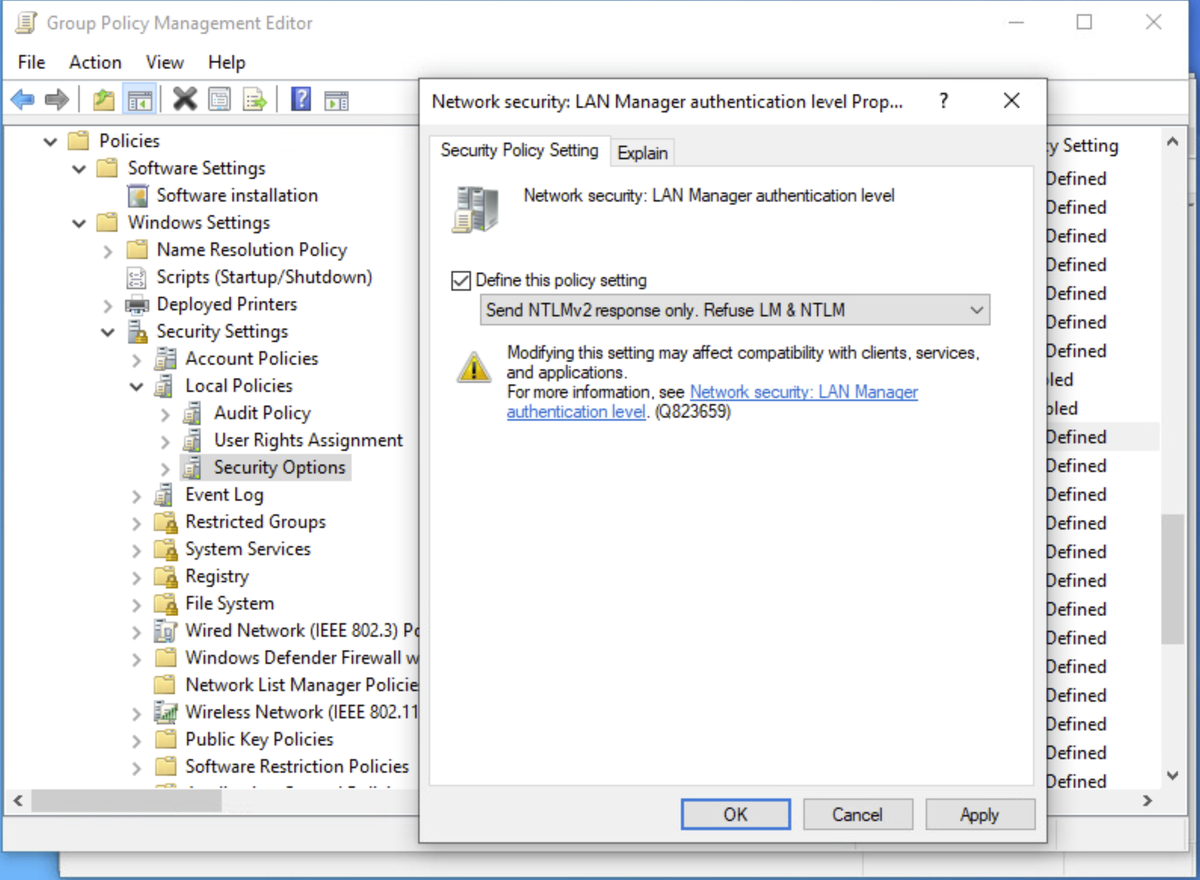
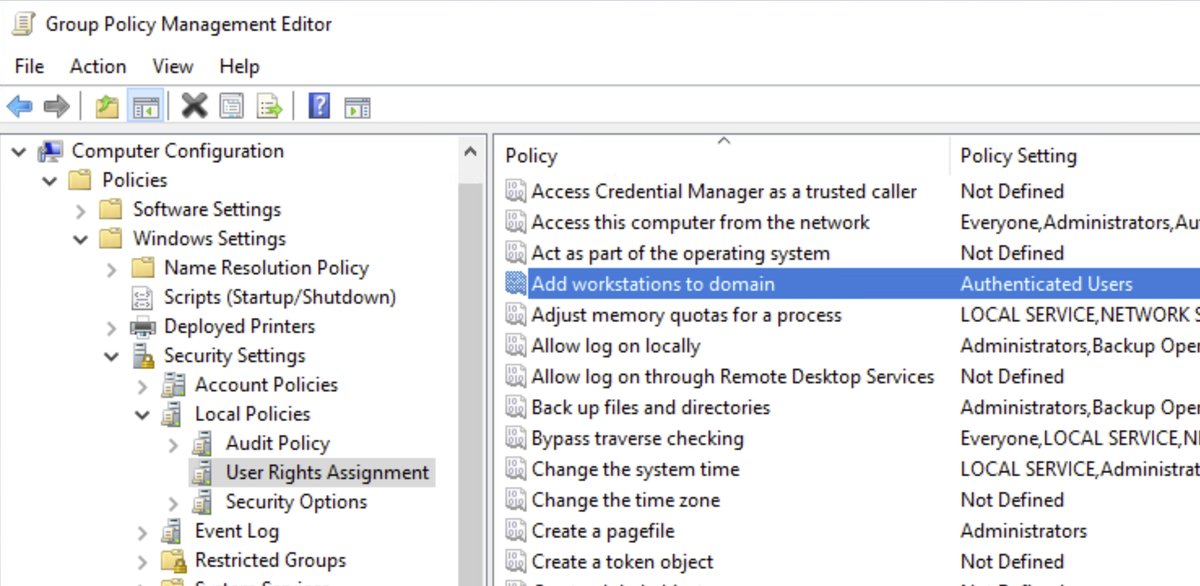
GPO: Modify Default Domain Controller Policy and remove Authenticated Users from the user rights assignment (1st pic)
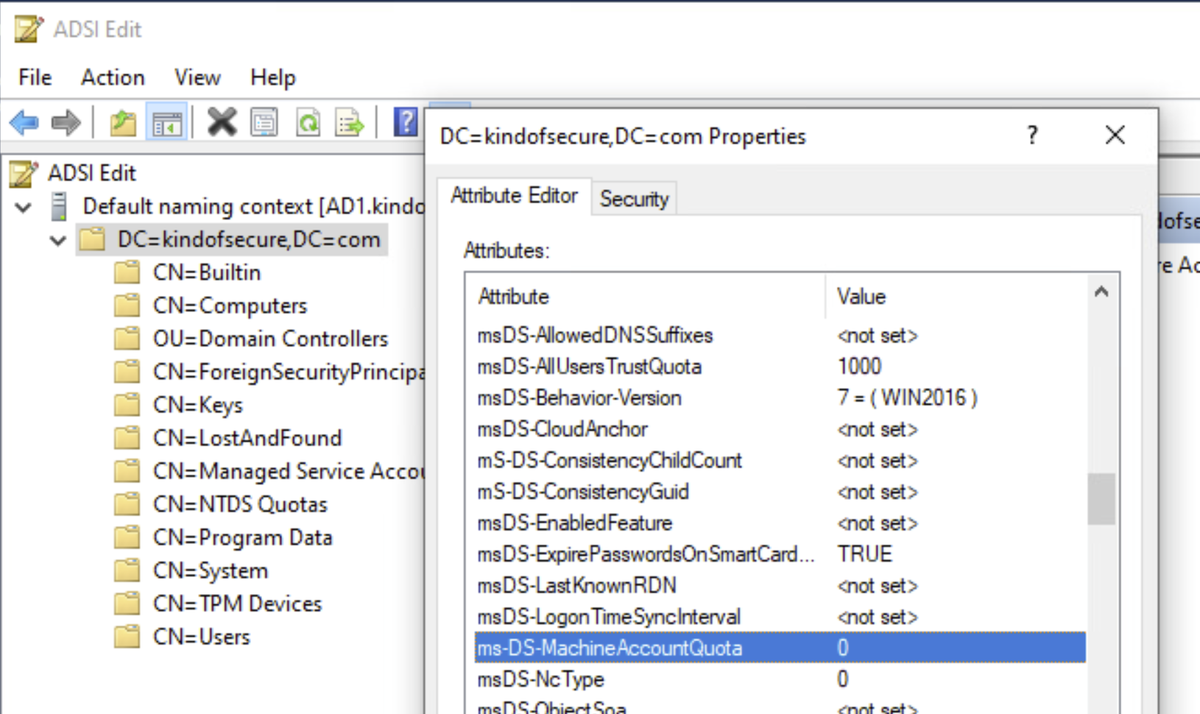
ADSI: (2nd pic)
moderndeployment.com/correct-domain…
Also, change binding to create objects in an OU with strict policies:
redircmp "OU=Bind,DC=Domain,DC=Com"
redirusr can be used for users if you want.
Run with proper permissions, control click to select ones to clear, click OK, confirm)
Get-ADObject -LDAPFilter "(&(admincount=1)(objectclass=user)" | Out-GridView -PassThru | Set-AdObject -Clear @('admincount') -Confirm -Verbose
Limit all of these groups:
docs.microsoft.com/en-us/windows-…
Understand managing privileged identities:
docs.microsoft.com/en-us/windows-…
Work to empty these groups, use PAWs, get a PAM solution, and leave only honeytokens in there to piss off attackers ;)
Look, most apps claiming to need Domain Admin to work are lying to you.
Vendors that do this are lazy and care more about their support time than your security.
Consider using gMSA's with least privilege possible
docs.microsoft.com/en-us/windows-…
I'd start with Bloodhound to remove most risky first, then run this script:
manageengine.com/products/ad-ma…
Then:
$securityreport | Select IdentityReference, ActiveDirectoryRights, OrganizationalUnit, IsInherited -Unique | Export-Csv -Path "path" -NoTypeInformation
Extremely long passwords on services accounts if you can't use gMSA's
Also could evaluate Kerberos Armoring (aka FAST) - just be careful:
docs.microsoft.com/en-us/previous…
Also read @PyroTek3 articles: adsecurity.org/?p=3458
Get-ADUser -Filter { passwordNeverExpires -eq "true" }
Convert service accounts over to gMSA's if you can
Many credential vaults from vendors like CyberArk, Thycotic, etc. can rotate strong passwords for you on any AD accounts you need. Evaluate them!
Holy crap - give them a password...
9) AD Passwords stored using reversable encryption
Get-ADUser -Filter { userAccountControl -band 128 }
Ask why, and if no one knows, create a new account to test replacing it with at your next opportunity.
CIS guidance of 60 days is too short
My recommendation (in order):
- Reject weak passwords (covered later)
- SSO all the things
- Increase length to around 16 characters, remove complexity, and push phrases/sentences
- 1 yr expiry
- Hashcat your users
Know your envinronment. I have thousands of accounts that go inactive depending on time of year or what the user signed up for.
Make flexible policies based on needs. This is 90 days:
Search-ADAccount –AccountInactive -TimeSpan 90.00:00:00 -UsersOnly
Use fine-grained password policies so privileged, interactive users have stricter requirements
Use gMSA or cred management solution to ensure service account passwords rotate often.
Create new accounts for new installs. Don't be lazy.
I love Azure AD Password Protection:
docs.microsoft.com/en-us/azure/ac…\
But not everyone can afford it. @BHinfoSecurity is amazing and provides a free AD password filter that I'd be willing to trust putting in my AD.
blackhillsinfosec.com/the-creddefens…
Education is key
This has been blocked for a long time, but legacy GPO's still exist
Quick tool to find them:
github.com/l0ss/Grouper2
Consider new policies for each version of Windows (use WMI filters, add security baseline) to deprecate old policies.
Check out the content by the folks I've mentioned in the thread as that's a huge part of where I've learned what I know.
Last thing - be willing to ask questions. Smart people ask questions ;)