Lol it's so much
When the Ethereum network split into two (ETC and ETH, July 2016) the networks didn't have replay protection so you would send thru these contracts that were super simple and would ensure that ONLY your ETH or ETC was sent on the intended chain.
When the Ethereum network split into two (ETC and ETH, July 2016) the networks didn't have replay protection so you would send thru these contracts that were super simple and would ensure that ONLY your ETH or ETC was sent on the intended chain.
https://twitter.com/fengtality/status/1282842269725278208
It was especially important exchanges did this as in the first days of the network split, users who were "in the know" could send only ETH to, say, Coinbase and then withdraw that ETH but actually receive ETH & ETC and then send that ETH and separately ETC to Poloniex to profit.
It doesn't matter if the forkchain doesn't have value but the moment Polo listed ETC (about 3 days after the hard fork) ETC had value and eventually anyone who had ETH listed at the time of the fork had to credit their customers w ETC. That they may have inadvertantly given away.
(Shout-out to @ShapeShift_io who not only foresaw this as a real possibility while most were of us had the "longest chain will win" mindset BUT ALSO RELEASED A TOOL FOR USERS WITHIN DAYS SO USERS COULD SAFELY "SPLIT" THEIR ETH & ETC!!! 👏👏👏👏)
Okay but this is NOT THE CODING ERROR rekt Quadriga. Lol. #QCX
Usually exchanges handle funds like this:
1. User sends to their user deposit address (onchain)
2. Exchange sweeps to hot wallet (onchain)
3. Exchange credits users exchange acct balance (DB)
Usually exchanges handle funds like this:
1. User sends to their user deposit address (onchain)
2. Exchange sweeps to hot wallet (onchain)
3. Exchange credits users exchange acct balance (DB)
Once the fork happened, you need to split all new funds or funds you held at time of fork. For some, it's a massive undertaking.
An OG infamous account known as "The accumulator" generated a lot of interest and speculation when they split their holdings.
reddit.com/r/ethereum/com…
An OG infamous account known as "The accumulator" generated a lot of interest and speculation when they split their holdings.
reddit.com/r/ethereum/com…
But QCX. Oh sweet #QCX. For the next year, even after network-level replay protection was added, they just did this:
1. User sends to use deposit addy
2. Exchange sends thru "safe split" contract to their hot wallet
3. Exchange credits user acct balance (DB)
1. User sends to use deposit addy
2. Exchange sends thru "safe split" contract to their hot wallet
3. Exchange credits user acct balance (DB)
Everything was fine until one day the TXs that were sent via this safe split contract just....didn't make it to their final destination (the #QCX hot wallet)
This is partly bc the contract was so simple it didn't account for unhappy paths. But neither did their sweeper code.
This is partly bc the contract was so simple it didn't account for unhappy paths. But neither did their sweeper code.

So for 3 days in June 2017 all user deposits were sent to the contract, the contract didn't pass them along, but users were still credited.
Until @BokkyPooBah was like "uh hey guys you know all your money is getting stuck, right?"
reddit.com/r/ethereum/com…
Until @BokkyPooBah was like "uh hey guys you know all your money is getting stuck, right?"
reddit.com/r/ethereum/com…
And QuadrigaCX was like "oh shit oops. Don't worry though, we are #1 exchange and we are Canadian therefore you can trust us when we say we'll cover the loss with our profits."
old.reddit.com/r/ethereum/com…
old.reddit.com/r/ethereum/com…
And so until Feb 2019, everyone trusted them and no one was like "yo where are your cold wallets?" until it was revealed that QCX top dog Gerald Gotten had died ("died") and "no one knows where the keys are" which is code for "there are no cold wallets."
https://twitter.com/tayvano_/status/1092439754849759233?s=19
And everyone was like "but Canadians are the trustworthy and nice!"
And Gerald was like "lol canadians are really good at running schemes and laundering money too and man the weather in Thailand/hell is super hot compared to Canada! 😎"
vanityfair.com/news/2019/11/t…
And Gerald was like "lol canadians are really good at running schemes and laundering money too and man the weather in Thailand/hell is super hot compared to Canada! 😎"
vanityfair.com/news/2019/11/t…
Then any remaining $ was spent trying to find the $ and creating a report (June 2020).
And no one was like "BITCOIN FIXES THIS" even tho AN IMMUTABLE TRANSPARENT LEDGER THAT ENSURES ACCOUNTABILITY LITERALLY FIXES THIS but #digitalgold > #DeFi, amiright?
osc.gov.on.ca/quadrigacxrepo…
And no one was like "BITCOIN FIXES THIS" even tho AN IMMUTABLE TRANSPARENT LEDGER THAT ENSURES ACCOUNTABILITY LITERALLY FIXES THIS but #digitalgold > #DeFi, amiright?
osc.gov.on.ca/quadrigacxrepo…
The end.
• • •
Missing some Tweet in this thread? You can try to
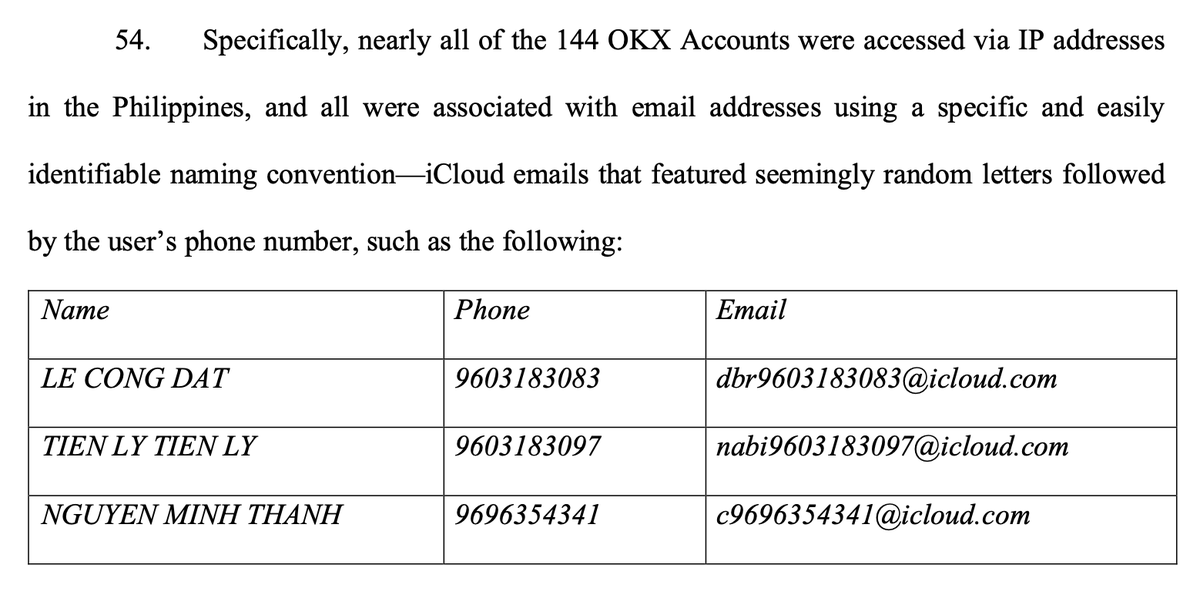
force a refresh