At some point, you have to put your trust in someone / something. This was an initial barrier to cloud adoption.
We take it on faith.
My first *nix admin gig was at a university as their email admin. I *could* have done evil things; I did none of them.
In most cases, we separate things out. Yes, in virtually every org there are people who could access anything that you haven't encrypted that passes through their systems.
2. Everything they do is logged immutably to systems to which they definitively do not have access. A separate team entirely manages and reviews that environment.
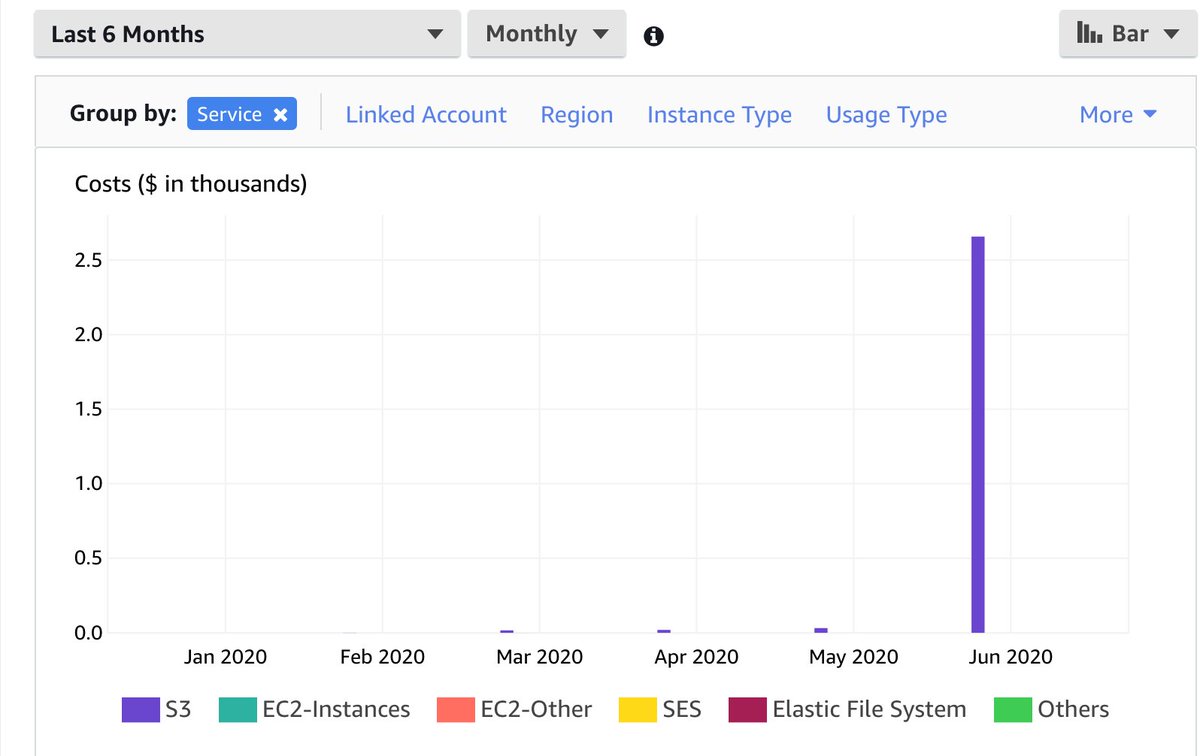
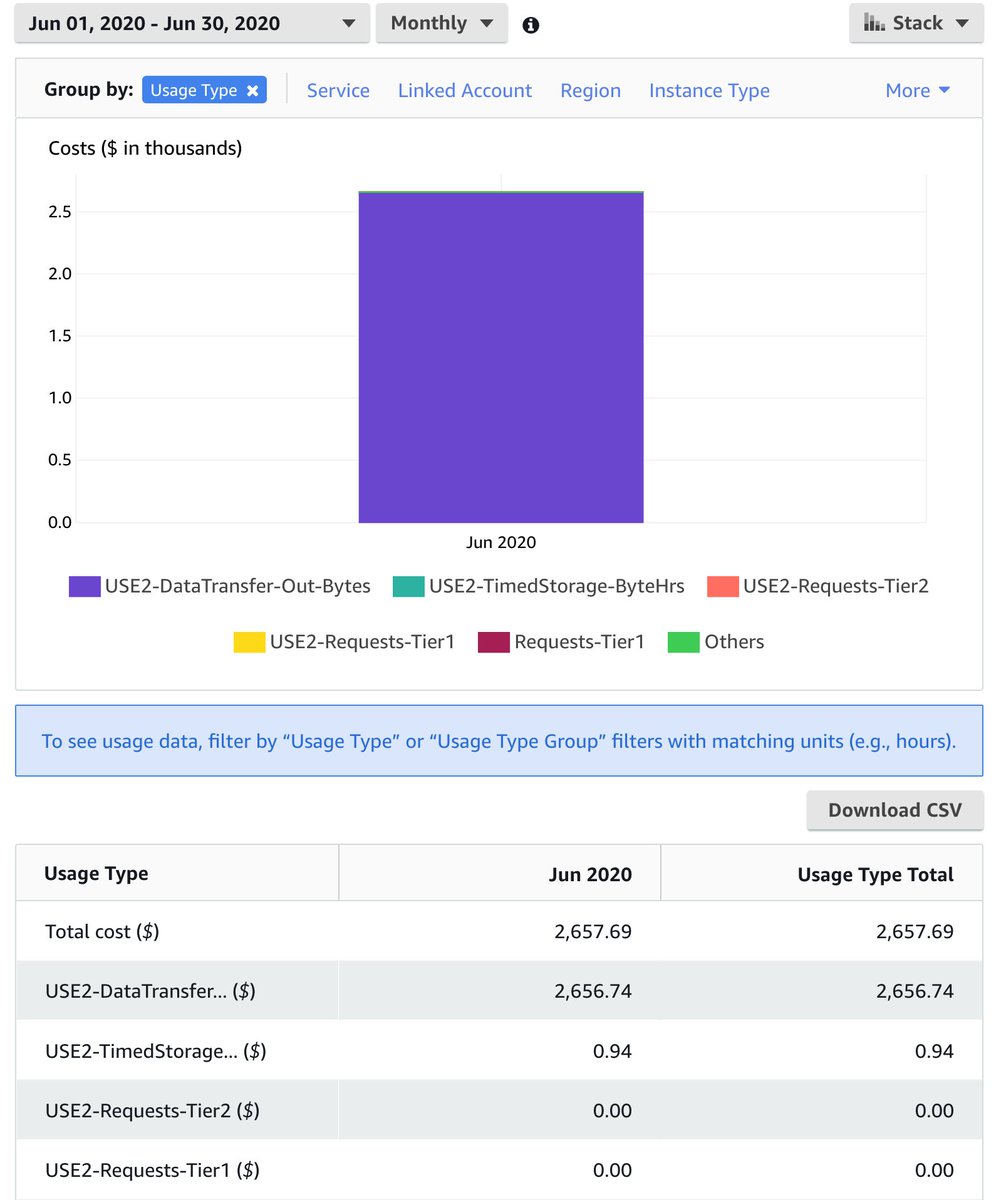
(The bill is usually small if they haven't fallen for the Macie trap.)
It turns out that in reality, it's way harder to subvert the right set of @awscloud employees than the datacenter night shift folks that your company criminally underpays.
You may not! If you can unilaterally change the user's email address in a company's records, you can effectively become them completely as far as most systems are concerned.
* Who changed that customer's email address?
* What time did they do it?
* From where were they accessing the internal system?
This is why there are audit logs. You won't necessarily be able to STOP everything, but you'll for damned sure know what happened and when.
Have you *MET* users? You'd need a shitload of VPs whose entire job was rubber stamping password and email address resets! Fatigue would set in, and they'd get sloppy. Humans do that.
Security is a trade-off. Make things secure enough and nobody will be able to use the damned thing.
Because nobody decent wants to see racial slurs trending.
You don't have a right to a platform for your shitty opinions, just a right to be free from government persecution.
They're smart people. They learn from their mistakes, and this won't happen again.
But something else will! It always does! The dance continues.
Remember, today it's their breach but tomorrow it's yours. How will you want the world to treat you when it's your turn?