Many still don't understand that.
Also, the question of whether or not you can reverse the hash is irrelevant, if everyone uses the same function.
There are more complex versions of this, e.g. hashing the hashes, using temporary IDs and later match it to persistent ones, linking/matching chains of identifiers, using salted hashes for sub-purposes etc.
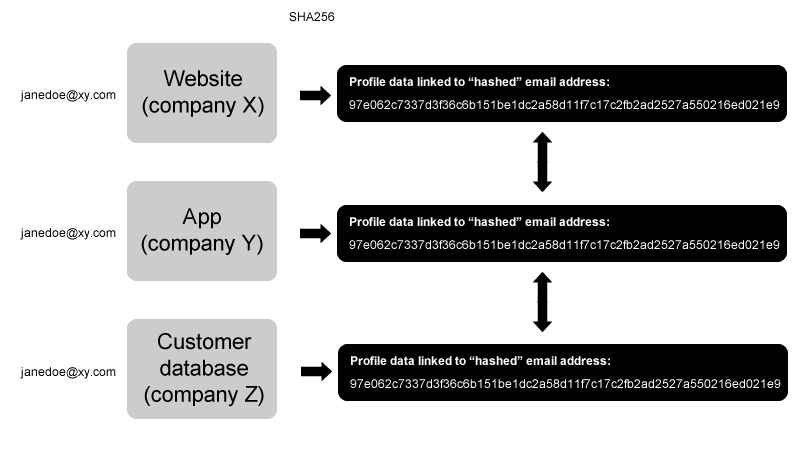
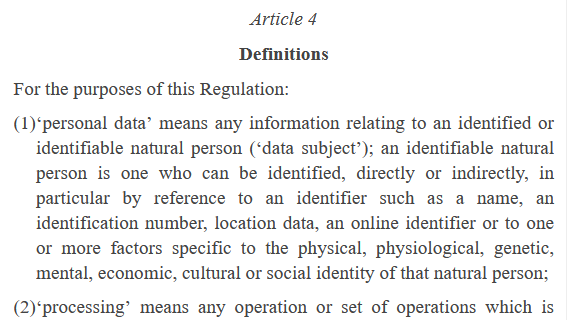
Sharing/matching personal data by converting email addresses into hashed pseudonymous identifiers across companies is just: sharing/matching personal data.
I wrote about this here (from p. 69):
crackedlabs.org/dl/CrackedLabs…


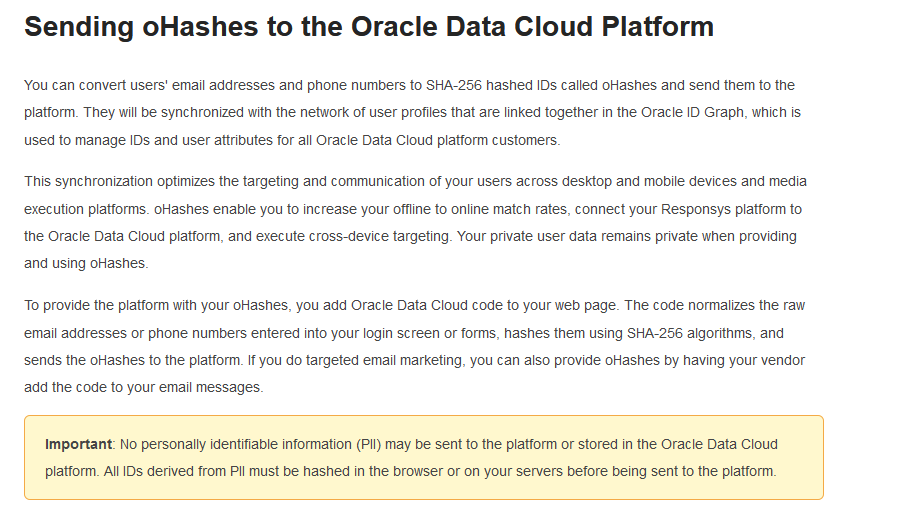
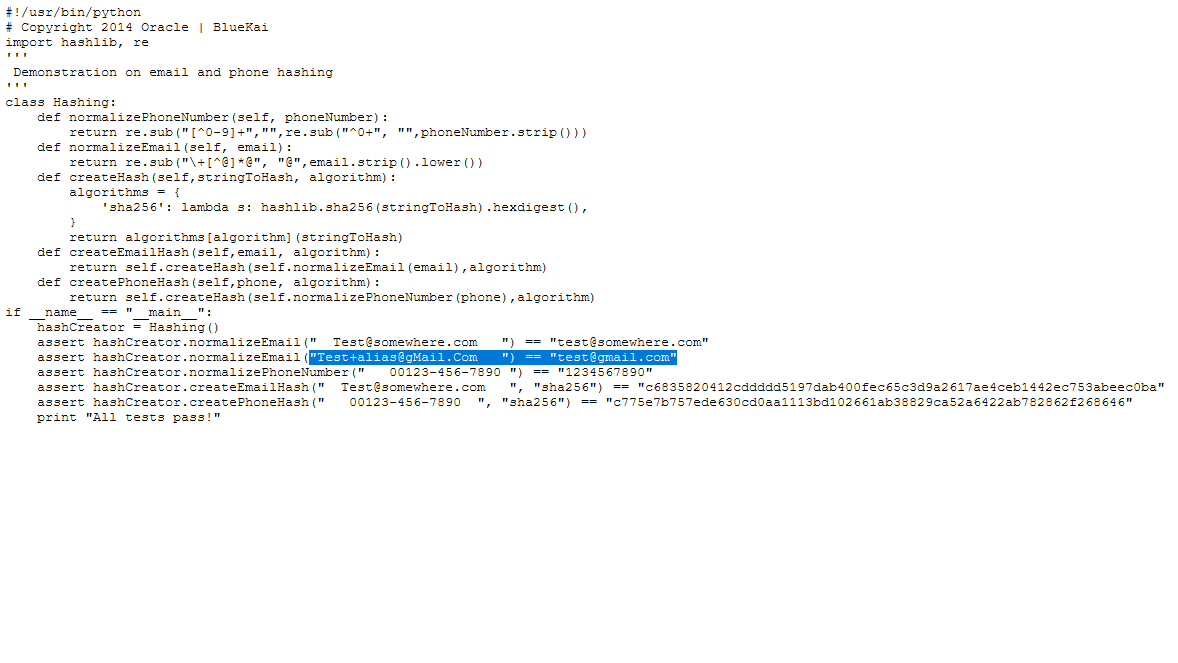
Convert "email addresses and phone numbers to SHA-256 hashed IDs" to synchronize them "with the network of user profiles that are linked together in the Oracle ID Graph". No "personally identifiable information"! docs.oracle.com/en/cloud/saas/…
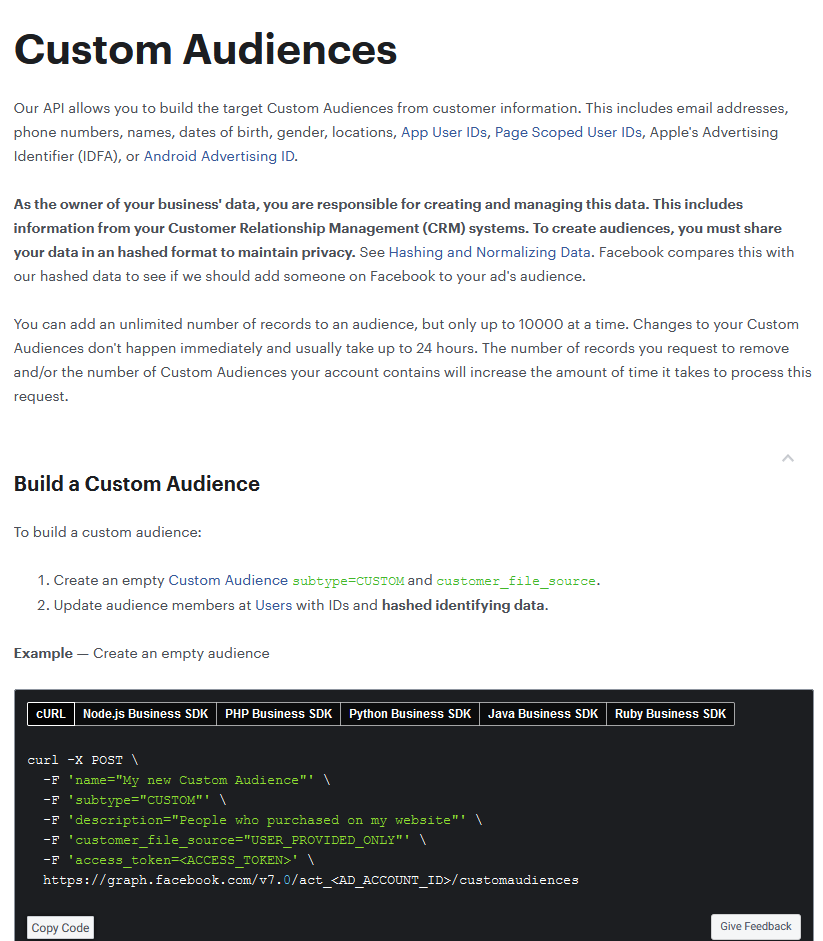
"you must share your data in an hashed format to maintain privacy"
developers.facebook.com/docs/marketing…
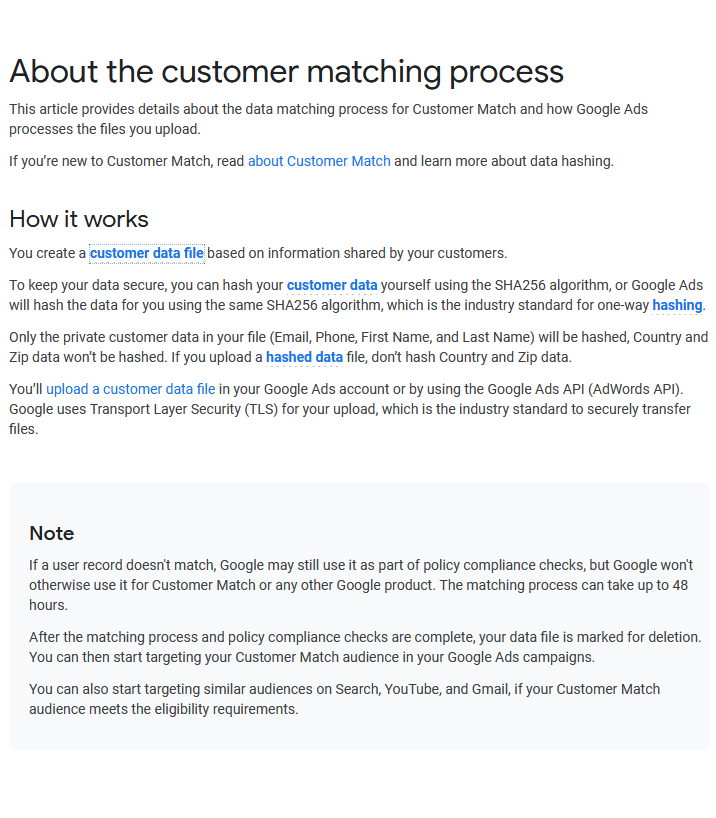
support.google.com/google-ads/ans…
And if personal data sharing based on pseudonymous identifiers would be discussed in the same way as sharing names or phone numbers.
docs.oracle.com/en/cloud/saas/…
docs.oracle.com/en/cloud/saas/…
Yes it's good to use a few different email addresses in different contexts but this cannot be fixed individually.
Recent state legislation has changed this, but details matter, also for federal regulation.
For example, Microsoft:
For example, this:
It covers just one specific use case, there are many other possible variants:
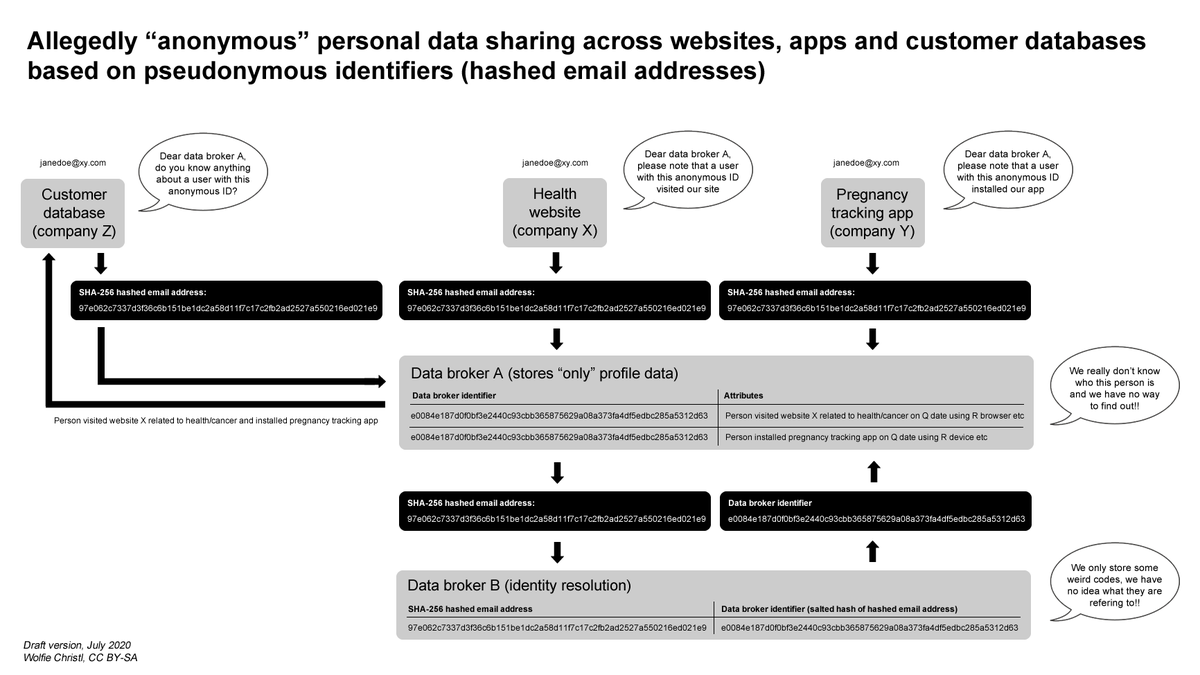
Data broker A stores "only" profile data linked to a proprietary ID, but relies on data broker B who 'translates' hashed email addresses into proprietary data broker IDs.
Data broker B is, for example, LiveRamp.
slideshare.net/mediapostlive/…
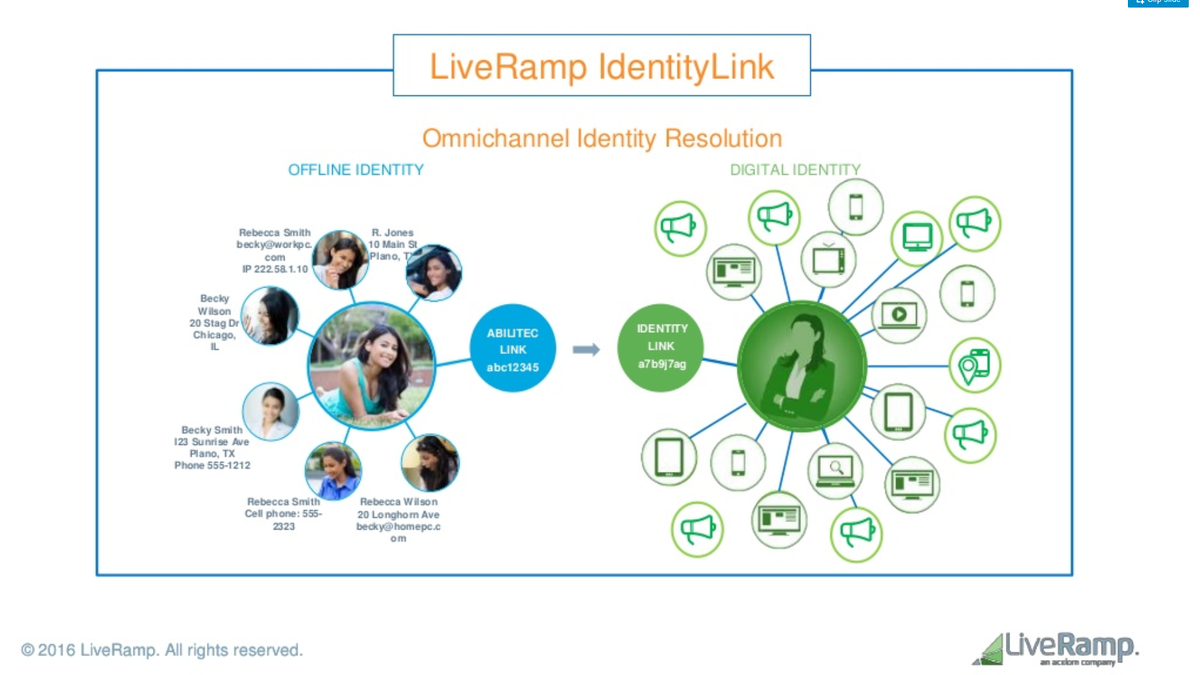
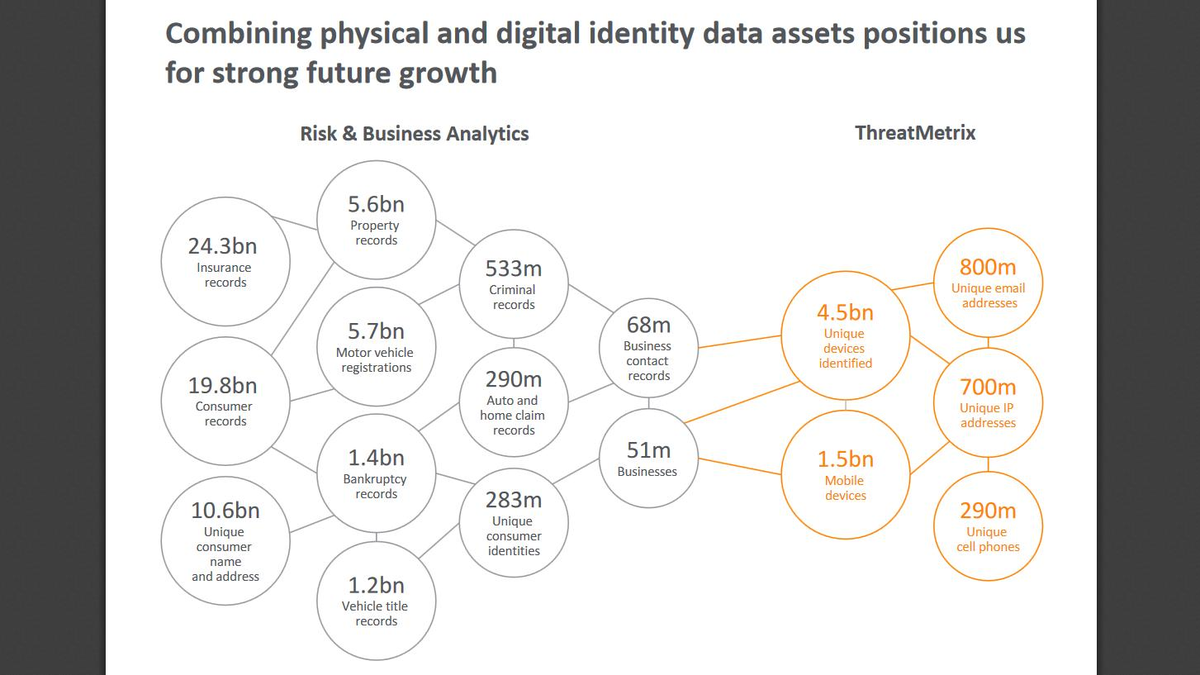
A smaller number of data brokers maintain comprehensive databases that link different personal identifiers referring to billions to each other.
martechtoday.com/whos-who-in-th…
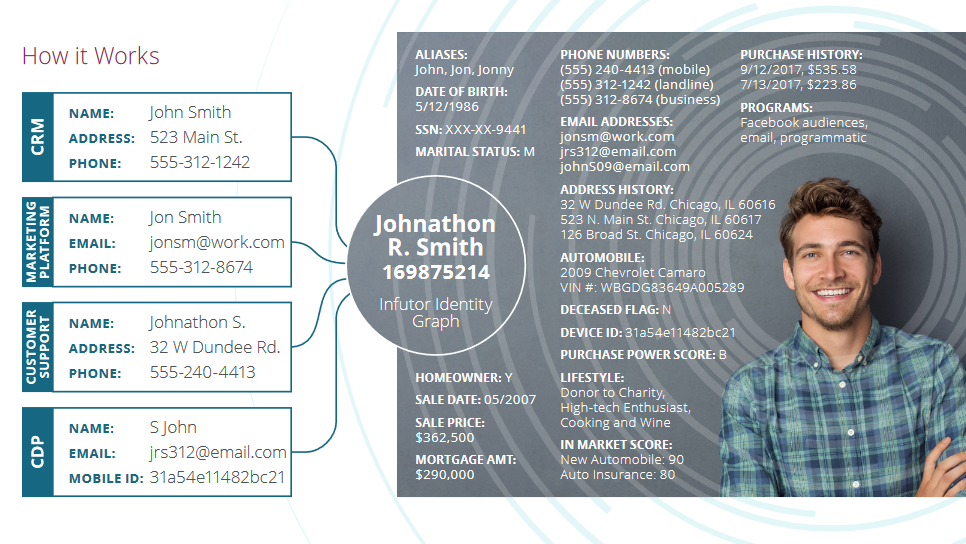
Everything totally anonymous!
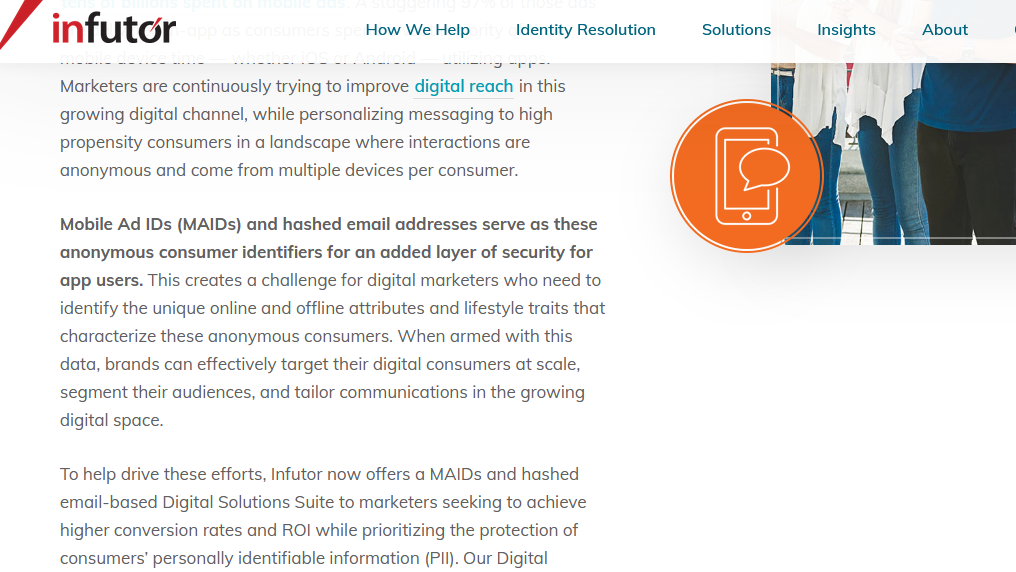
infutor.com/digital-soluti…