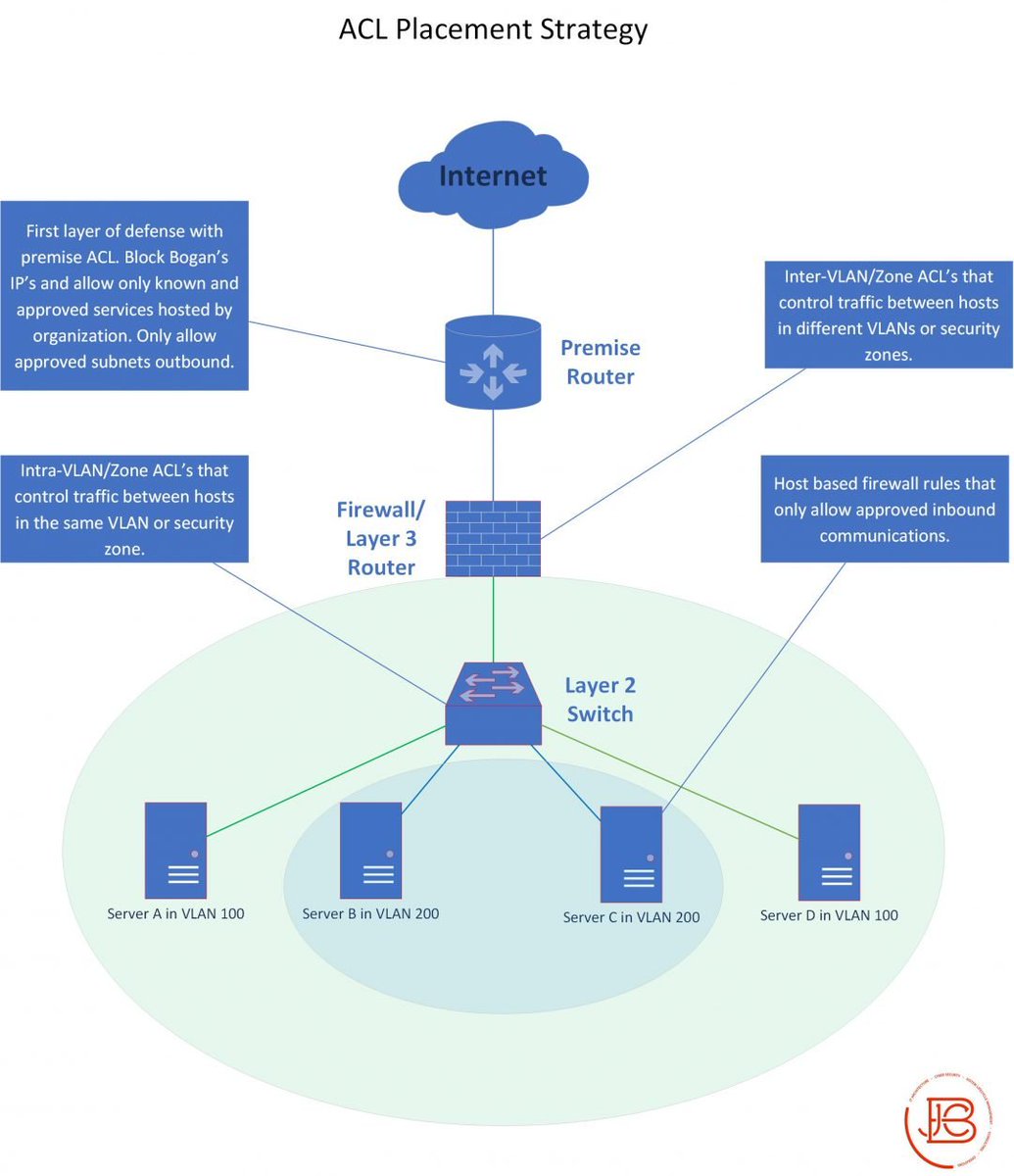
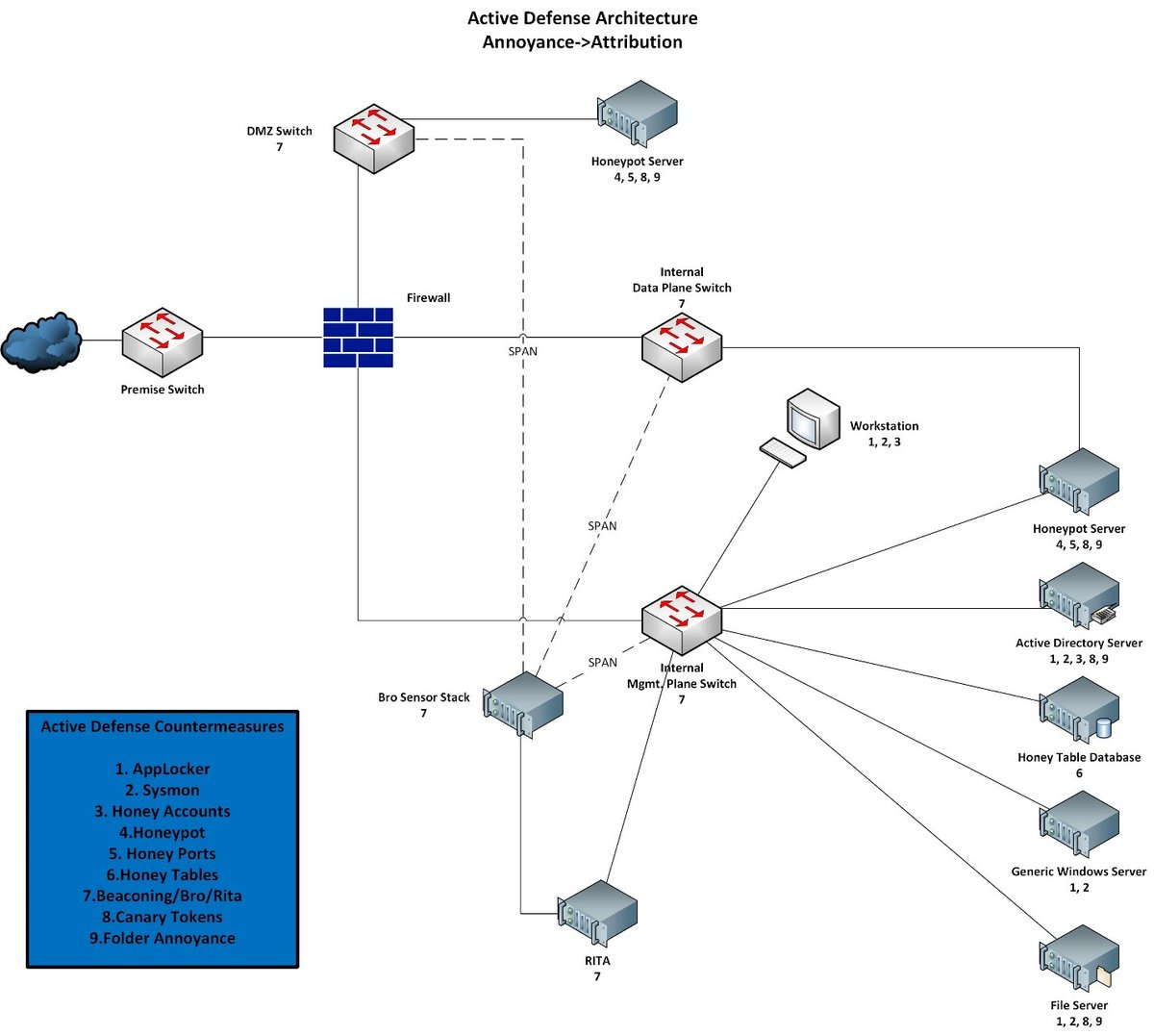
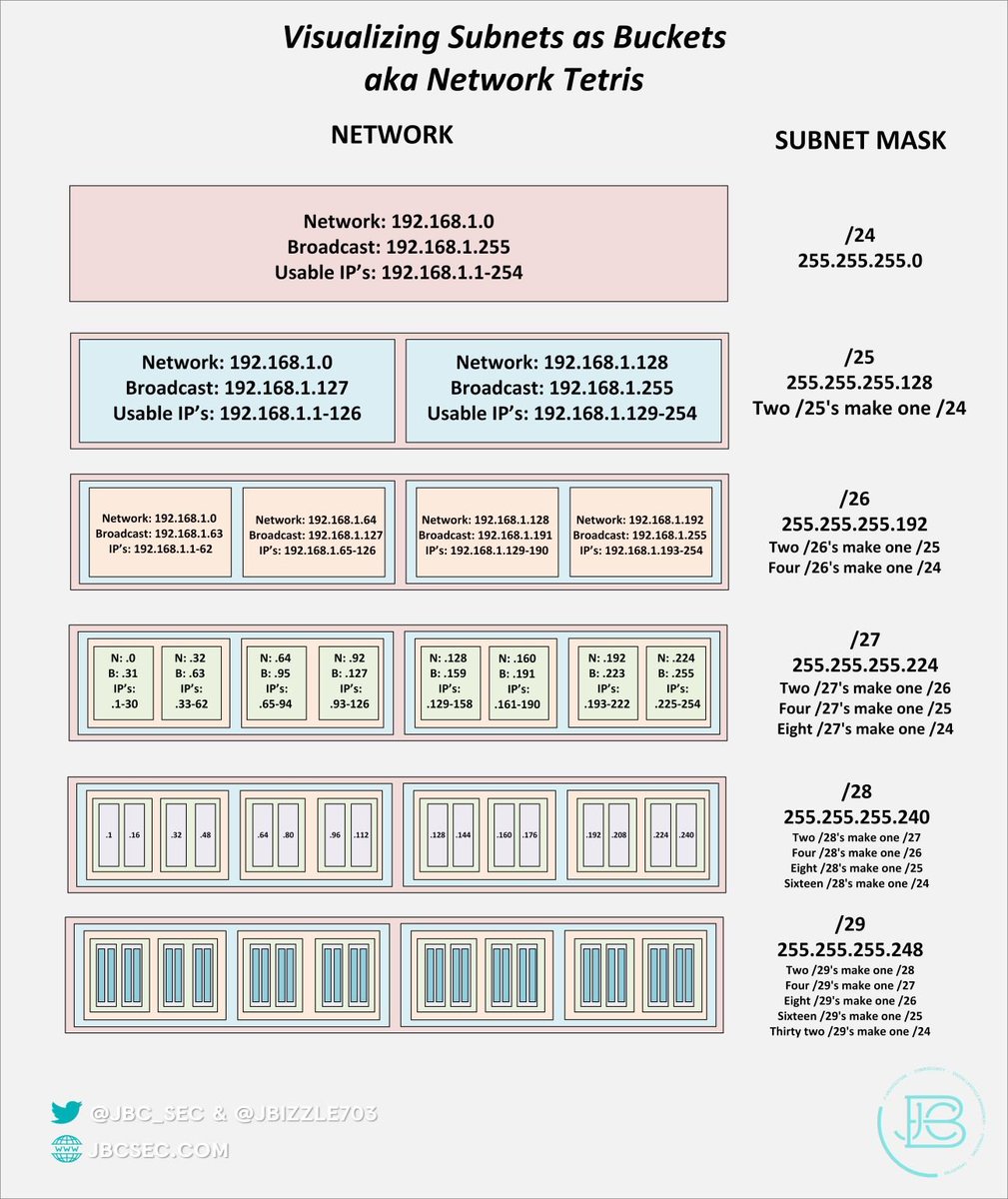
Next, Inter-Zone...
Ideally, if you are routing a lot of traffic through a firewall, this would be a perfect place to set up zone based rules between various security zones. The rules permit and deny communication between different subnets/VLANs/zones.
jbcsec.com/network-securi…
If you liked this, check out my YouTube channel : youtube.com/c/cyberinsight
Also, sign up for my blog and newsletter👍
mailchi.mp/e7b56addb7fc/c…
@ki_twyce_ @brianwhelton @bina_abdulrahim @NikkiMegaplaza @cachedchecks @AlmightyMek @nickrusso42518 @HugOfThunder @TayOnTech @varcharr