Shout out to @strandjs @BHinfoSecurity @ActiveCmeasures @corelight_inc
#30DaysofThreads
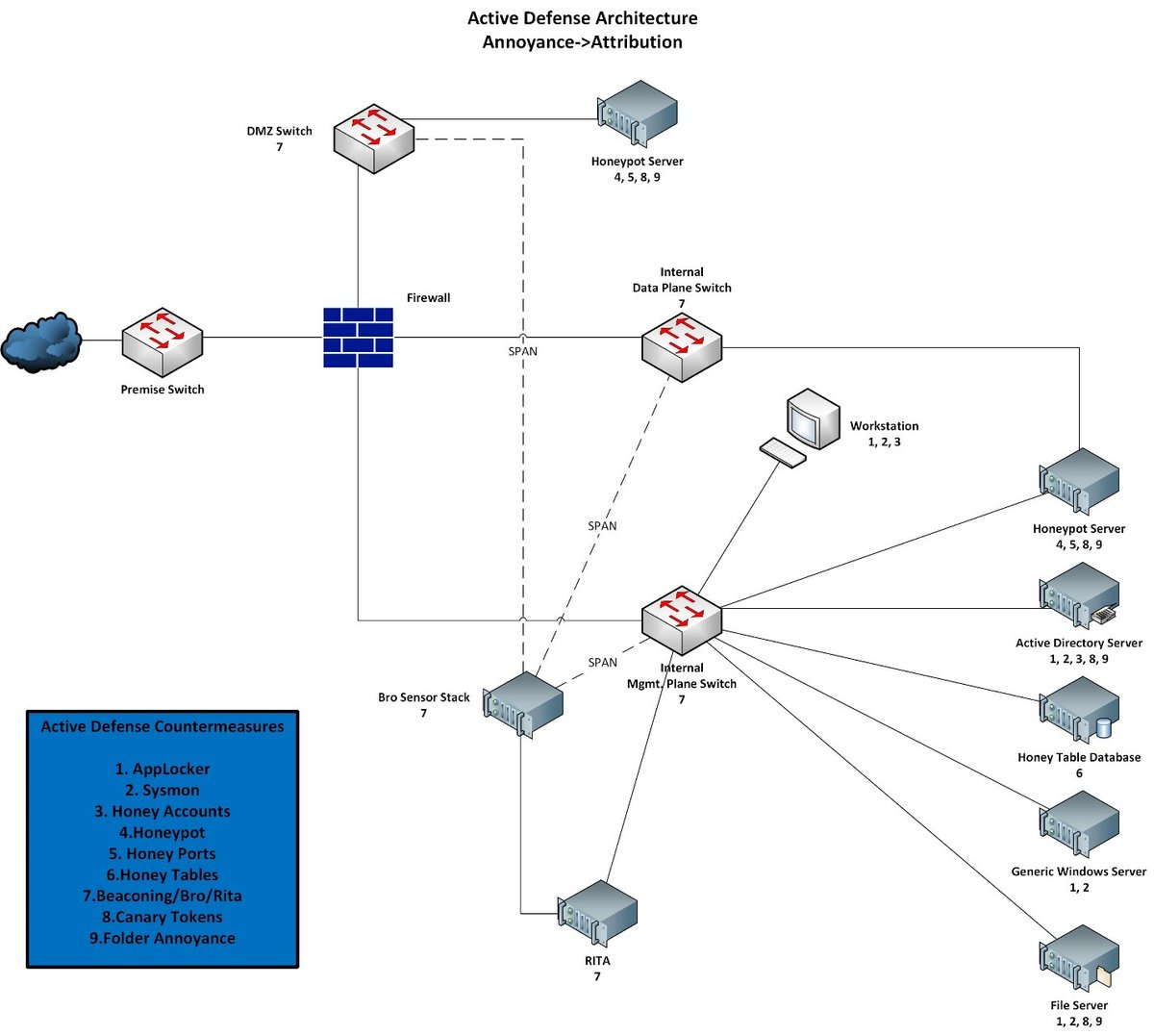
Purpose: Provides additional context and correlation that native Windows logging doesn’t provide natively.
Implementation: Implement on all Windows servers and workstations(if feasible). Logs can be fed to SIEM and alerts tailored
Purpose: Allows whitelisting and blacklisting of applications within the Windows environment. Can be in alert or blocking mode. Alerts can be set up whenever a block or non-approved software is ran.
Implementation: Implement on all Windows devices.
Challenges: Tuning to ensure that only the proper applications are allowed. Ensuring that the approved list is updated and that the certificate store that holds the certs to check for signing applications is monitored and protected.
Purpose: Accounts that are setup within the environment to look like critical accounts that should have a lot of permissions an attacker would want. Attackers will see and possibly attempt to use when pulling domain account lists due to intriguing username
Purpose: Server that provides level of deception that tricks attackers into thinking a server is vulnerable and has attractive open services. Further annoyance techniques can be set up to waste attackers time and resources.
Couple with honeypot. Listens on certain fake ports( provides fake information about what services are open), but only when a TCP connection is established, options are configured to alert and/or block the offending IP address via IP tables if desired.
Purpose: Create database table entries that are enticing on a honeypot or other database server and alert when someone access it.
Challenges: Ensuring that any tables added into active databases are configured to not allow additional access
Purpose: RITA is an open source framework for network traffic analysis. This open source project, born from Black Hills Information Security, is now developed, funded and supported by Active Countermeasures.
Beaconing Detection: Search for signs of beaconing behavior in and out of your network
DNS Tunneling Detection: Search for signs of DNS based covert channels
Blacklist Checking: Query blacklists to search for suspicious domains
Purpose: To create a document based honeypot. Fake documents are left in various areas around the environment with names/data that would entice an attacker. Document beacons back once opened giving IP of person who opened it(attribution).
Should review with security/legal before implementation.
Purpose: To annoy an attacker/waste their resources/time by creating a file/folder structure that continues to build on itself indefinitely. Alerting can be set up. Make sure it's not being scanned by AV, vulnerability scanner, and backups.
jbcsec.com/insights/
And sign up for my blog notifications and monthly newsletter 👍
mailchi.mp/e7b56addb7fc/c…