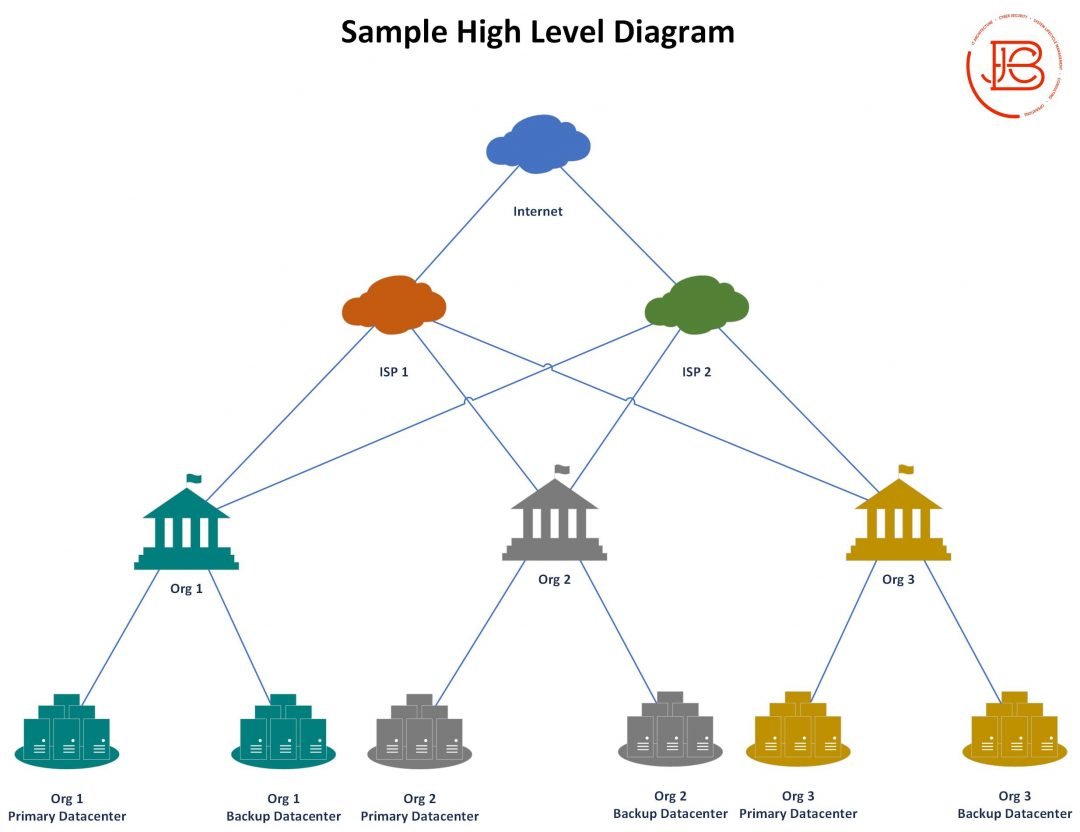
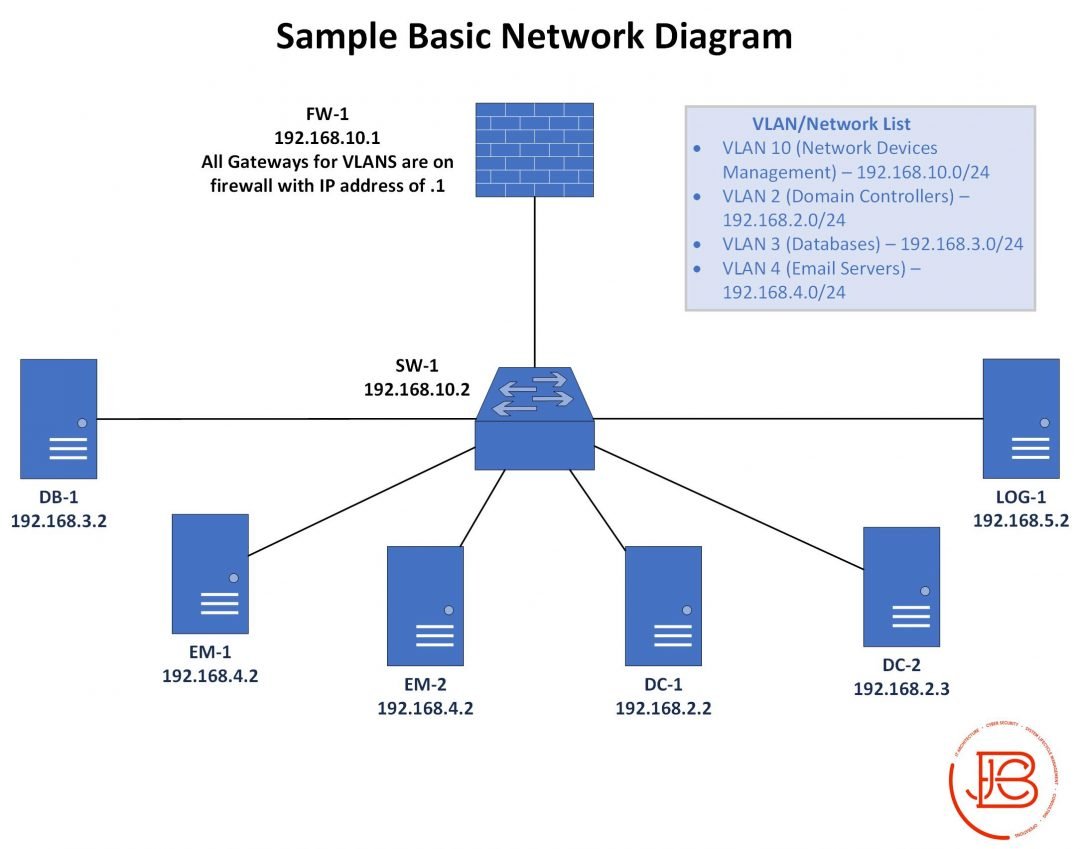
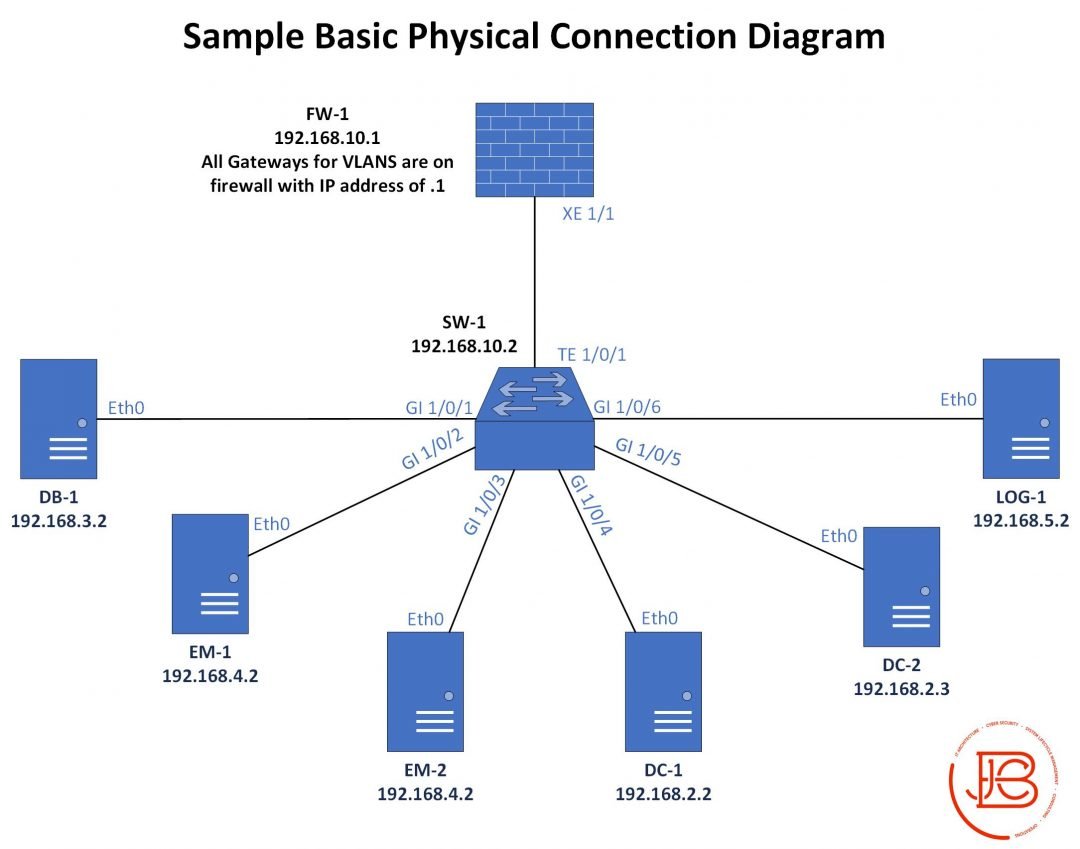
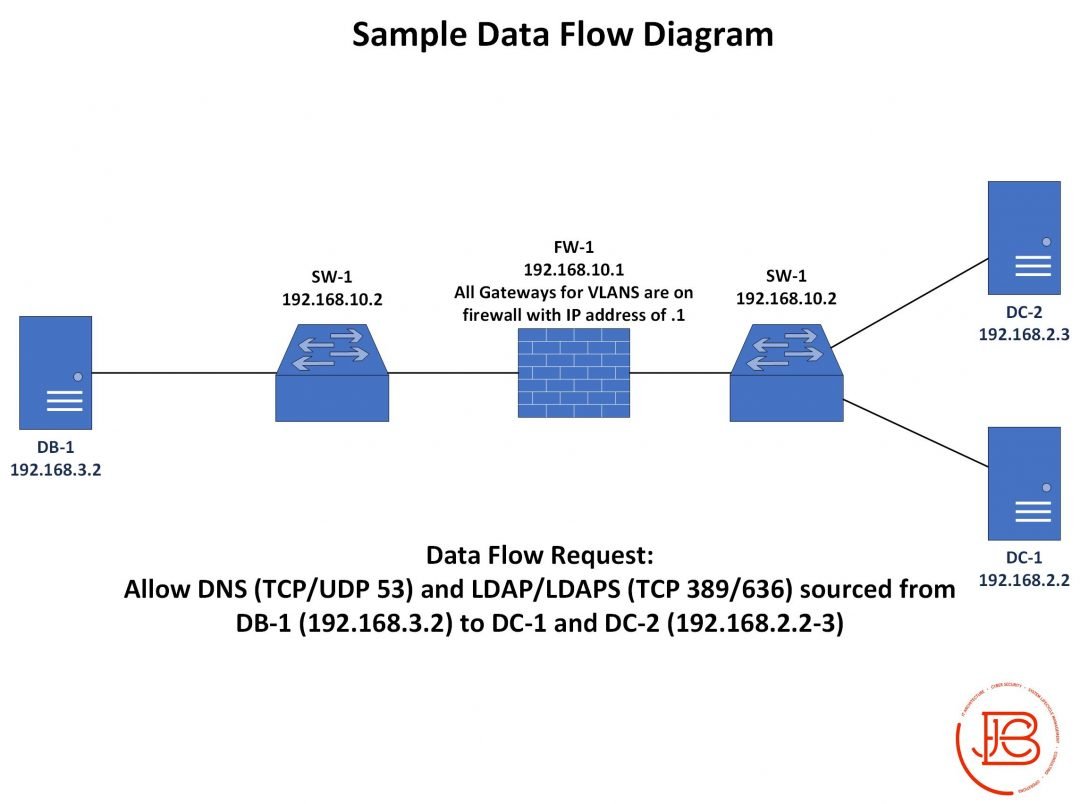
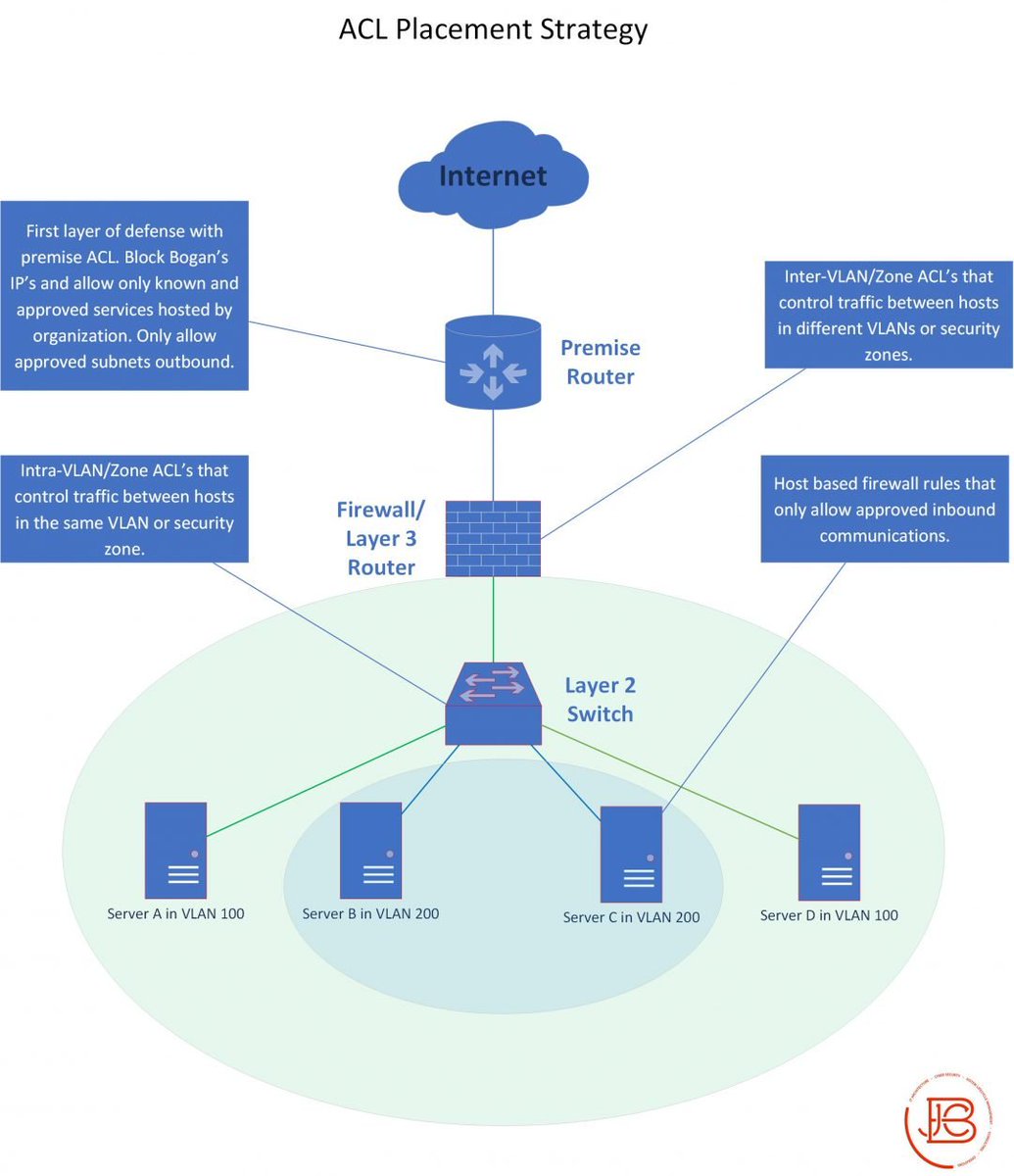
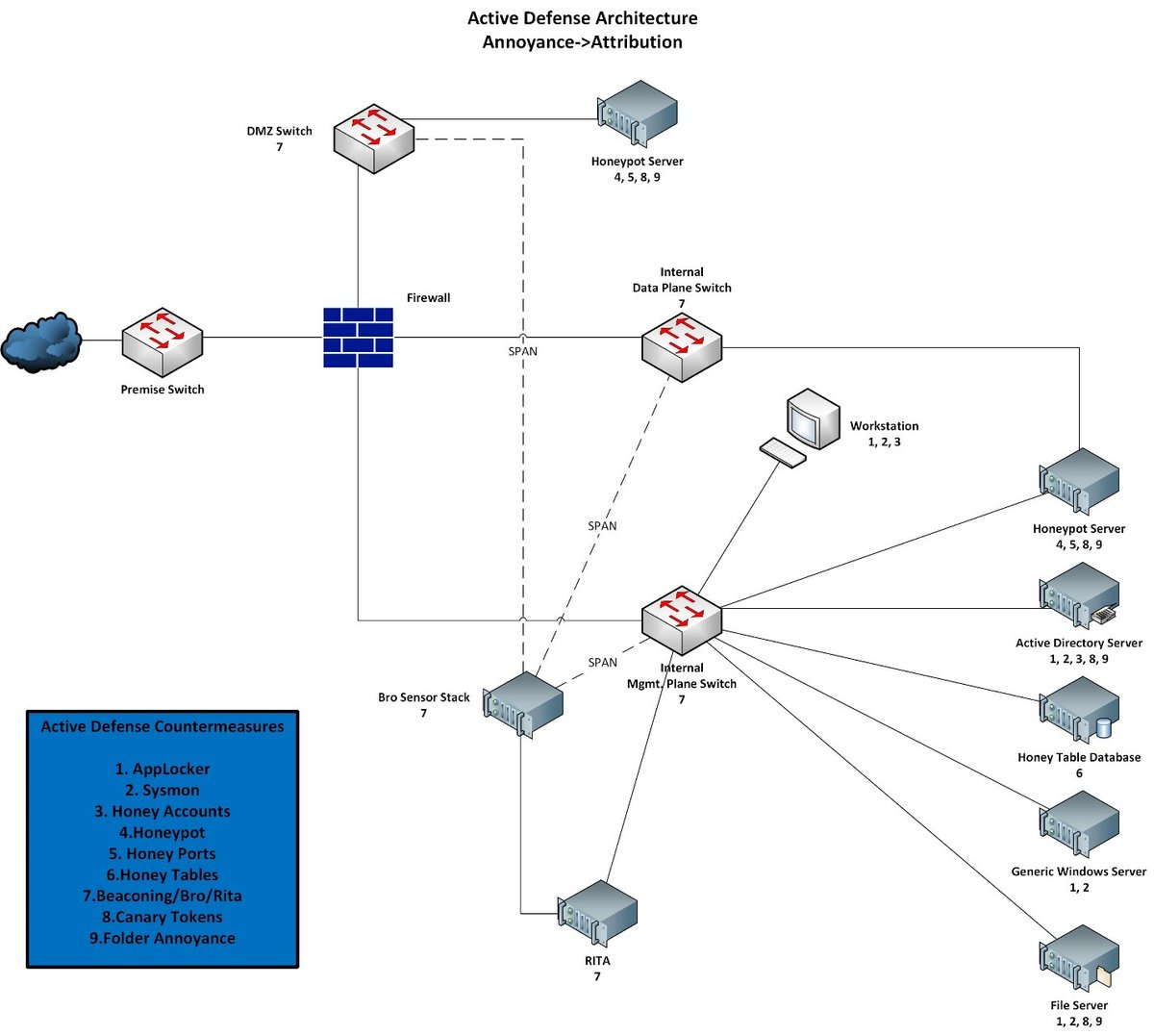
I've seen tweets recently from @gabsmashh and @TC_Johnson about wanting to nail down subnetting. I threw this little diagram together. For me, leaning to subnet took a combination of memorization and finally finding the right explanation that made it click.
#30DaysofThreads
#30DaysofThreads
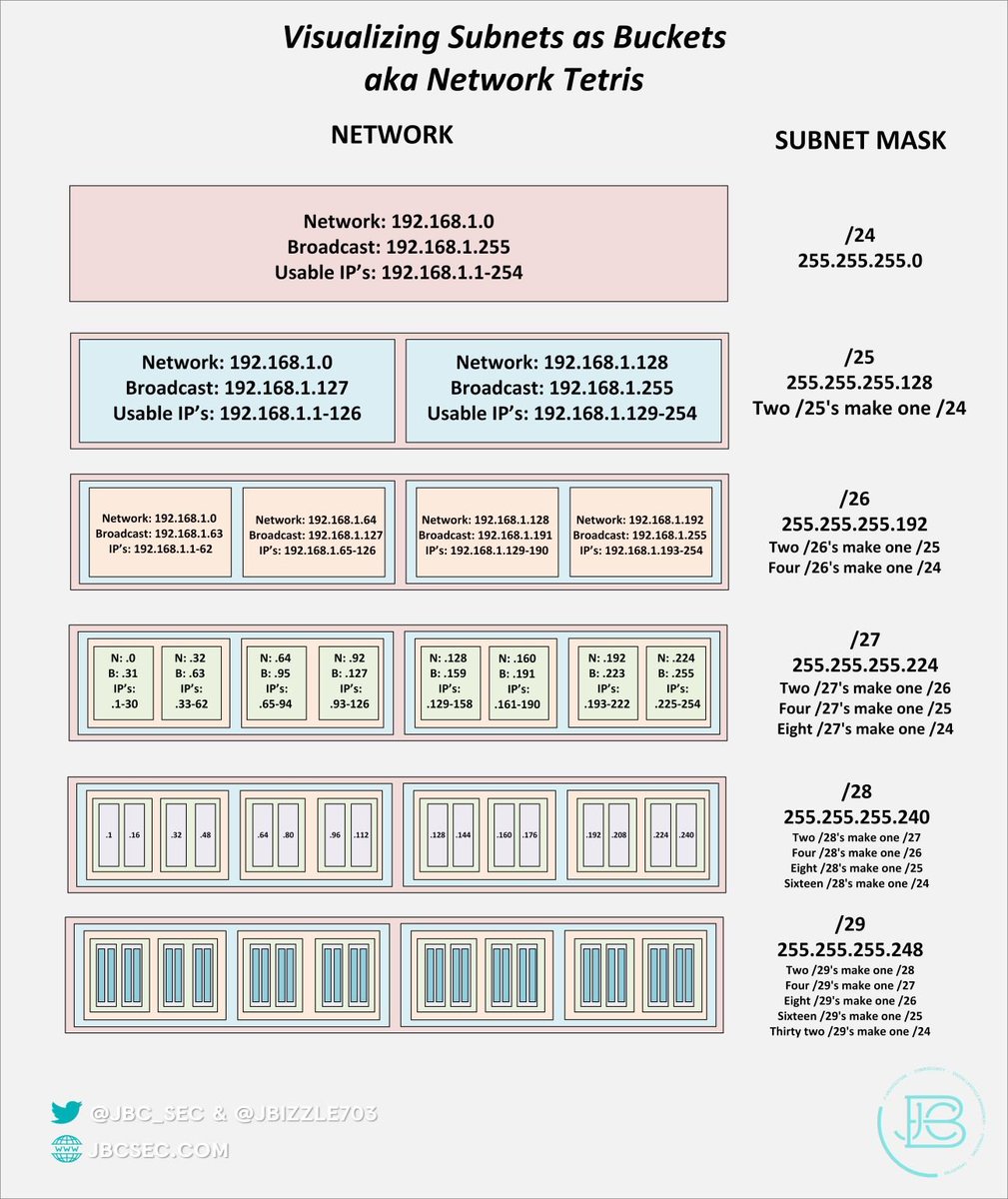
The thing that really clicked for me was understanding that each type of subnet (/24 for instance) is made up of multiple smaller subnets. And the address assignments or boundaries of these smaller subnets cannot change. You can't make a /26 network that bridges two /25's.
So, learning where these boundaries are is critical to learning how to do this all in your head. Also, remember that the first IP address in a network is always the network address and the last is the broadcast address. These are not usable IP's.
So what you're left with in between, is the usable IP range. In most instances one of those usable ones will be assigned as the gateway, and then rest will be used for whatever devices you want connected on that network.
If we start with the /24 network 192.168.1.X, we know that .0 and .255 can't be used since they are the network and broadcast address. If I need more networks, we break the /24 into a two /25's. Look at the diagram and you can see where those boundaries start and stop for a /25.
The other thing that helped make things click was that for every step going to the right(going from a /24 to /25 to /26...etc), you are doubling your initial number of networks but halving your number of IP's as they are now split between two networks.
Vice versa, for every step you go to the left ( going from a /29 to /28 to /27 ..etc) you are dividing the total number of usable networks you have by 2. So if you had two /29's and they fell within the IP space(the boundary) of a /28, you could combine them into one /28 network.
It really is all about memorization of block sizes, and then dividing or multiplying by two when moving between subnet sizes and remembering the first and last IP's of a subnet cannot be use. Happy to talk to folks who have questions👍
Check out my blog where I cover more topics 🔥
jbcsec.com/insights/
And sign up for my blog notifications and monthly newsletter 👍
mailchi.mp/e7b56addb7fc/c…
jbcsec.com/insights/
And sign up for my blog notifications and monthly newsletter 👍
mailchi.mp/e7b56addb7fc/c…
I did want to make one little correction to the diagram, I had a "1" for the first subnet under the /28's and it should have been a "0". I also added the total number of IP's in each subnet size. 

Also, check out this new thread on supernetting!
https://twitter.com/JBizzle703/status/1214187278433705984?s=20
• • •
Missing some Tweet in this thread? You can try to
force a refresh