There's a tricky way to create a new user on a Windows host without it being displayed by the "net" utility. This is something @Ben0xA tweeted about very recently.
I wanted to find out why a user named "$" is not shown, and here's what I learned :) [1/5]
I wanted to find out why a user named "$" is not shown, and here's what I learned :) [1/5]
https://twitter.com/Ben0xA/status/1301550957516541952
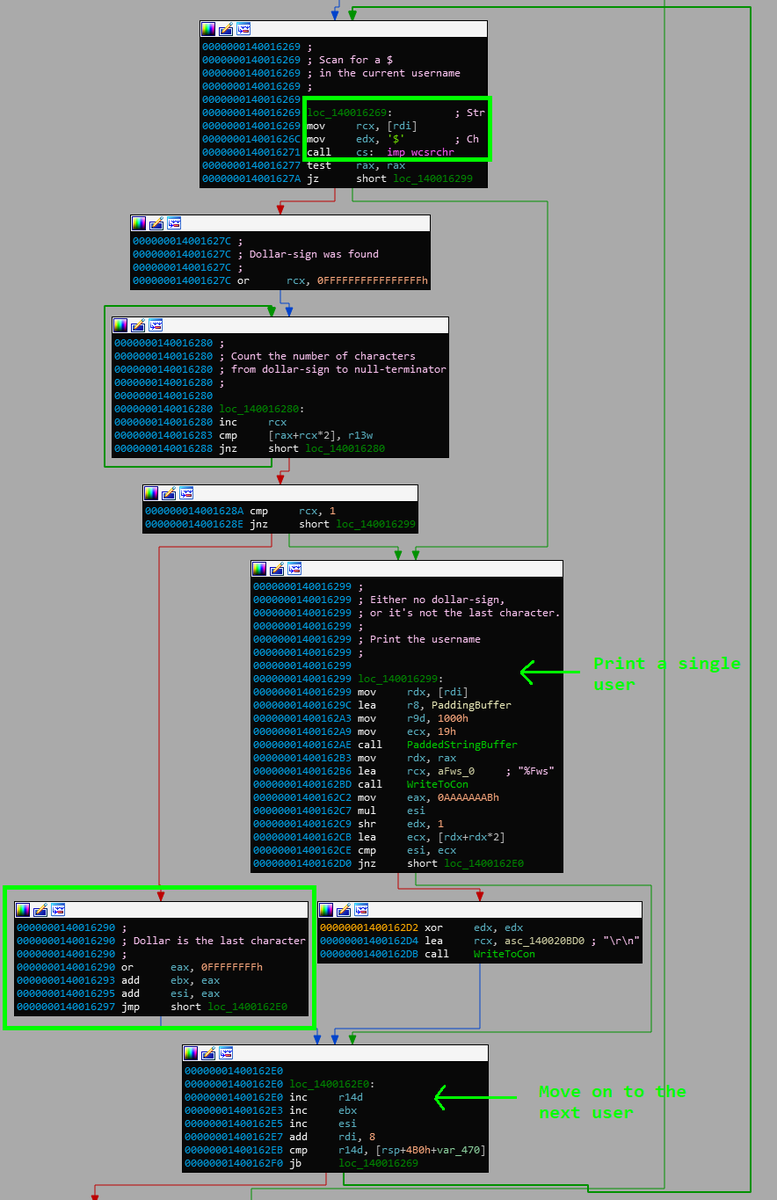
net.exe checks if the username contains a dollar sign. If it does, *and* the dollar sign appears at the end -- the username is not printed but simply skipped. This is probably because ending an account name with "$" may indicate a computer name, and not a human user. [2/5] 
In Powershell, usernames ending with $ *do* show in the output of Get-LocalUser cmdlet, although Powershell uses the same source - SAM's (Security Account Manager) user enumeration. It simply doesn't use the "$-at-the-end" heuristic, and displays all user objects returned. [3/5] 

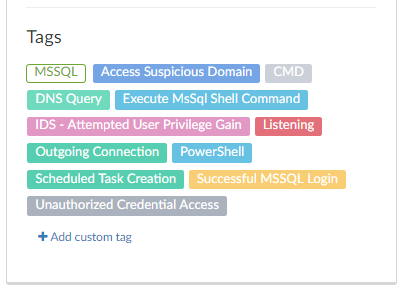
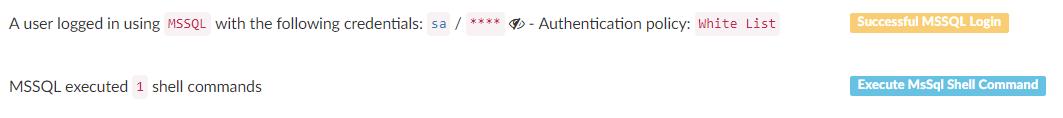
Attackers know this nice, silent backdoor (@PashaGur, this should answer your question); @Guardicore's sensors captured 30 different usernames ending with $ created as part of attacks, 5 of them this year.
Here's one example of such an attack - threatintelligence.guardicore.com/ip/14.241.36.30 [4/5]
Here's one example of such an attack - threatintelligence.guardicore.com/ip/14.241.36.30 [4/5]

There are more thorough ways - Powershell is just one of them - to list user accounts on your host than running "net user". Choose them :) [4/5]
https://twitter.com/Ben0xA/status/1301558235963494402
• • •
Missing some Tweet in this thread? You can try to
force a refresh