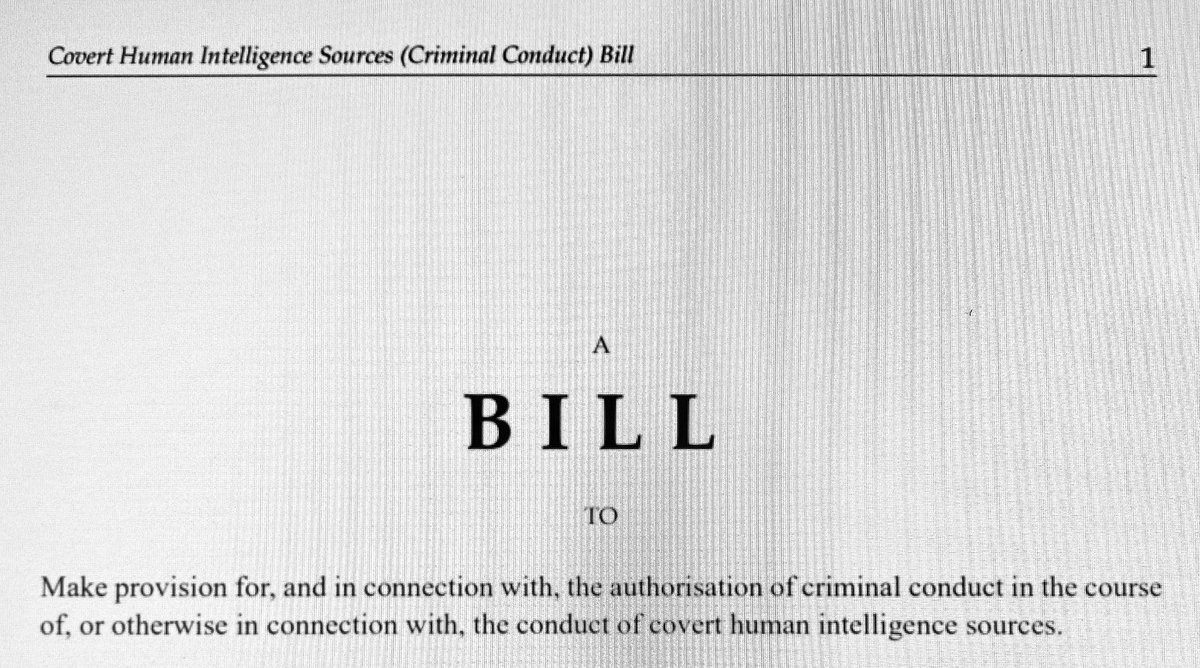
Here are my thoughts on the super-sensitive CHIS (Criminal Conduct) Bill #CHISBill, published today in time (just) for 2nd reading in @HouseofCommons on Monday assets.publishing.service.gov.uk/government/upl…. /1
CHIS = covert human intelligence source legislation.gov.uk/ukpga/2000/23/…: put simply, an agent who for whatever reason (personal, financial, even patriotic) agrees to help the police, MI5 or others spy on suspected criminals. They are authorised under #RIPA legislation.gov.uk/ukpga/2000/23/… /2
CHIS play a vital role in disrupting terrorism and organised crime. Over the past year, CHIS operations by @metpoliceuk alone are claimed to have led to 3500 arrests, recovery of 100 firearms and 400 other weapons, seizure of 400 kg of Class A drugs, and £2.5m cash. /3
But what happens if a CHIS (e.g. to maintain cover) takes part in the criminality they are supposed to be informing on - by helping a banned terror group, handling stolen goods, supplying drugs - or worse? /4
Under the so-called "James Bond clause", MI6 agents can be authorised to break UK law abroad: legislation.gov.uk/ukpga/1994/13/…. But police/spooks pre-authorising people to break UK law in the UK? That sounds different. /5
Last December, the Investigatory Powers Tribunal was divided on the issue of whether MI5 had an implied statutory power to authorise CHIS participation in criminality judiciary.uk/wp-content/upl… /5
The stakes were high - just look how the judgment started. Especially as the power is claimed not just by MI5 (as in that case) but by @HMRCgovuk, @NCA_UK, several other public authorities and every police force in the land. /6 

The Government won 3-2, but the case is being appealed and no one could be confident of the result. So the Government has decided to seek Parliament's express authority, in the form of #CHISBill. /7 
They are right to do so. Police and security forces must always have a democratic licence to operate. It's (to coin a phrase) A Question of Trust …egislationreviewer.independent.gov.uk/wp-content/upl…. /8
But Parliament also has a duty to scrutinise this Bill. Here are a few questions that colleagues in @HouseofCommons and then @UKHouseofLords will want to ask. /9
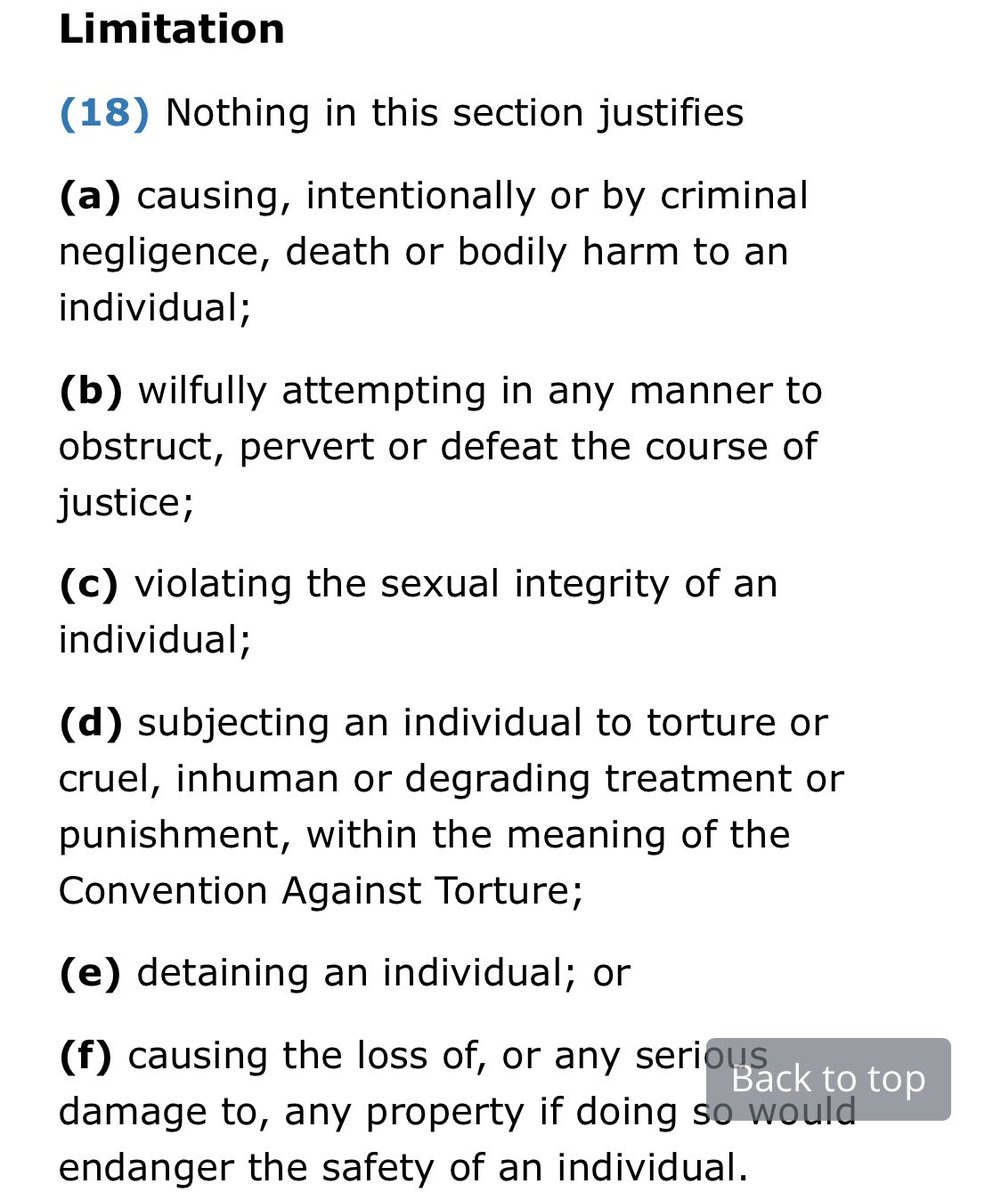
First, are we happy that all these bodies need not only to be able to run CHIS, but to authorise criminality by them? /10 

Secondly, are we content that the processes for authorising CHIS to commit crime are sufficiently sound - in every one of these bodies, not just the biggest? The bottom line is self-authorisation with internal safeguards: lots of detail here. assets.publishing.service.gov.uk/government/upl…. /11
Thirdly, should the Act at least specify types of serious crime that can never be authorised? The Canadian CSIS Act s20(1) canlii.org/en/ca/laws/sta… does (how's it working, @cforcese?) Or would hard limits allow gangs to smoke out CHIS by inviting them to step over the line? /12
Fourthly, how does all this square with human rights? The Government has set the ball rolling here: publications.parliament.uk/pa/bills/cbill…. /13
Finally, it's great that @IPCOffice will be keeping an eye on the use of these powers - after the event. /14 

But should they be entrusted either with prior approval of authorisations (as for some other forms of covert surveillance, such as phone-tapping) legislation.gov.uk/ukpga/2016/25/… ... /15
... or at least be notified of authorisations in real-time, so that they can raise the alarm if someone is way out of line? /16
To recap - the principle of this Bill deserves our strong support. But the detail matters, and we need to apply ourselves to it. /17 end
Further, critical thread here
https://twitter.com/thebrieftweet/status/1309504217795698689?s=20from @thebrieftweet
• • •
Missing some Tweet in this thread? You can try to
force a refresh