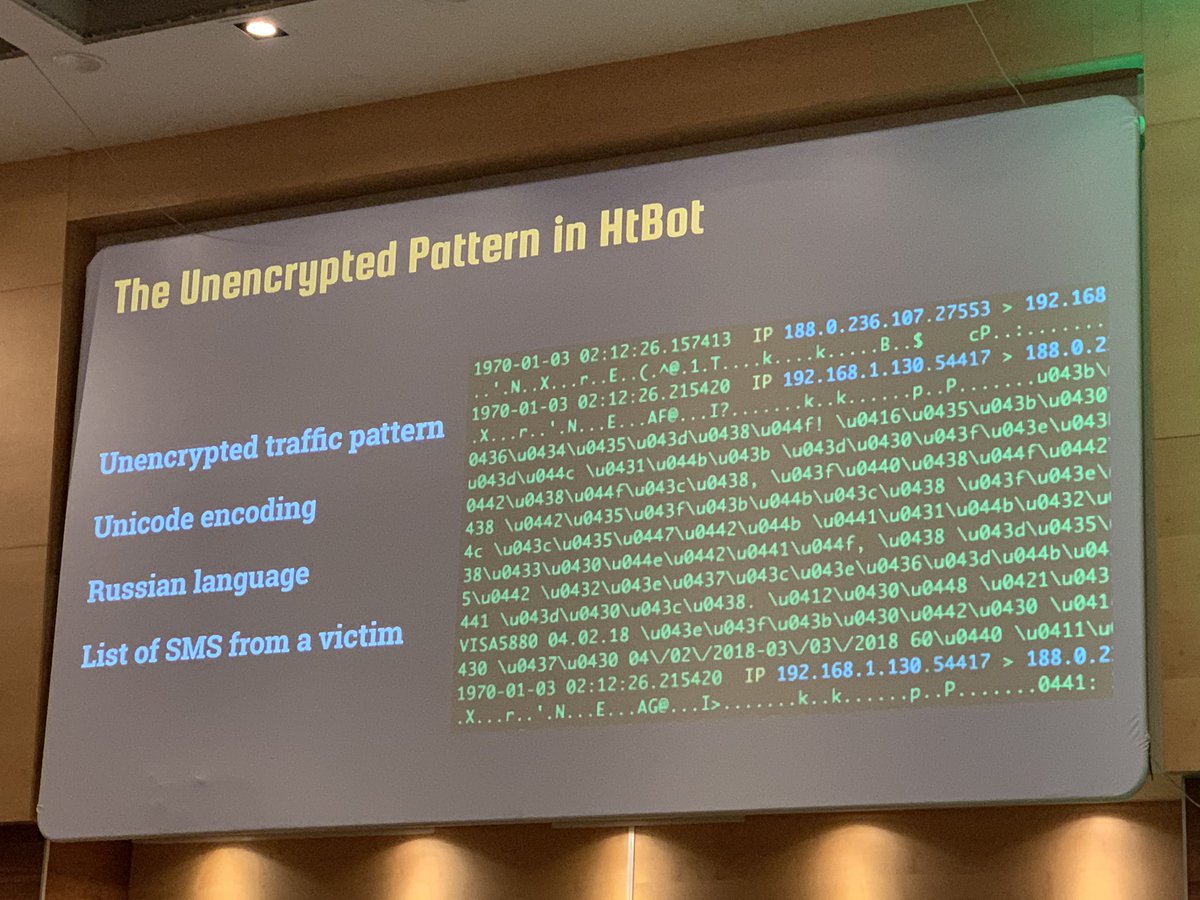
Friday night, playing again with #honeypots <3 
The installation was very smooth, and the end result is neat. Don't try to run this with 4GB of memory, because is not gonna work. T-Pot requires at least 8GB (note to self: rtfm). 

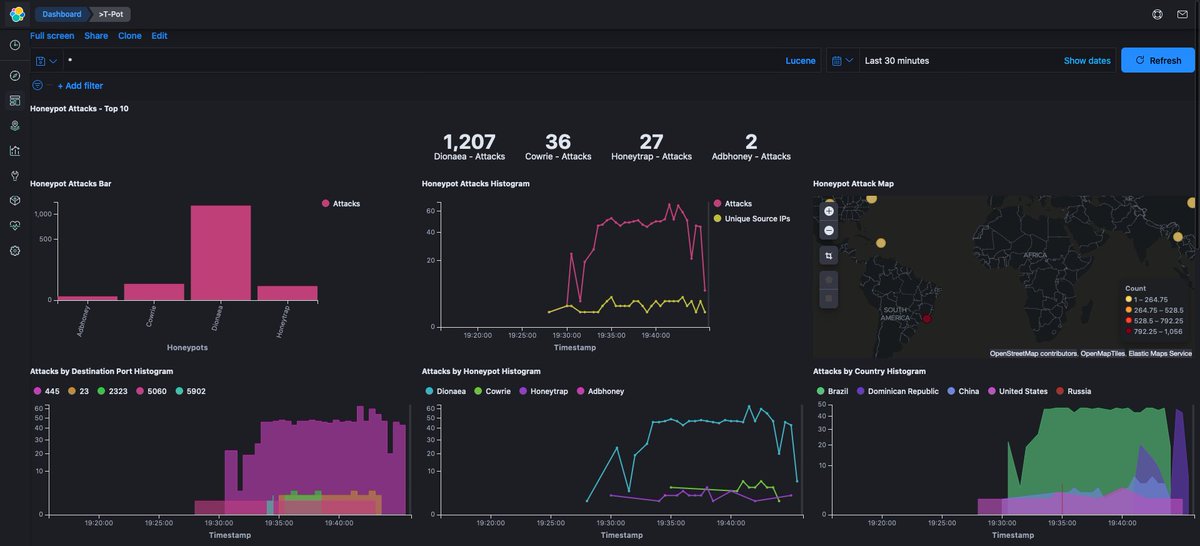
The number of attacks received always impresses me. Less than 45 minutes minutes after installation and the numbers are staggering.
👉🏿5,030 Dionaea attacks
👉🏿1,375 Cowrie attacks
👉🏿5,030 Dionaea attacks
👉🏿1,375 Cowrie attacks
The morning after deploying honeypots is like Christmas. Wake up early, way too excited to see what gifts are there for you!
For those interested, I installed a full version of T-Pot (@dtag_dev_sec). The server(s) were I've this installed has 8GB RAM/4CPU. T-Pot has around 20 different honeypots, an ELK suite, and pre-built Kibana dashboards. T-Pot GitHub repository is: github.com/telekom-securi…
Already having Kibana loading issues. It's incredible how much memory it requires. 8GB seemed enough, but now it's just struggling to load.
Alright, here we go. At least one dashboard loaded. An all time low around 1am, but got more active after that. This is after 14 hours since start time. 



I was expecting numbers to be higher by now.
Interesting related paper that uses T-Pot data as their dataset: "Identifying Attack Propagation Patterns in Honeypots using Markov Chains Modeling and Complex Networks Analysis" (2016)
cyber.bgu.ac.il/wp-content/upl…
cyber.bgu.ac.il/wp-content/upl…
48 hs later, the Kibanas are completely unresponsive, the memory of the servers is completely depleted and I am almost unable to type commands via ssh because is super slow. Probably more than 8GB of memory are needed to run this for longer times.
It seems the real memory issue is due to log stash, not kibana. And that's a component you probably do not want to turn off. I see no real solution here except increasing memory, which is costly.
After a week, 3 out of 5 T-Pot installations crashed, and therefore stopped collecting data. Memory issues. The instances, all the same specs, had 8GB of RAM. The other two instances struggled but somehow survived. A quick walkthrough the observed attacks 👇🏿 

Attacks per honeypot:
Dionaea - Attacks: 272,295
Cowrie - Attacks: 65,919
Honeytrap - Attacks: 18,260
Rdpy - Attacks: 7,510
Heralding - Attacks: 7,137
Mailoney - Attacks: 775
Adbhoney - Attacks: 274
Tanner - Attacks: 171
Ciscoasa - Attacks: 131
CitrixHoneypot - Attacks: 78
Dionaea - Attacks: 272,295
Cowrie - Attacks: 65,919
Honeytrap - Attacks: 18,260
Rdpy - Attacks: 7,510
Heralding - Attacks: 7,137
Mailoney - Attacks: 775
Adbhoney - Attacks: 274
Tanner - Attacks: 171
Ciscoasa - Attacks: 131
CitrixHoneypot - Attacks: 78
Dionaea is, as usual, the most attacked. The majority of attacks coming from Vietnam, India, and Indonesia. 



Cowrie, has a good 65,919 attacks. This seems a bit low for what we are used to see on SSH/Telnet ports. Surprisingly (?) most of the attacks are coming from Ireland, Russia, and Panama. 

Adbhoney received 274 attacks. Again most attacking IPs are well known offenders. Most attacks coming from China, South Korea, and Russia. 

The Ciscoasa honeypot received 131 attacks. Interestingly, most attacks coming from a single country: US. 

Heralding honeypot received 7,137 attacks. The majority of attacks coming from Republic of Moldova and Seychelles. These two IPs attacking are well known offenders. 

The end. EOM.
• • •
Missing some Tweet in this thread? You can try to
force a refresh