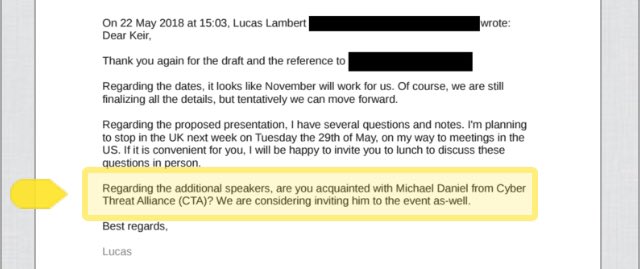
Here's the @Reuters story on today's hastily convened press conference blaming Iran for the 'Proud Boys' email threats.
reuters.com/article/us-usa…
I note these paragraphs in particular:
reuters.com/article/us-usa…
I note these paragraphs in particular:

As Dimitri - who knows a thing or two about publicly blaming a foreign power for election cyber mischief! - notes, this was a *blisteringly* fast attribution:
https://twitter.com/DAlperovitch/status/1319078728228433921?s=20
I dunno what the evidence is - it hasn't been made public - so maybe there's a slam-dunk somewhere.
As many have noted, Iranian cyber ops aren't exactly watertight & Tehran-linked hackers regularly make disastrous mistakes. wired.com/story/iran-apt…
As many have noted, Iranian cyber ops aren't exactly watertight & Tehran-linked hackers regularly make disastrous mistakes. wired.com/story/iran-apt…
But then again ...
reuters.com/article/us-rus…
reuters.com/article/us-rus…
• • •
Missing some Tweet in this thread? You can try to
force a refresh