
I'll attempt to live tweet this awesome webcast from @Wanna_VanTa and @x04steve on Ryuk and UNCs behind them! Roughly 1/5 ransomware intrusions have been related to Ryuk. @Mandiant @sansforensics 

So what's an UNC? UNC = "uncategorized" - a way to cluster unique activity that is fundamentally related. They're "labels" or "buckets". UNCs might become FINs or APTs someday, but that requires time. 

Van mentions one of my favorite blog posts, by Matt Berninger: fireeye.com/blog/threat-re…
Not all Trickbot is UNC1878!!! This is such an important point. Don't attribute to actors based SOLELY on the tool they use.
Our first mention of Cobalt Strike. Used in EVERY INTRUSION. You need to know how you can detect this. Look into Malleable C2 Profiles. Code signing certs are a great place to look too. 



Can confirm, these are super common credential access and lateral movement techniques...for UNC1878 and other actors too. ADFind is a good one to look for and might be rare in your environment. 

Note how much of what UNC1878 uses is open source. This gives defenders the chance to dive into the code and make better detections. 

What happened over the summer? They're not sure, but the data clearly shows RYUK has returned. But does that mean UNC1878 has returned? Maybe, but DON'T ATTRIBUTE BASED ON MALWARE FAMILY ALONE. AGAIN FOR THE FOLKS IN BACK....DON'T. ATTRIBUTE. ON. MALWARE. FAMILY. ALONE. 

Some things are similar to previous activity, some are different...Kegtap has replaced Trickbot. Cobalt Strike isn't quite the same as it was a few months ago. 

Diving into attribution...it can be so useful to compare activity over time and look for similarities and differences. 
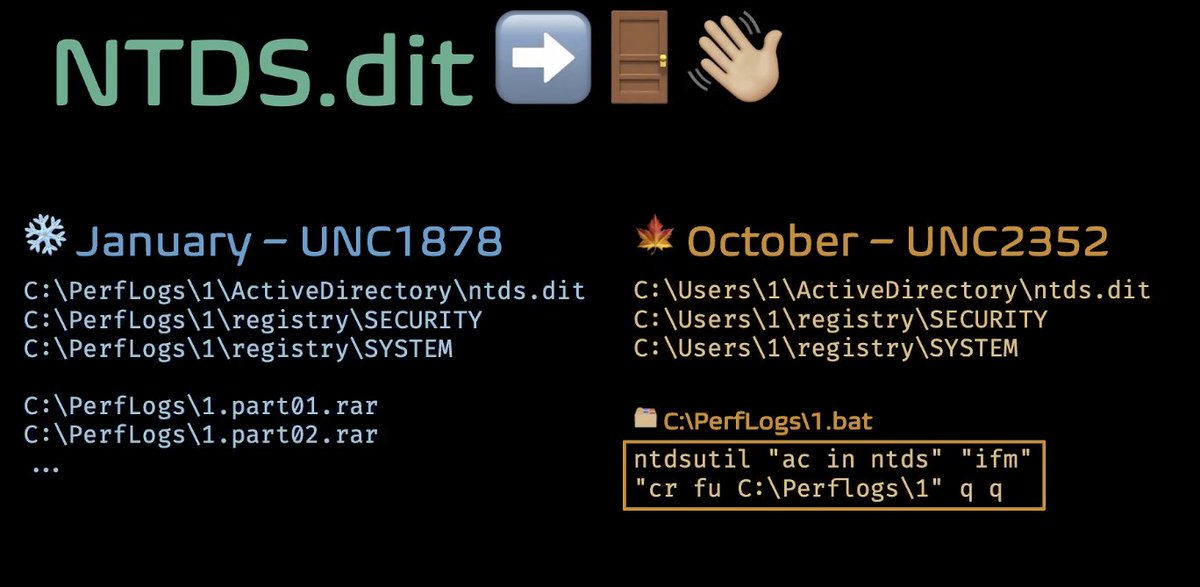
Use of WMI plus shared folder and BITSadmin...ALMOST the same commands. Check out vVv and xxx. This is a strong overlap between UNC1878 and UNC2352. 

Ultimately these UNCs were merged. It may seem like a lot of work for something "obvious", but sometimes it takes time to build confidence. THIS IS A KEY POINT FOR INTEL ANALYSIS!!! We shouldn't just accept our "gut feelings" - that's where cognitive biases come in. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh












