1/ Not in the least bit, and the protocol isn't really designed to operate like Bitcoin (since Bitcoin was created for peer-to-peer payments).
Also, the upside for what Ethereum can / can't do seems to be a hell of a lot more limited than it is for Bitcoin (ironically).
Also, the upside for what Ethereum can / can't do seems to be a hell of a lot more limited than it is for Bitcoin (ironically).
https://twitter.com/RyanSAdams/status/1323666067785482240
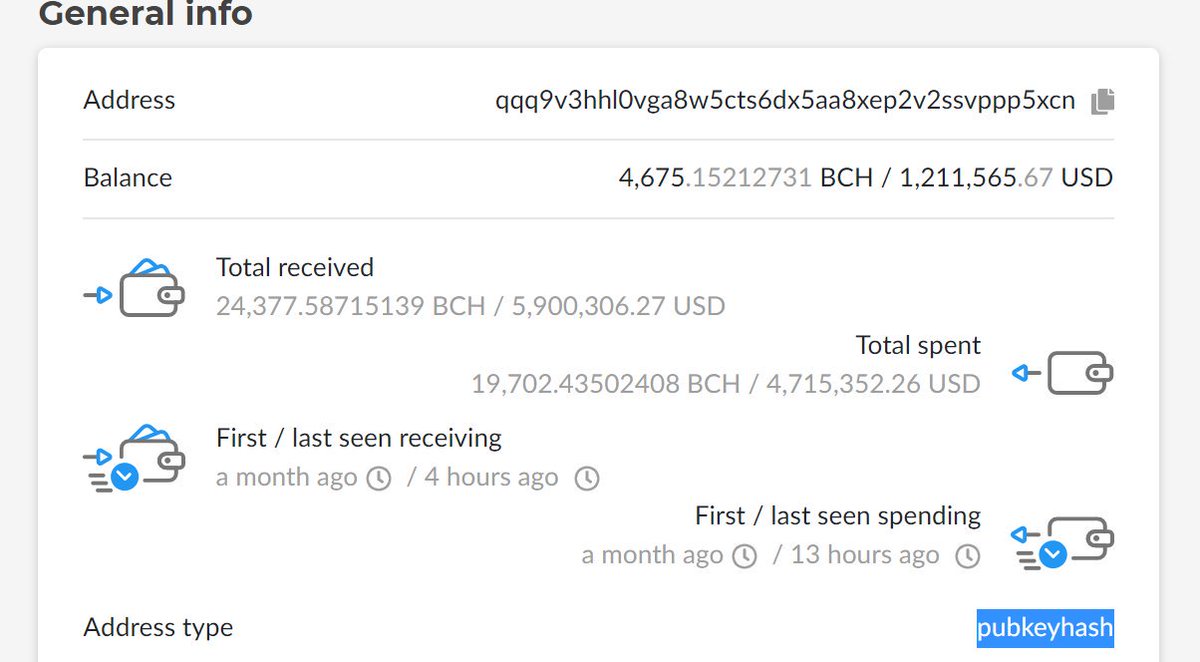
2/ The fact that Ethereum has an account-based transaction system (vs. UTXO) means that all Ethereum wallets must have an incrementally increasing 'nonce' value; the downside here is that this requires one to 'sync' with a node / API running *somewhere* on planet earth 



3/ More so to that API point that I made above, the disadvantage here for Ethereum users (in comparison to Bitcoin; don't worry I'll bring up an advanage).
Metamask users, for instance, have their wallets pointed at Infura(.)io's API endpoint.
Metamask users, for instance, have their wallets pointed at Infura(.)io's API endpoint.

4/ Afri (in tweets that are now deleted for some reason), stated that he took issue with the use of such services like Infura(.)io ; unfortunately, he was punished by the heads of Ethereum via community manufactured anti-sentiment against what he was saying. 

5/ In fact, when you think about it - most of the services on Ethereum that are so-called 'decentralized' (which is an interesting word to use for reasons I'll discuss later), are later re-centralized via the general lack of available tools / guides for one to bootstrap the same.
• • •
Missing some Tweet in this thread? You can try to
force a refresh