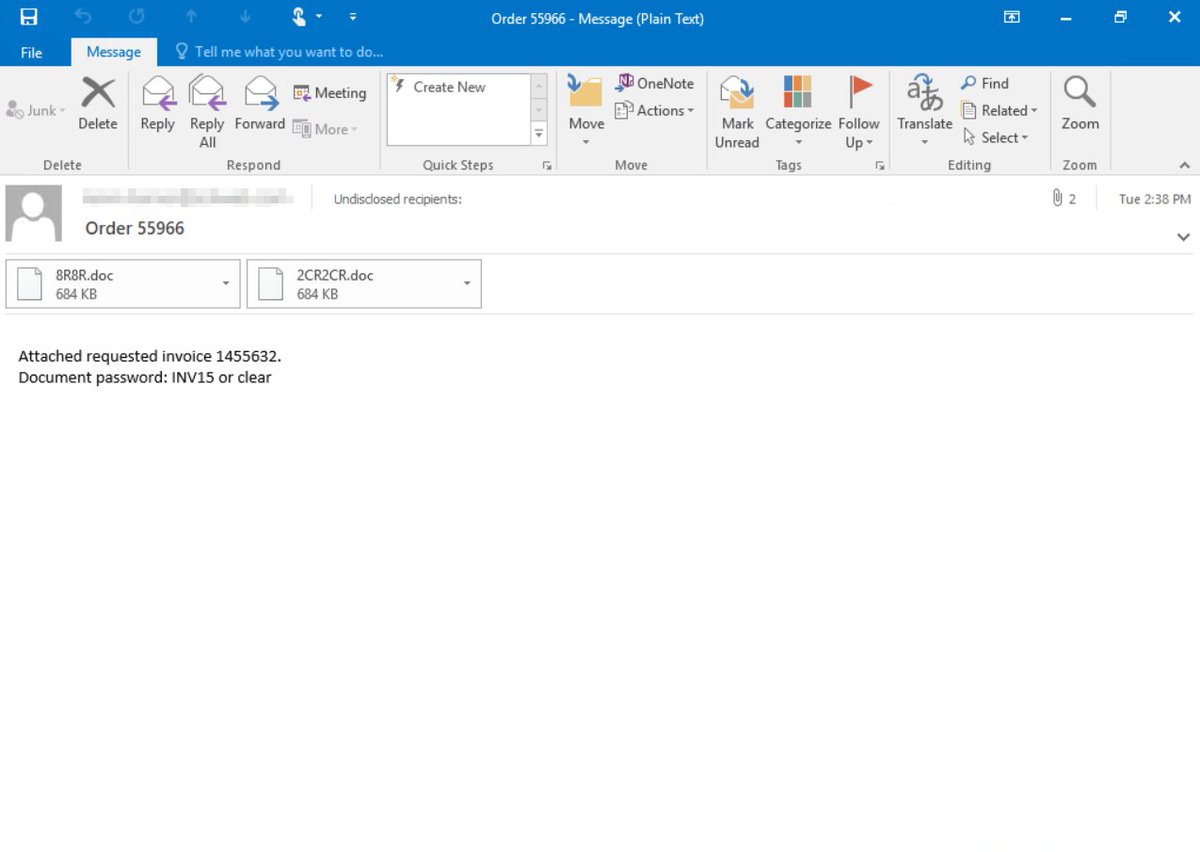
We’re tracking an active credential phishing attack targeting enterprises that uses multiple sophisticated methods for defense evasion and social engineering. The campaign uses timely lures relevant to remote work, like password updates, conferencing info, helpdesk tickets, etc. 



One of the interesting techniques we observed in this campaign is the use of redirector sites with a unique subdomain for each target. The subdomain follows different formats but generally always contains the recipient’s username and org domain name. 

This unique subdomain is added to a set of base domains, typically compromised sites. Notably, the phishing URLs have an extra dot after the TLD, followed by the Base64-encoded email address of the recipient.
The use of custom subdomains helps increase the believability of the lure. In addition, the campaign uses patterns in sender display names consistent with the social engineering lure: "Password Update", "Exchange proteccion", "Helpdesk-#", "SharePoint", "Projects_communications".
The unique subdomains also mean huge volumes of phishing URLs in this campaign, an attempt at evading detection. As another layer of defense evasion, these redirector URLs can detect connections from sandbox environments.
If the redirector detects that it’s being accessed from a sandbox environment or if the URL has expired, it redirects to legitimate sites, such that it can evade automated analysis, and only actual users reach the phishing site.
These techniques, in addition to the fact the email message uses heavy obfuscation in its HTML code, make for a sophisticated phishing campaign, exemplifying the increasingly complex email threats that enterprises face today.
Microsoft 365 Defender detects phishing and other email threats and correlates threat data across email and data, endpoints, identities, and apps. Microsoft Defender for Office 365 uses behavior-based detections and machine learning to detect sophisticated email threats.
Defenders can use advanced hunting and other tools in Microsoft 365 Defender to locate emails that exhibit the unique techniques used by this phishing campaign, perform additional investigation, and resolve attacks.
• • •
Missing some Tweet in this thread? You can try to
force a refresh