We've got a neat new @citizenlab report out, looking at NSO Group affiliate company Circles, the we-spy-without-hacking-your-phone guys, who reportedly exploit flaws in mobile phone networks themselves. We ID'd a bunch of likely customers! citizenlab.ca/2020/12/runnin…
The essence of the report is simple. The firewalls of Circles systems are configured using a management server with the domain name "tracksystem[.]info." Thanks to some leaked documents filed in a lawsuit in Israel, we can see that this domain name is used by Circles for email 



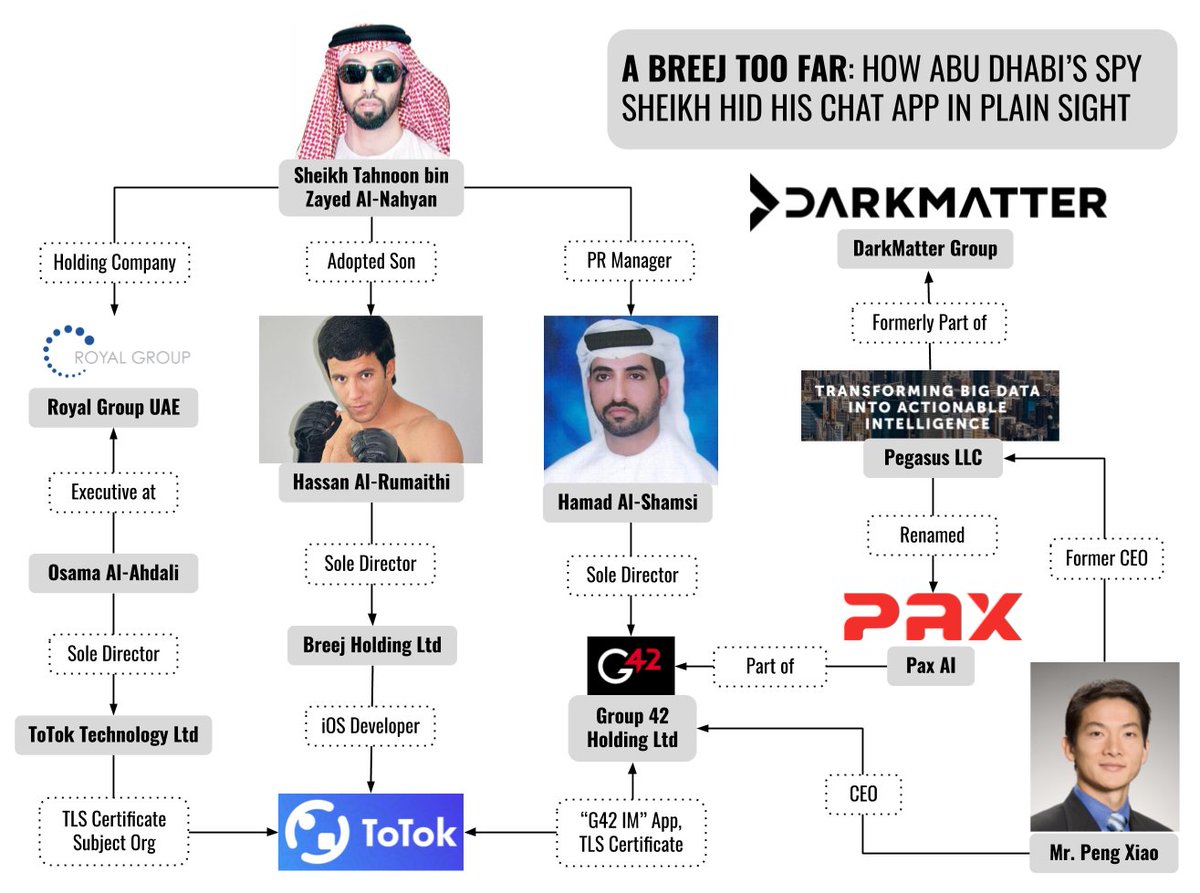
There's some dodgy customers, including spyware abuser UAE (apparently UAE Supreme Council for National Security, Sh. Tahnoon's Royal Group, and Dubai Police). The Royal group case is interesting, because there also seems to be a nexus with Mohammed Dahlan. 

Interesting case in Peru as well. In 2016, @fbajak reported on Israeli co Verint's role in "Project Pisco" (apnews.com/article/f799cf…) a National Intelligence Directorate (DINI) initiative to monitor comms. Our scans found a Circles system called "Porsche Pisco" operated by DINI. 

Also nice overlap in Nigeria w/ @PremiumTimesng report that two governors used Circles to spy on political opponents (premiumtimesng.com/investigations…). We found Circles systems in Nigeria. One system appears to be operated by the same group as a FinFisher system we found in 2015. 

Also nice overlap w/ investigation by @NuestroDiario (nomada.gt/pais/la-corrup…) looking at Guatemala's General Directorate of Civil Intelligence (DIGICI). DIGICI reportedly abused Circles to spy on journalists. Our scans found a Circles system in Guatemala operated by DIGICI! 

• • •
Missing some Tweet in this thread? You can try to
force a refresh