Sohn bekommt @kinderus Überraschungs Ei ... ihr wisst schon, das Ding wo früher mal coole Sachen drin waren ... Getriebe, Metallzahnräder richtige Schwungräder
"Spannung, Spaß, Spiel"
"Spannung, Spaß, Spiel"
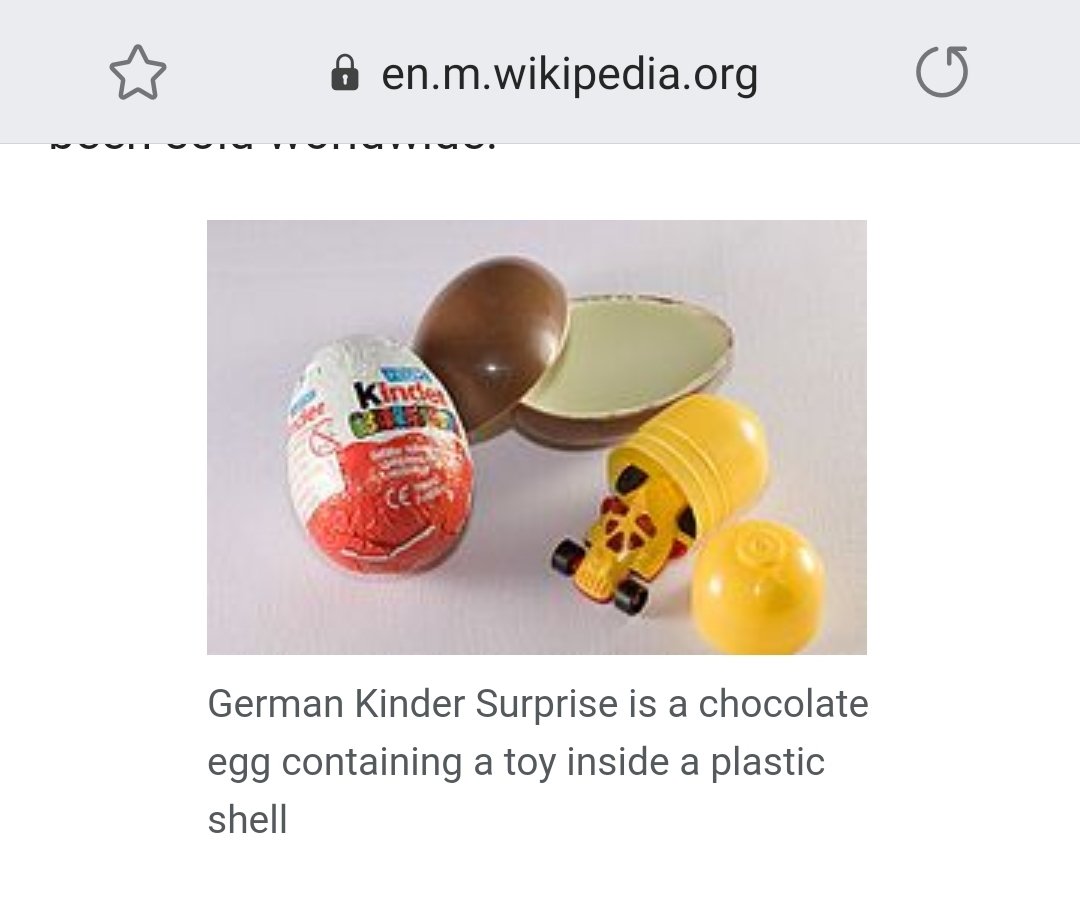
Wir kaufen die nur noch selten, weil Heute nur noch Plastikmüll drin ist.
Mein Sohn rennt also wie angestochen durch die Bude und sucht verzweifelt den Beipackzettel zu dem Plastikmüll.
Ich wundere mich, ist ja alles schon zusammengebaut.
Er findet ihn ...
Mein Sohn rennt also wie angestochen durch die Bude und sucht verzweifelt den Beipackzettel zu dem Plastikmüll.
Ich wundere mich, ist ja alles schon zusammengebaut.
Er findet ihn ...

Ich verstehe, ist ein QR Code drauf, das sagt ihm was.
Er: Papa kann ich den mit deinem Handy scannen und die App spielen (App hat er also auch gleich abgeleitet)
Ich: Vergiss es, kostenlose Apps sind alle 😈... ich beschäftige mich gerade damit.
Sohn sauer, ich gehe Rauchen
Er: Papa kann ich den mit deinem Handy scannen und die App spielen (App hat er also auch gleich abgeleitet)
Ich: Vergiss es, kostenlose Apps sind alle 😈... ich beschäftige mich gerade damit.
Sohn sauer, ich gehe Rauchen
Überlege und öffne bei Zigarette mal die Datenschutzbestimmungen.
App explizit für Kinder ... Verantwortung wird an Eltern übertragen (COPPA konform)

App explizit für Kinder ... Verantwortung wird an Eltern übertragen (COPPA konform)

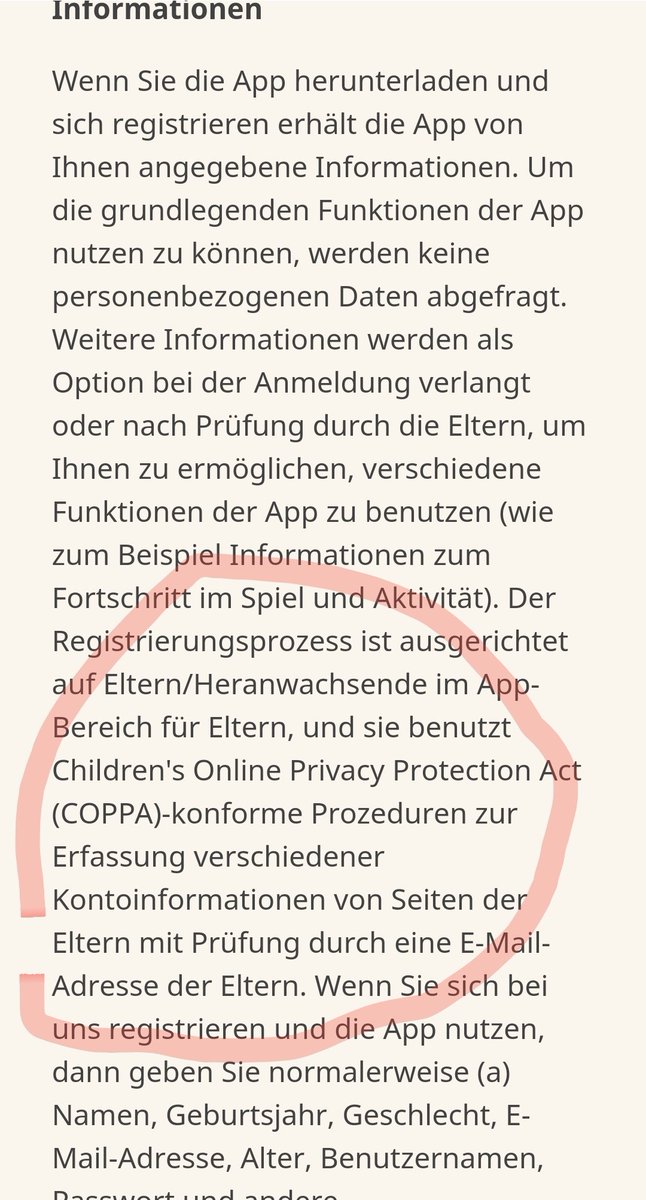
Die eingebaute Gesichtserkennung speichert keinerlei Daten und ??? die so erhaltenen Daten werden auch nicht an Dritte weitergegeben ???
Passt schon!
Passt schon!

Komme zurück von meiner Zigarette und gehe zu meinem Sohn (schlechtes Gewissen).
Ich: Hey Kumpel, hab das mal ge-checkt ... klar kannst du die App mal probieren, aber wir nehmen eins von meinen anderen Handys zum testen.
Gleich nach der Installation bin ich gefordert
Ich: Hey Kumpel, hab das mal ge-checkt ... klar kannst du die App mal probieren, aber wir nehmen eins von meinen anderen Handys zum testen.
Gleich nach der Installation bin ich gefordert

Gleich nach dem "user consent" ... oder "parent consent" gehen dann die ersten Daten an Google raus (da kann Ferrero Kinder nicht viel machen, schätze ich) 



Kamera Zugriff ... lieber nicht, das mit den Daten zur Gesichtserkennung habe ich in den "privacy terms" nicht so richtig gerafft 

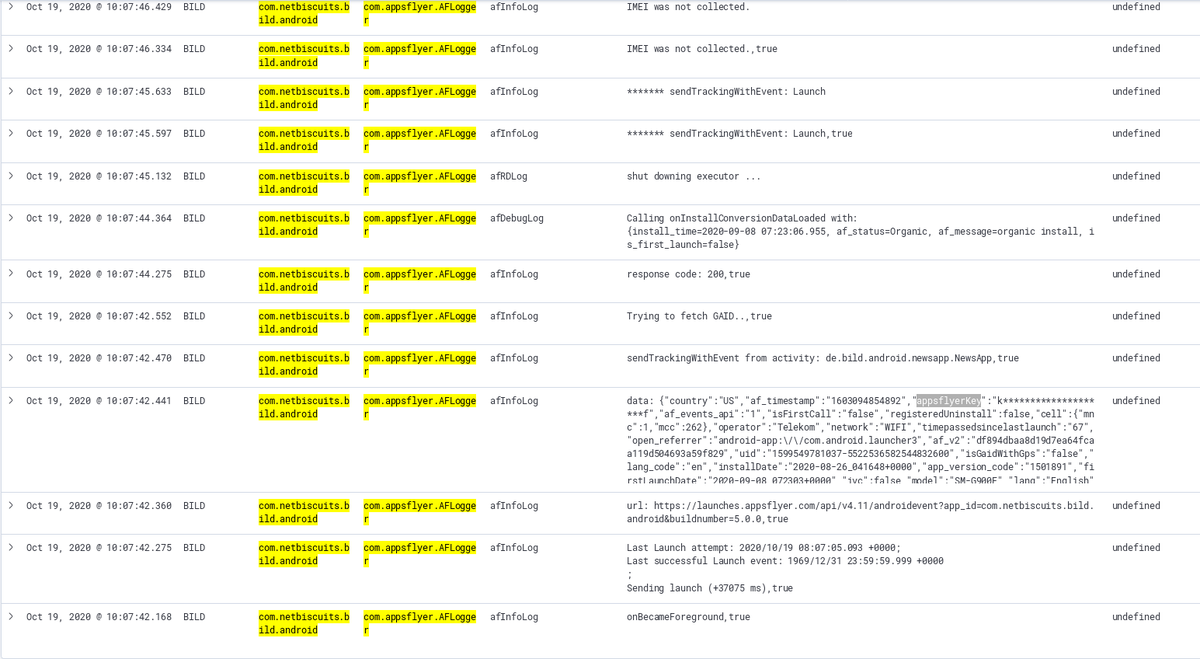
Sohn spielt, Papa schaut mal an welche Tracker Daten gesendet werden
Erstaunlich: Crashlytics bekommt nur Gerätehersteller, Gerätemodell und die Buildnummer des ROMs.
Unity3D geht ganz leer aus (bis auf den ping-back zur Nutzeraktivität)
Erstaunlich: Crashlytics bekommt nur Gerätehersteller, Gerätemodell und die Buildnummer des ROMs.
Unity3D geht ganz leer aus (bis auf den ping-back zur Nutzeraktivität)

Hmm ... vielleicht sollte ich nicht nach bekannten Trackern filtern!
Was ist den 'sdk.easyar.com' ... da gehen ja fast alle Gerätedaten hin, die mit den beschränkten Berechtigungen der App abrufbar sind (einschließlich persistenter Android ID)

Was ist den 'sdk.easyar.com' ... da gehen ja fast alle Gerätedaten hin, die mit den beschränkten Berechtigungen der App abrufbar sind (einschließlich persistenter Android ID)


Ach so! Das ist nur der nette "Cloud basierte Bilderkennungs-Service" aus Shanghai ... quasi direkt von neben an.
Danke Ferrero, ich de-installiere die App mal wieder, bevor mein Sohn versehentlich doch noch Kamera-Zugriff erlaubt

Danke Ferrero, ich de-installiere die App mal wieder, bevor mein Sohn versehentlich doch noch Kamera-Zugriff erlaubt


• • •
Missing some Tweet in this thread? You can try to
force a refresh