#AppPrivacy #Android
If you are interested in what data Android Apps push out to AppsFlyer, it might be a good idea to utilize @fridadotre to hook the 'af*' methods of class 'com.appsflyer.AFLogger'.
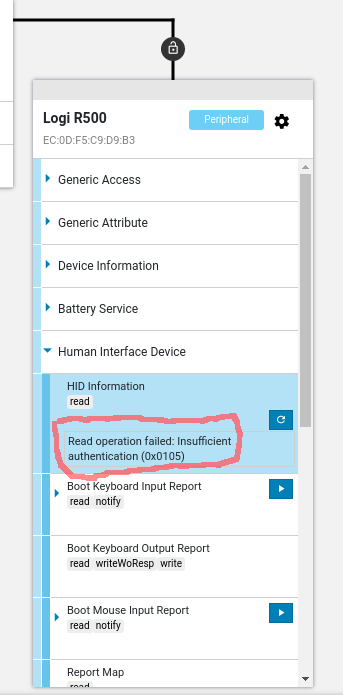
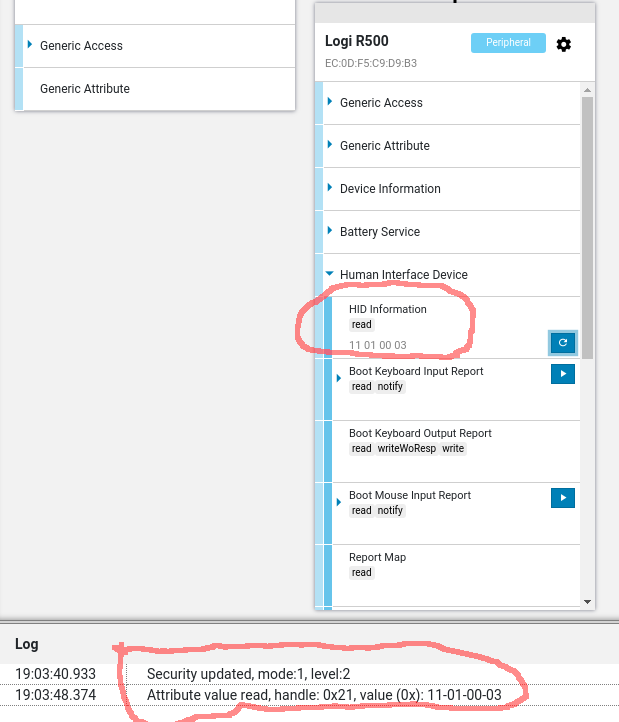
The screenshot shows an example of the app 'Bild'
1/n
If you are interested in what data Android Apps push out to AppsFlyer, it might be a good idea to utilize @fridadotre to hook the 'af*' methods of class 'com.appsflyer.AFLogger'.
The screenshot shows an example of the app 'Bild'
1/n
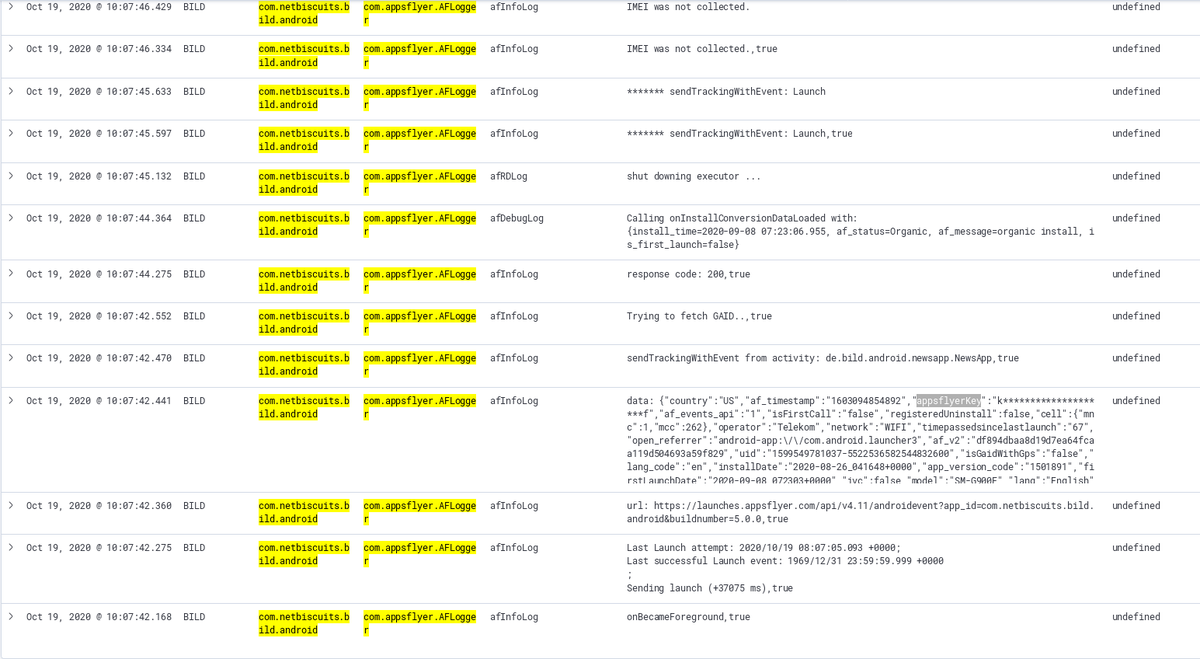
The screenshot contains to events, related to outbound http requests.
1) The one starting with "url:", which contains a request URI
2) The next event starting with "data:", which contains the **unecrypted** content, which is sent out ("appsflyerkey" redacted)
2/n
1) The one starting with "url:", which contains a request URI
2) The next event starting with "data:", which contains the **unecrypted** content, which is sent out ("appsflyerkey" redacted)
2/n
If you inspect the corresponding HTTPS request, the actual data is encrypted (at least it should be).
So if you have to proof the the data from "AFLogger" is contained in the request, you have to decrypt the body content
3/n
So if you have to proof the the data from "AFLogger" is contained in the request, you have to decrypt the body content
3/n

I recently tweeted on an approach doing this by hooking 'com.appsflyer.AFEvent' and other dynamically loaded classes. but the approach does not always apply (AFEvent class does not always exist).
I don't want to get into great detail on reversing the encryption ...
4/n
I don't want to get into great detail on reversing the encryption ...
4/n
... but what I believe is safe to reveal is safe to reveal that
1) The redacted "appsflayerKey" from the 1st screenshot could be obtained from several hook points
2) This keys is a password and the actual key is obtained using PBKDF2
...
5/n
1) The redacted "appsflayerKey" from the 1st screenshot could be obtained from several hook points
2) This keys is a password and the actual key is obtained using PBKDF2
...
5/n
3) Once the key is derived (exists per app) it is used to encrypt the data with AES128-CBC.
I don't want to give more details on key derivation/encryption, to avoid legal issues. But I consider it to be a valid demand, to inspect what gets pushed out from your device.
6/n
I don't want to give more details on key derivation/encryption, to avoid legal issues. But I consider it to be a valid demand, to inspect what gets pushed out from your device.
6/n
7/7
So if you are interested in this, the information from above should give you a good starting point to get the necessary details on encryption/key derivation parameters.
Also pay attention to the following tweet (crypto classes exist in-memory only):
So if you are interested in this, the information from above should give you a good starting point to get the necessary details on encryption/key derivation parameters.
Also pay attention to the following tweet (crypto classes exist in-memory only):
https://twitter.com/mame82/status/1317129640025202689
• • •
Missing some Tweet in this thread? You can try to
force a refresh