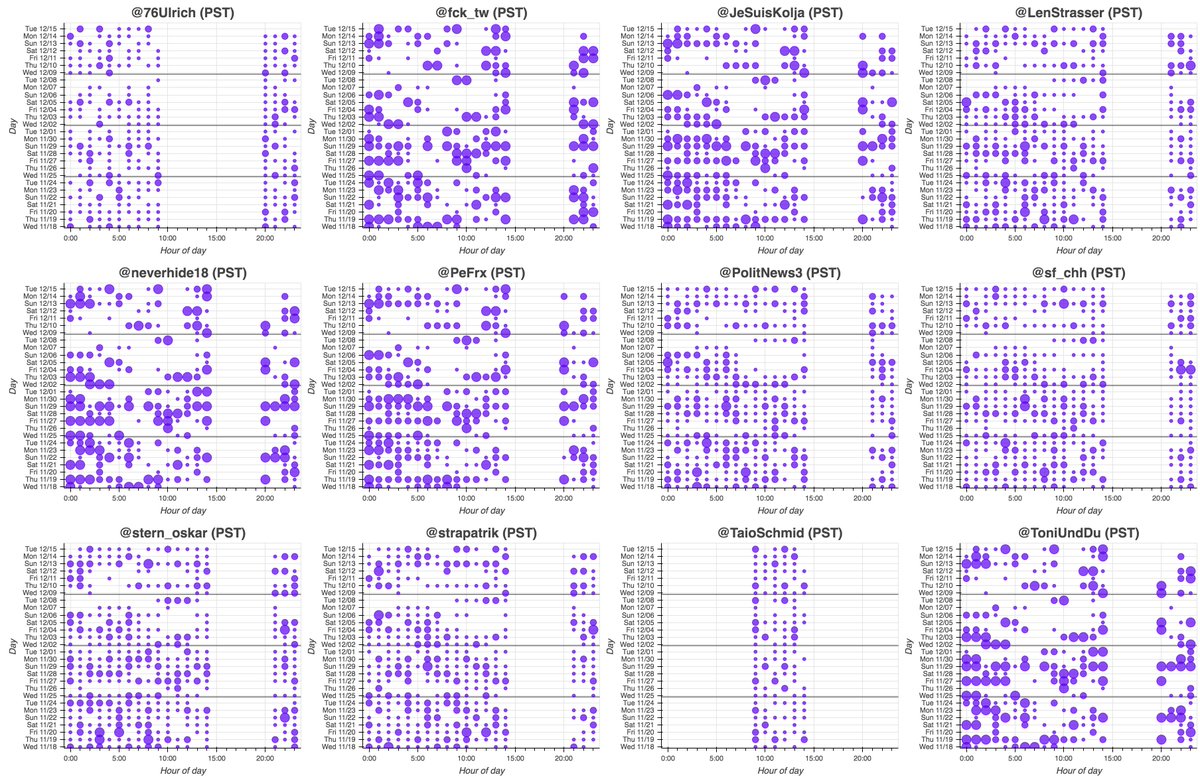
In a bizarre coincidence, this hashtag-crammed @SorabNY tweet was retweeted by a bunch of accounts created in May 2014 with random-looking names. #FridayFeeling
cc: @ZellaQuixote
cc: @ZellaQuixote

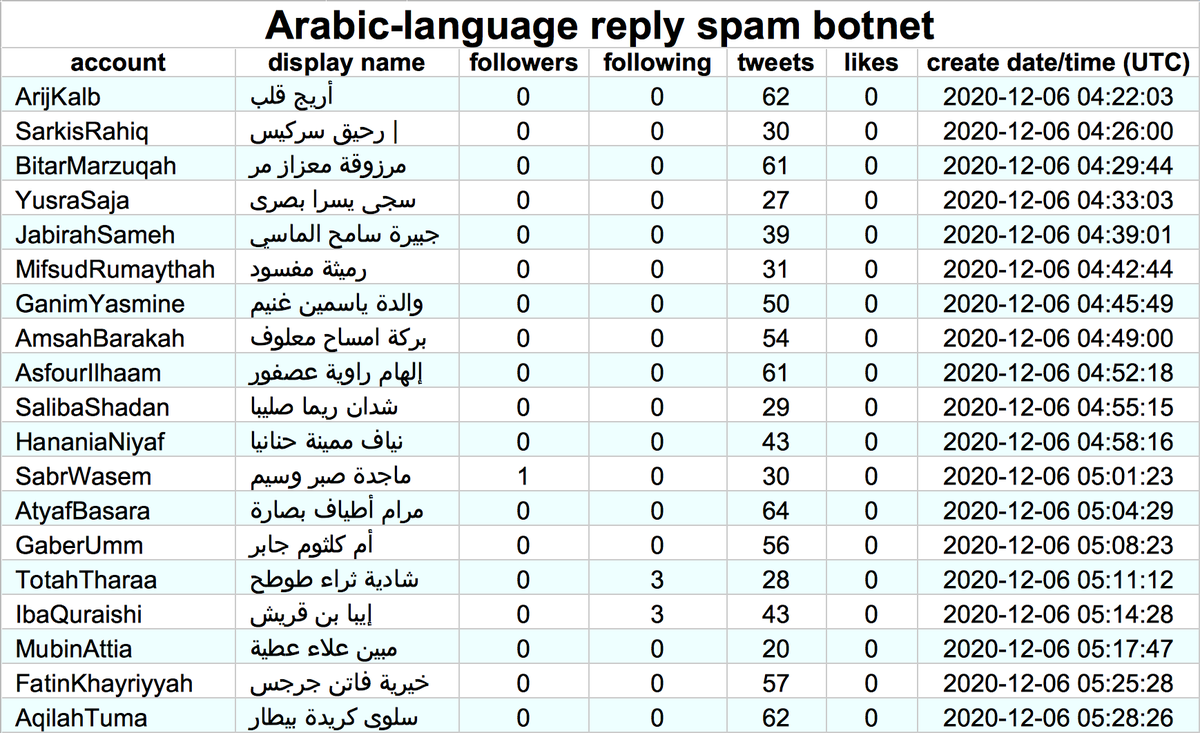
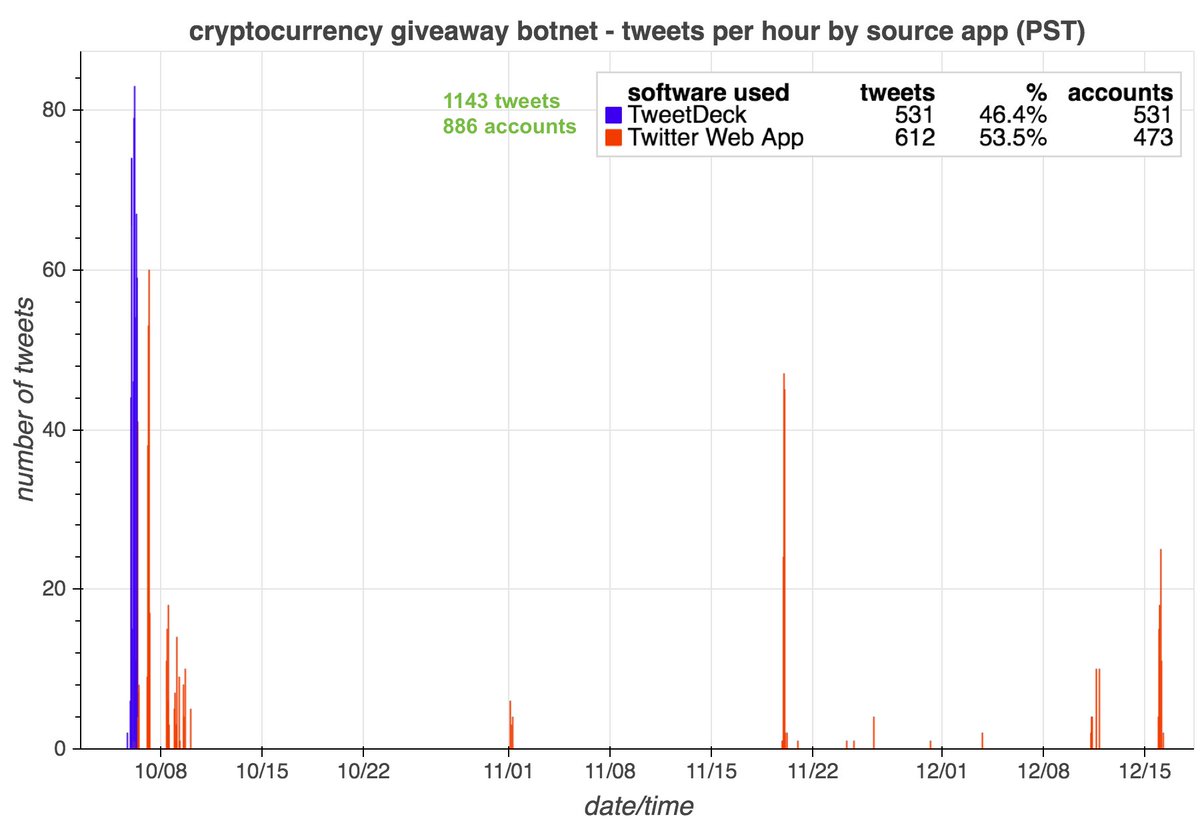
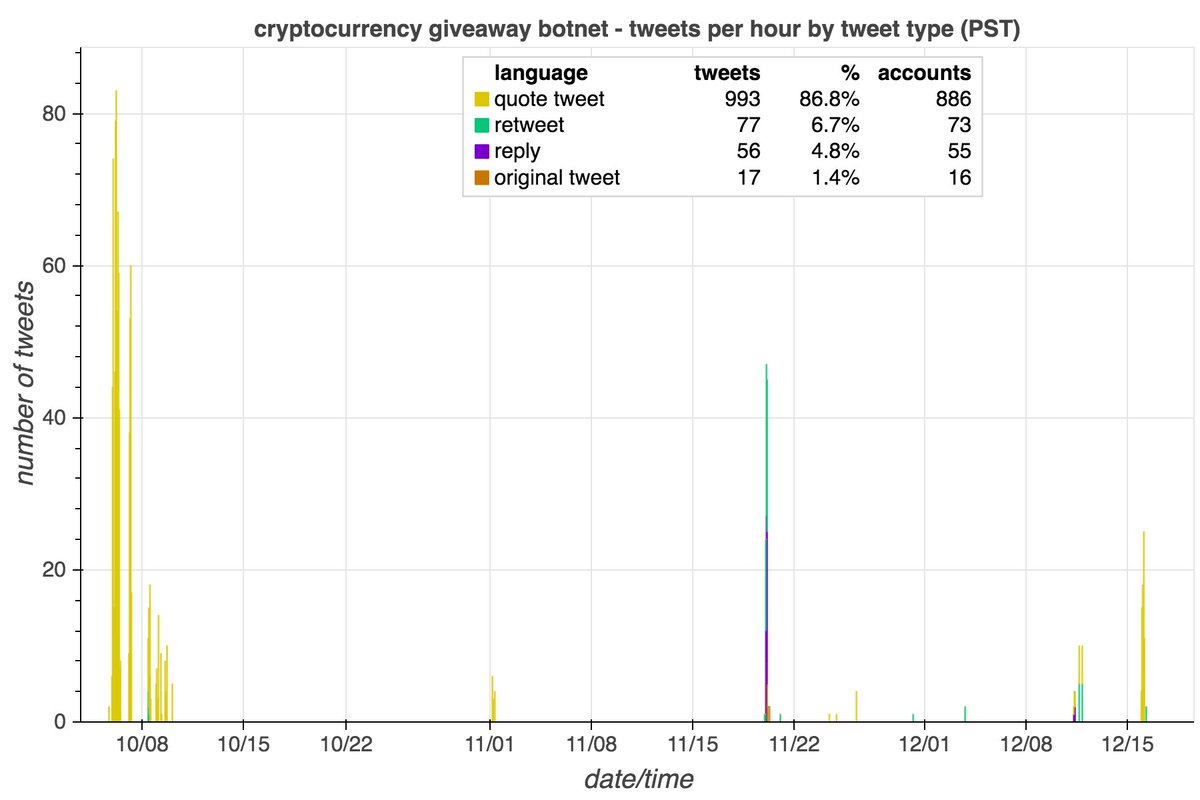
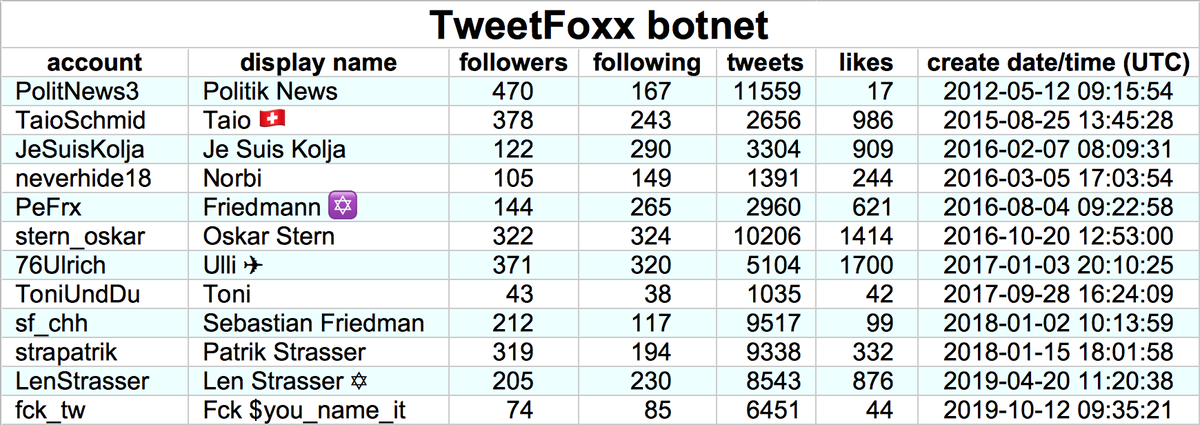
These accounts are part of a 29-account retweet botnet created on May 25th, 2014. All the accounts have names consisting of 11 or 12 lowercase letters, beginning with a consonant and followed by alternating vowels and consonants. We suspect the names were generated randomly. 

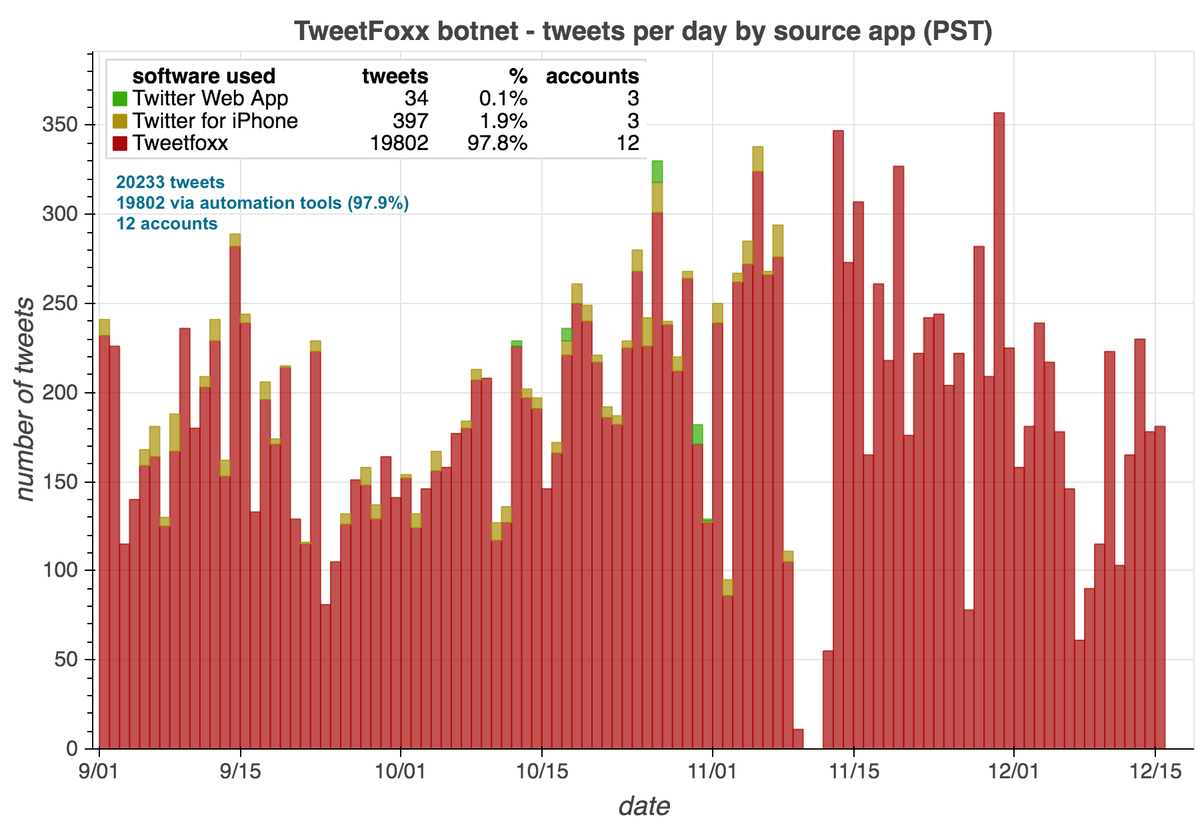
The accounts in this botnet have thus far posted all of their tweets (allegedly) via "Twitter Web App". Despite being created back in 2014, we found no evidence any of them tweeted prior to September 2020, with most accounts activating for the first time on December 9th, 2020. 


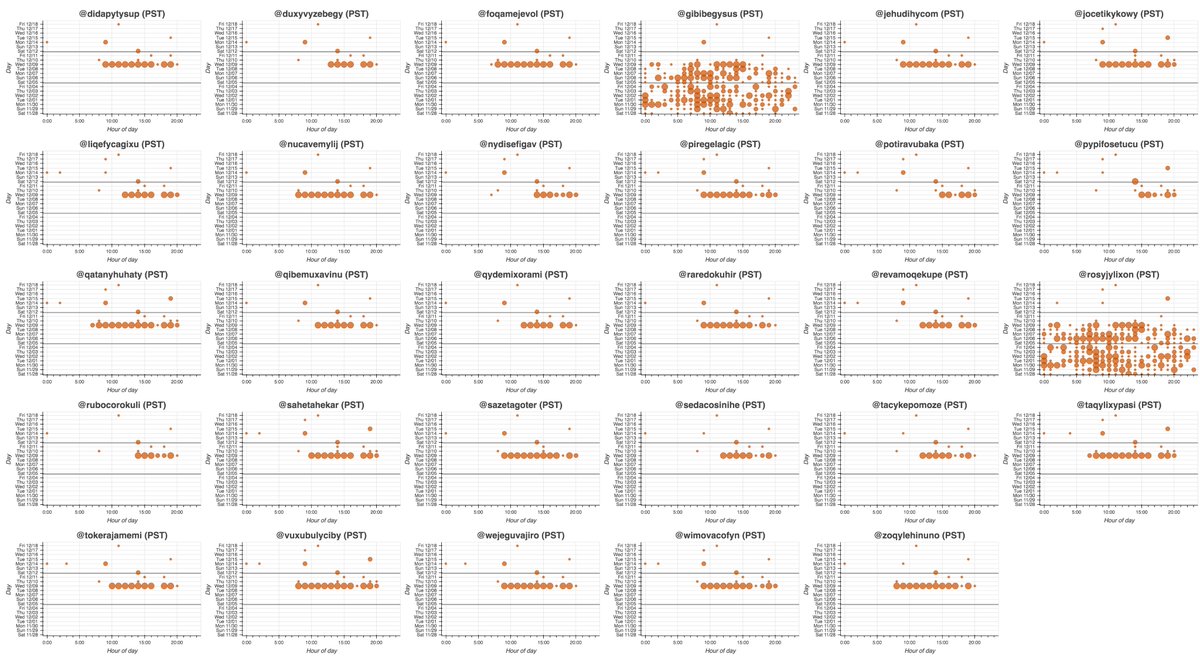
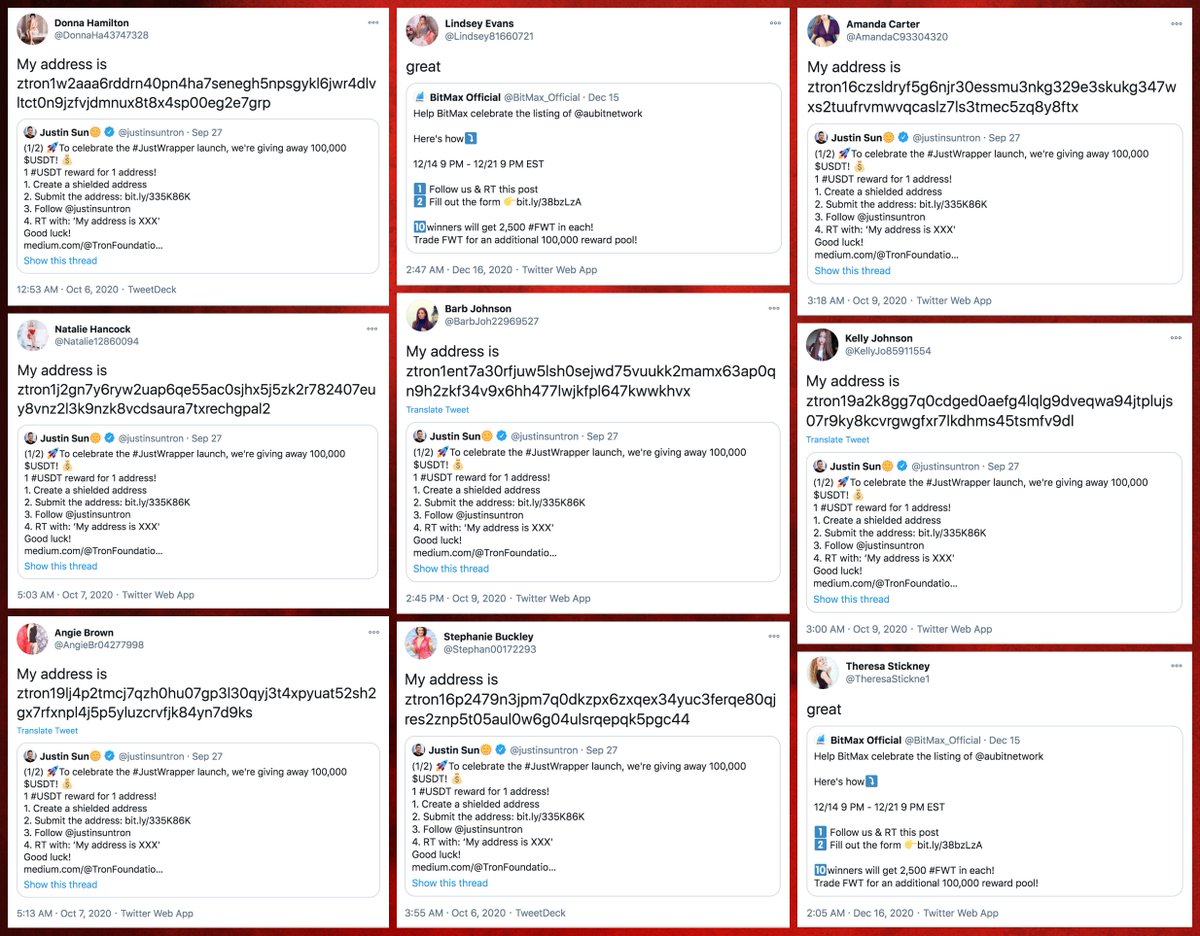
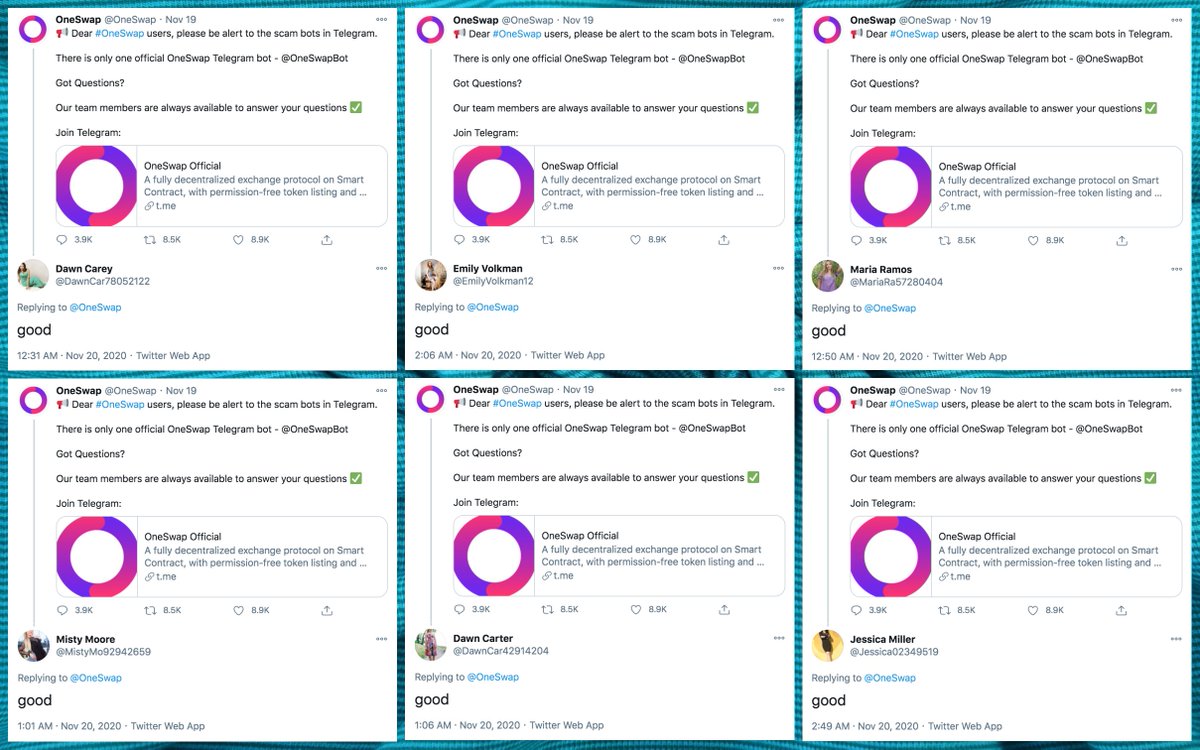
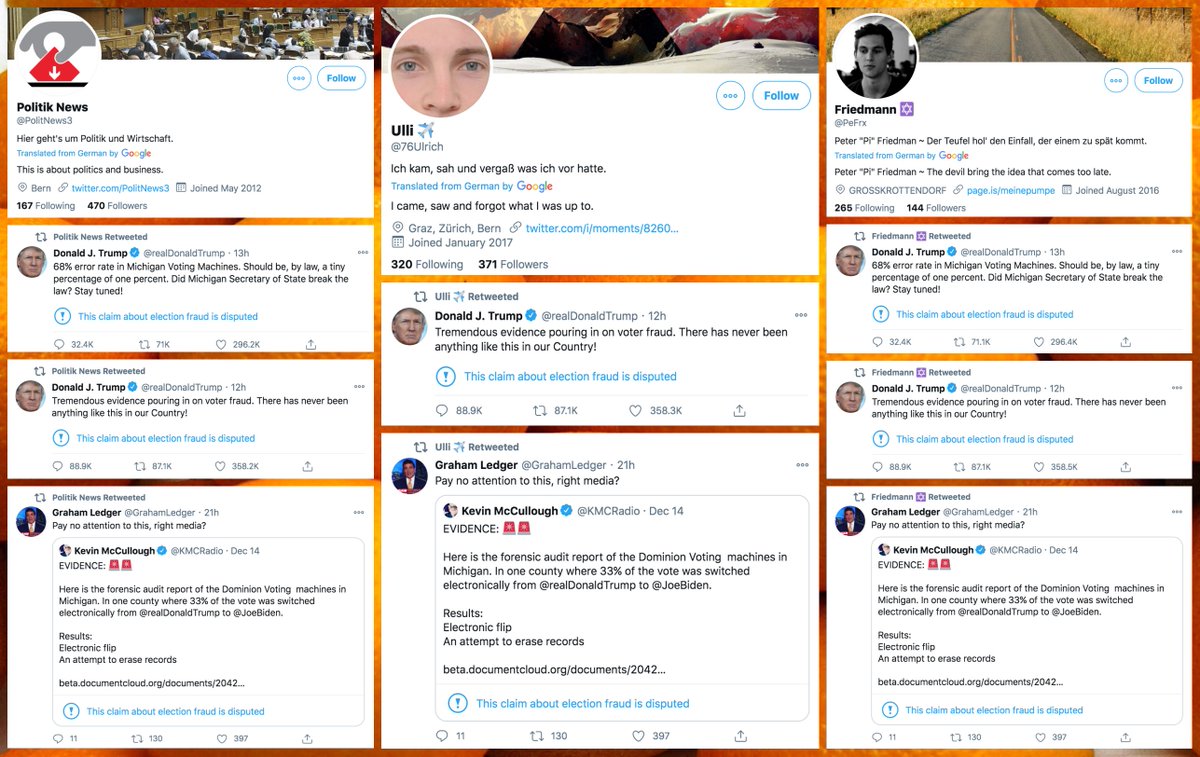
Who do these accounts retweet? They mostly amplify accounts promoting various products and services, although political tweets from @realDonaldTrump turn up in the mix as well. (The tweets in the collage are examples of tweets retweeted by every bot in the network.) 



Although we weren't able to find most of these accounts' profile pics via reverse image search, we did notice something interesting: portions of their profile pics are frequently used as header images on other accounts in the botnet. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh