Per briefing today on SolarWinds hack, @RonWyden says IRS was not compromised or taxpayer data affected. However, hack of Treasury Department "appears to be significant." Treasury breach began in July, "the full depth of which isn’t known."
Microsoft notified Treasury Dept that dozens of email accounts were compromised. Additionally the hackers broke into systems in the Departmental Offices division of Treasury, home to Treasury's highest-ranking officials. Treasury still doesn't know precisely what info was stolen.
.@RonWyden on SW: “[A]fter yrs of gov officials advocating for encryption backdoors and ignoring warnings from [infosec] experts who said...encryption keys [are targets] for hackers, the USG has..suffered a breach that seems to involve...stealing encryption keys from USG servers”
What does Wyden mean when he says they stole encryption keys from US gov servers? "Once the hackers gained access to [Treasury Dept's] Departmental Offices network, they stole an encryption key used by Treasury's 'single sign on' login infrastructure," a Wyden aide tells me.
"With this key, the hackers were able to forge the credentials necessary to gain legitimate access to several Microsoft cloud-hosted email accounts," Wyden's aide says, attributing the info to Treasury officials who provided a briefing on the SolarWinds hack.
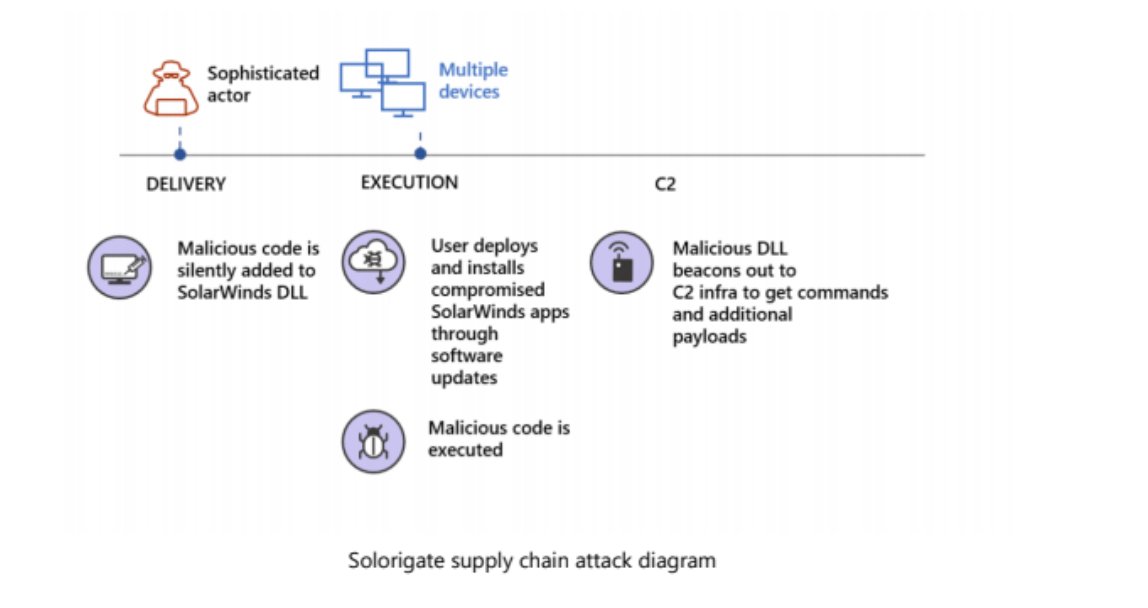
This matches what Microsoft had revealed in its writeup where it discussed how the SolarWinds hackers stole SAML encryption certificates for the targets who were hacked (blogs.microsoft.com/on-the-issues/…)
Here's Microsoft describing it: The intruders using admin permissions gained access to an org’s trusted SAML token-signing cert. "This enables them to forge SAML tokens that impersonate any of the organization’s existing users and accounts, including highly privileged accounts."
The forged tokens "can be used against any on-premises resources (regardless of identity system or vendor) as well as against any cloud environment (regardless of vendor) because they have been configured to trust the certificate." In other words, the keys to the kingdom.
NYT is now reporting that per Treasury Dept, Treasury Secretary Steven Mnuchin’s email account was not among those that were breached.
Treasury Secretary Steven Mnuchin, addressing the breach of the Treasury Dept with CNBC, said today: “At this point, we do not see any break-in into our classified systems. Our unclassified systems did have some access.”
Mnuchin speaking about Treasury hack: “I can assure you, we are completely on top of this
NYT [in narrator voice:] "He did not explain how the Russian presence was not detected in the system for more than four months."
NYT [in narrator voice:] "He did not explain how the Russian presence was not detected in the system for more than four months."
• • •
Missing some Tweet in this thread? You can try to
force a refresh