#Zyxel announced CVE-2020-29583 fixing a backdoor admin account which gave attackers root on affected devices via SSH or web interface
If you want to examine the firmware you need to run a #known_plaintext_attack against an encrypted zip
Sounds hard; don't worry I got you... 👇
If you want to examine the firmware you need to run a #known_plaintext_attack against an encrypted zip
Sounds hard; don't worry I got you... 👇
Zyxel have actually removed the backdoored firmware versions from their portal; but you can still grab the latest version or earlier versions for further inspection.
Example:
portal.myzyxel.com/my/firmwares?f…
Example:
portal.myzyxel.com/my/firmwares?f…

Running file on the .bin file suggests this is a zip archive, but if you attempt to unzip it from the command line, you'll see errors, as it's password protected 

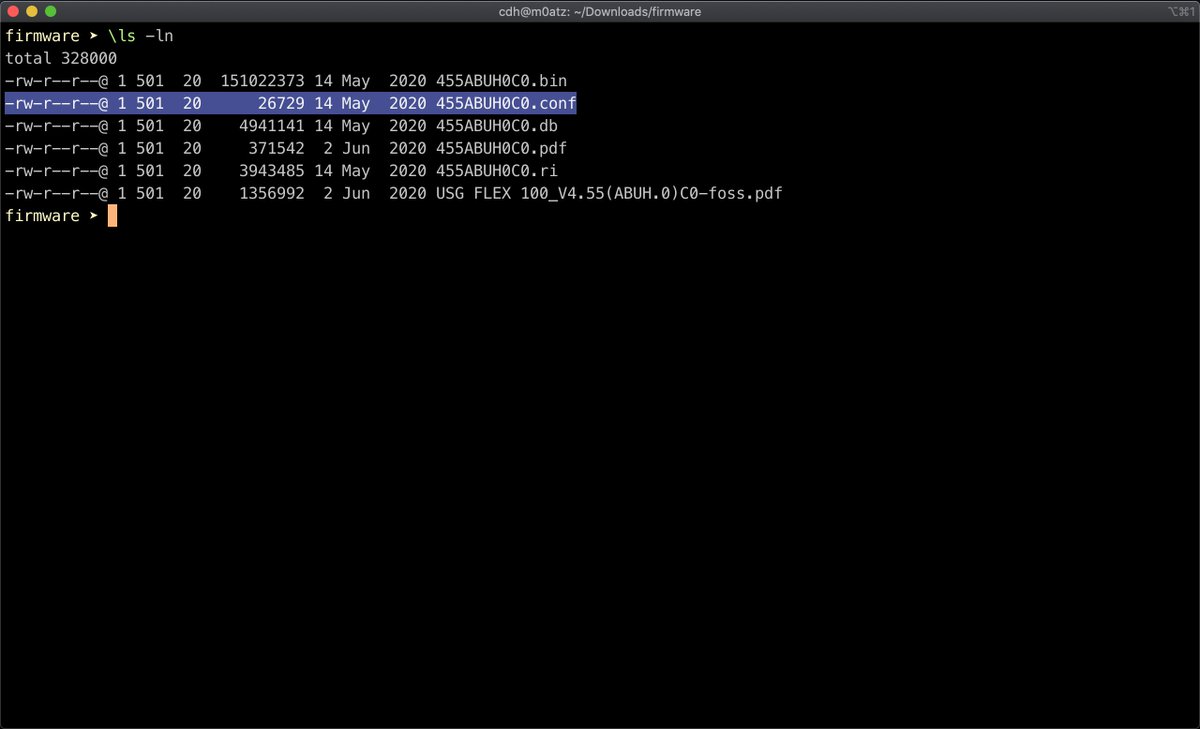
Let's flip to Windows and browse the archive using 7-Zip. We don't know the password to extract the zip, but we can see the file names, folder structure and file size 

Browse through the folders and you'll find system-default.conf in the following location
455ABUH0C0.bin\db\etc\zyxel\ftp\conf\system-default.conf
455ABUH0C0.bin\db\etc\zyxel\ftp\conf\system-default.conf

Hey, wait, that file is 26729 bytes long. Didn't we see something like that in the original firmware zip?
Coincidence? I think not. Looks like we know some of the plaintext within the encrypted zip.
Coincidence? I think not. Looks like we know some of the plaintext within the encrypted zip.
Now it's time to break out pkcrack. I use a mac, and you can install using homebrew, i.e.
brew install pkcrack
formulae.brew.sh/formula/pkcrack
brew install pkcrack
formulae.brew.sh/formula/pkcrack
I wrote a quick bash script which will help automate the process of cracking the zip.
We need to zip up the plaintext and also extract it and feed both to pkcrack along with the .bin we want to crack.
github.com/cybercdh/hacks…
We need to zip up the plaintext and also extract it and feed both to pkcrack along with the .bin we want to crack.
github.com/cybercdh/hacks…
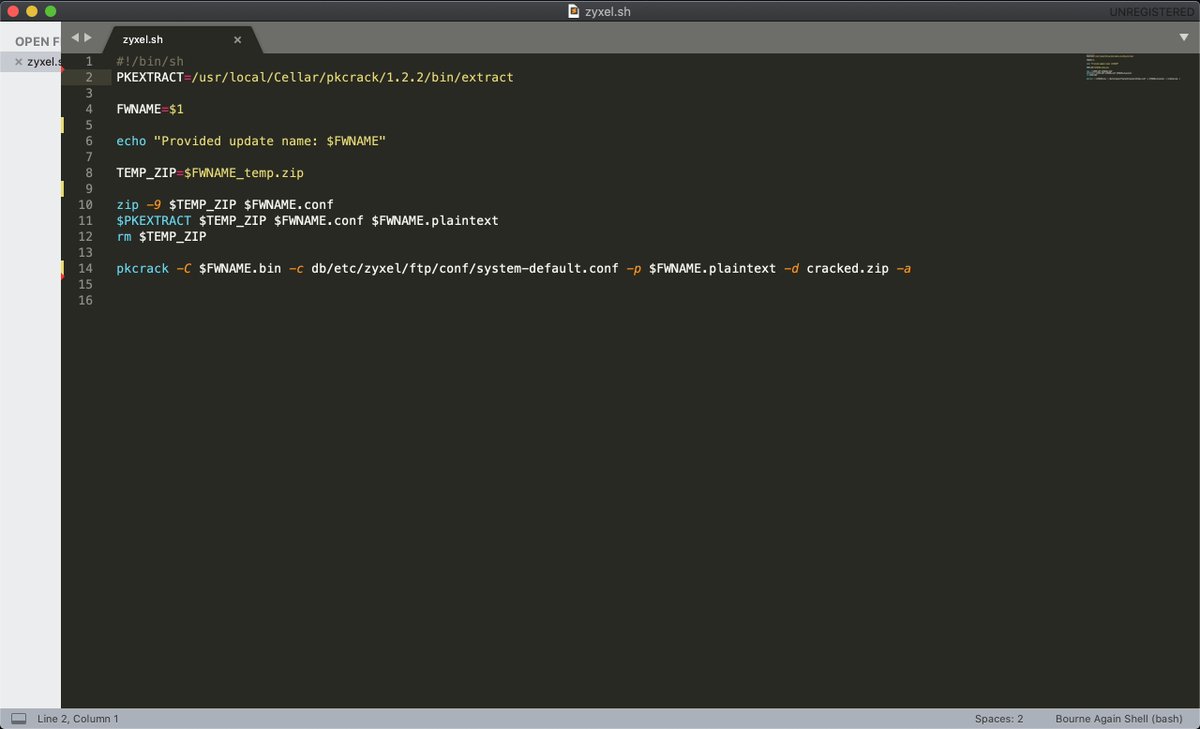
Run the bash script in the same directory as the firmware .bin file, feed it the name of the firmware (not the full filename of the bin) and it will crack the zip in about 20 seconds.
You'll then have a cracked .zip file in your current directory
You'll then have a cracked .zip file in your current directory

You'll want to pay attention to the file compress .img, this likely uses squashfs and therefore you can install squashfs using homebrew, and then run unsquashfs on the .img
formulae.brew.sh/formula/squash…
formulae.brew.sh/formula/squash…

Now, browse the filesystem looking for goodness / badness.
Here we can see the backdoor user still actually exists in the latest firmware.
I'm sure you'll find some other interesting nuggets. Enjoy
Here we can see the backdoor user still actually exists in the latest firmware.
I'm sure you'll find some other interesting nuggets. Enjoy

• • •
Missing some Tweet in this thread? You can try to
force a refresh