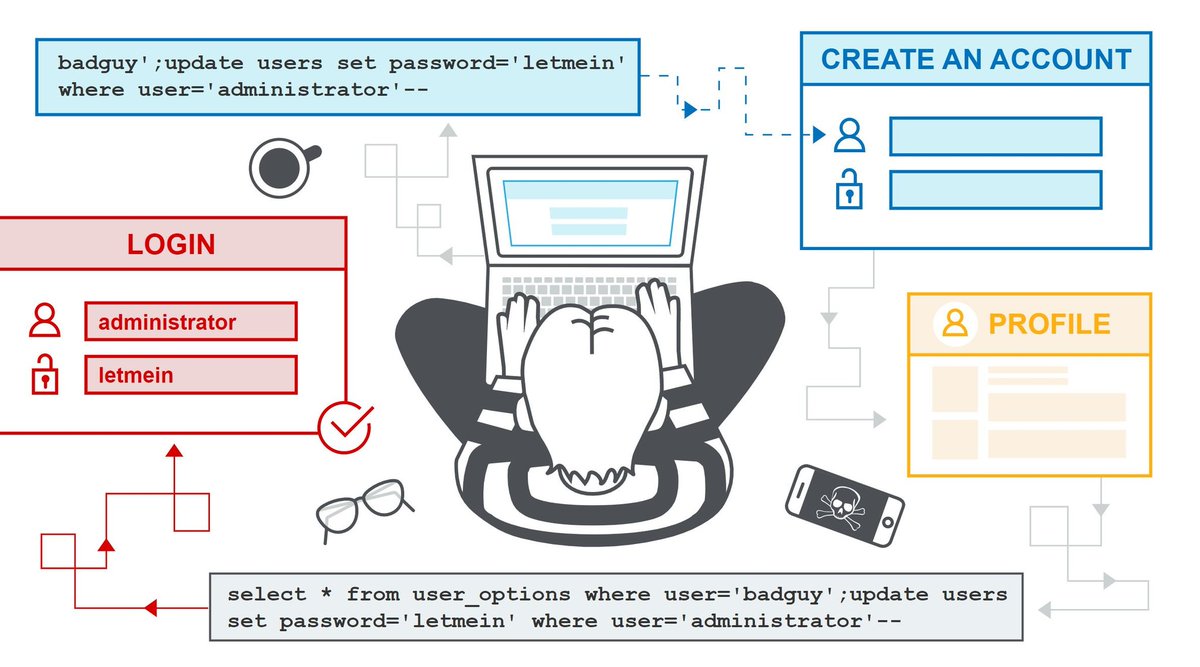
Great article by @StafordTitus for demonstrating cloud attack scenarios.
Learned about:
1- CloudGoat by @RhinoSecurity - Vulnerable AWS Lab for practicing cloud pentesting scenarios.
2- Privilege Escalation thru IAM policy misconfiguration
3- S3 Bucket Enumeration
#infosec
Learned about:
1- CloudGoat by @RhinoSecurity - Vulnerable AWS Lab for practicing cloud pentesting scenarios.
2- Privilege Escalation thru IAM policy misconfiguration
3- S3 Bucket Enumeration
#infosec
https://twitter.com/PenTestMag/status/1339599865832083457
I have been putting off learning about the cloud for a while now. The main reason is that there are plenty of products and tools to learn that make it daunting and complex for newcomers—this year's goals to look into it in-depth and understand the fundamentals.
#aws
#aws
Planning to start the journey with Cloud Security Bootcamp by @SecurityTube @vivekramac and play with the CloudGoat Labs afterwards.
#pentesting
#pentesting
@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh