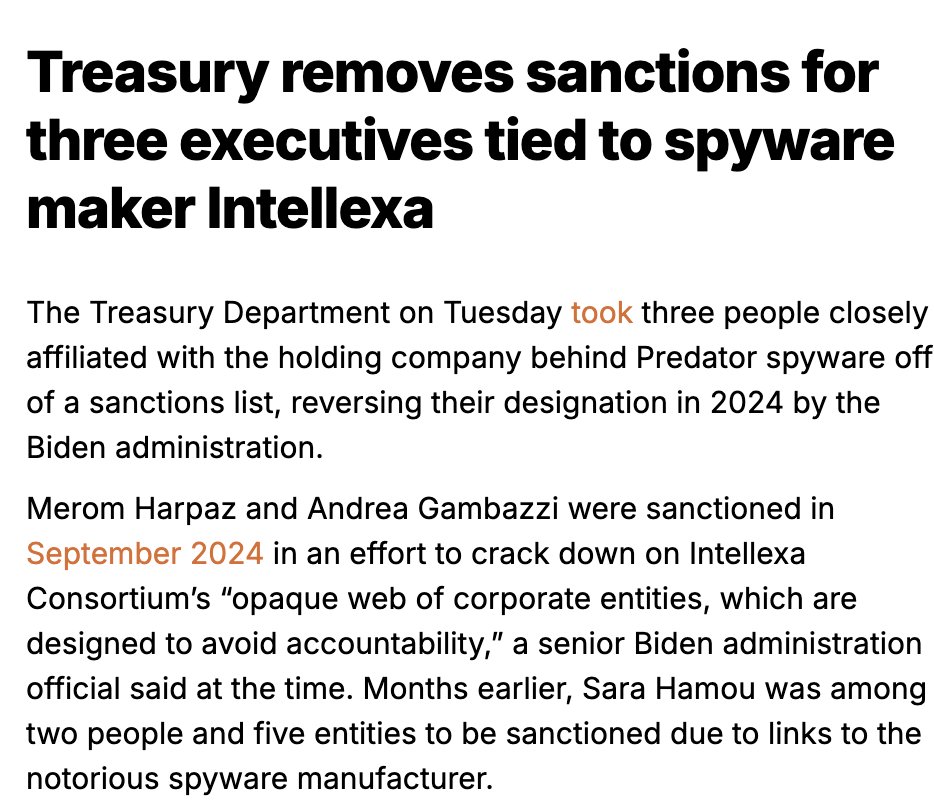
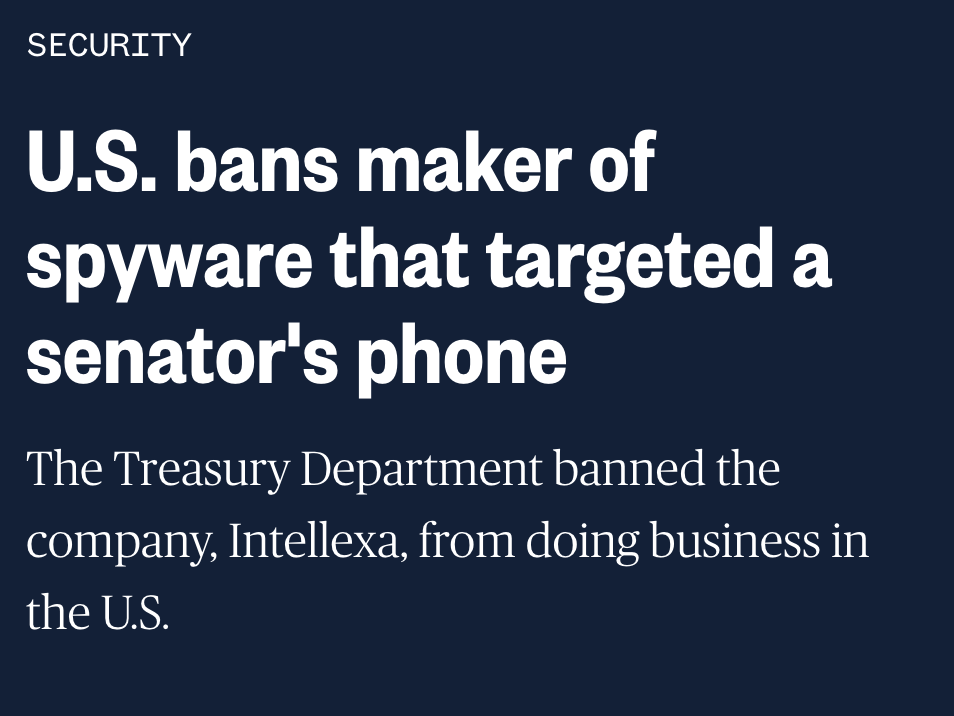
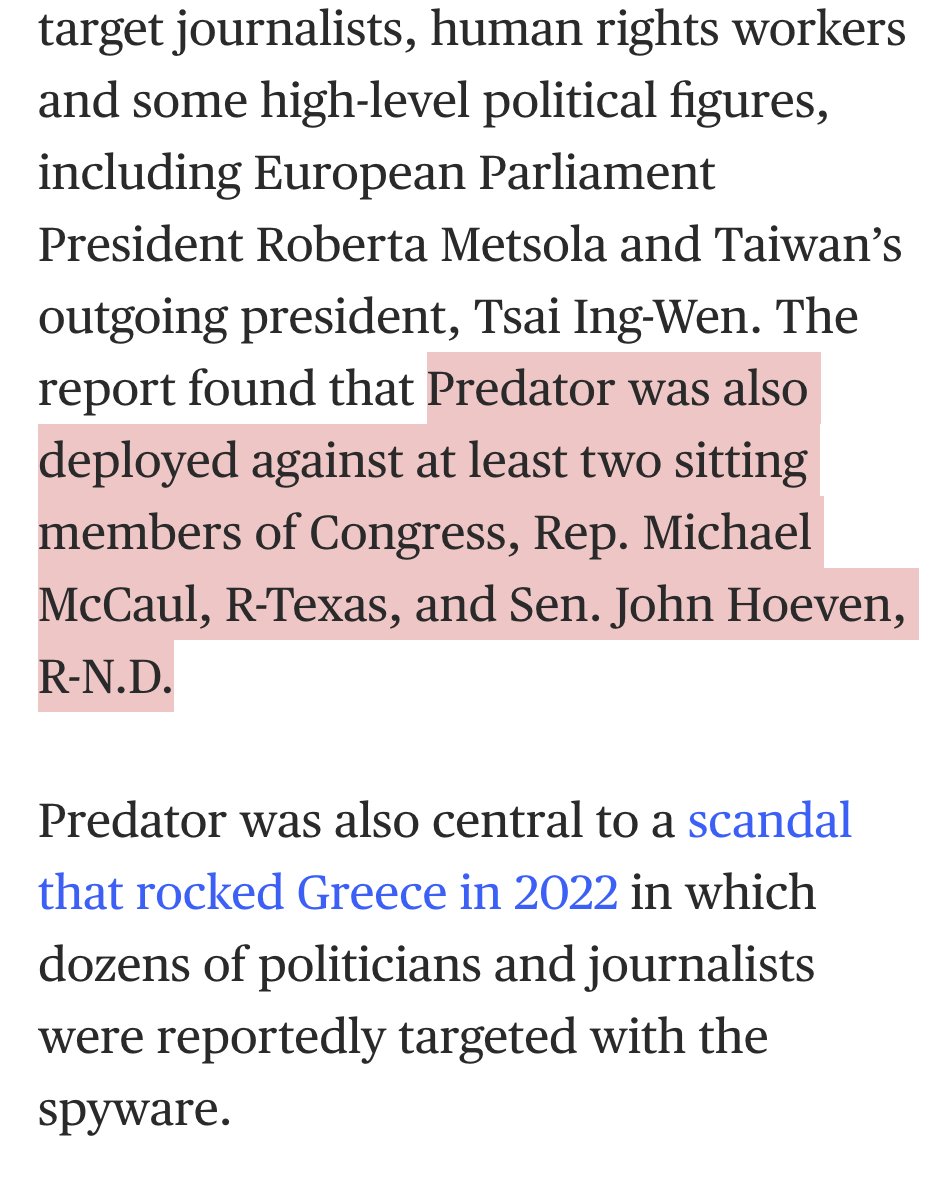
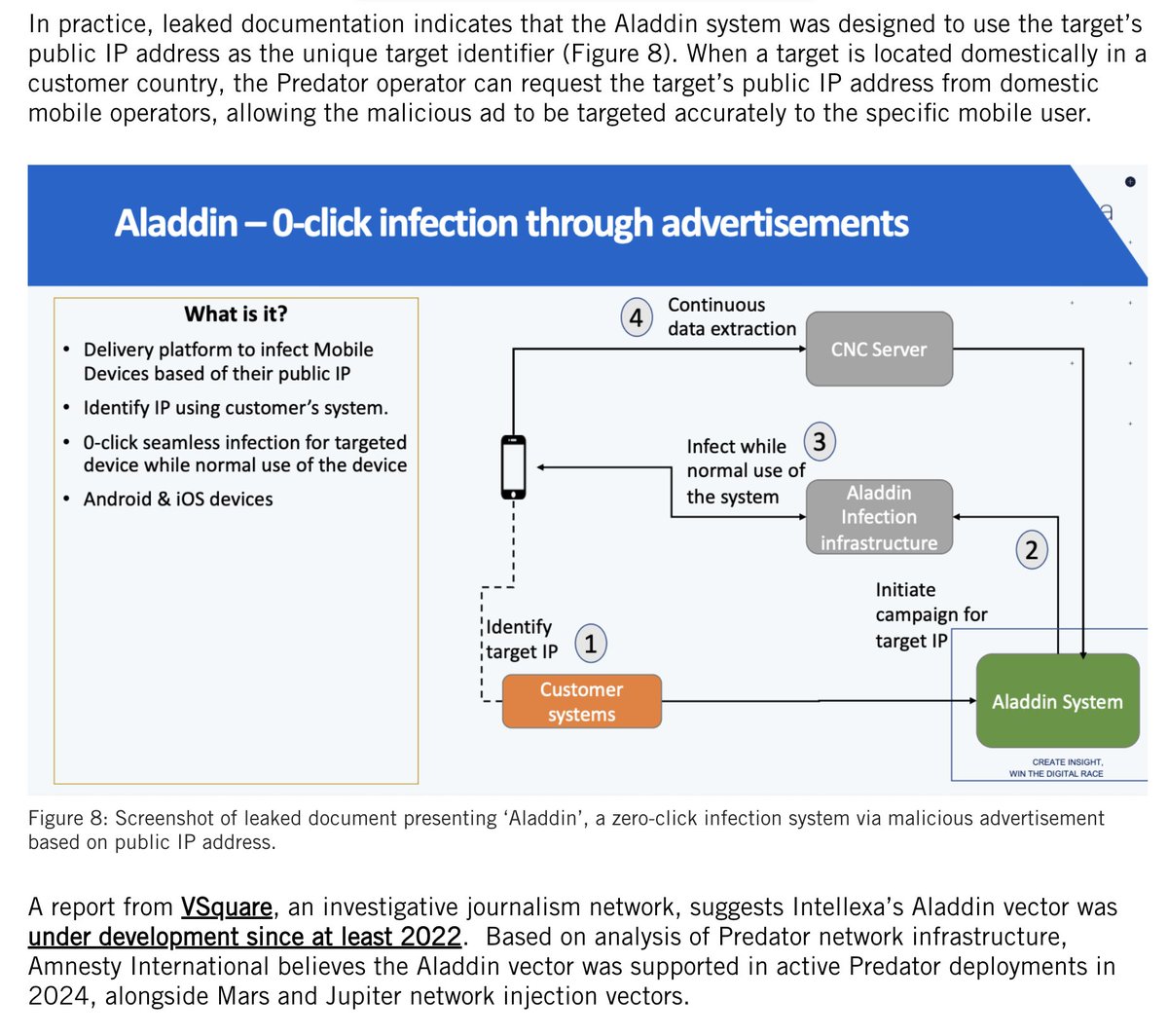
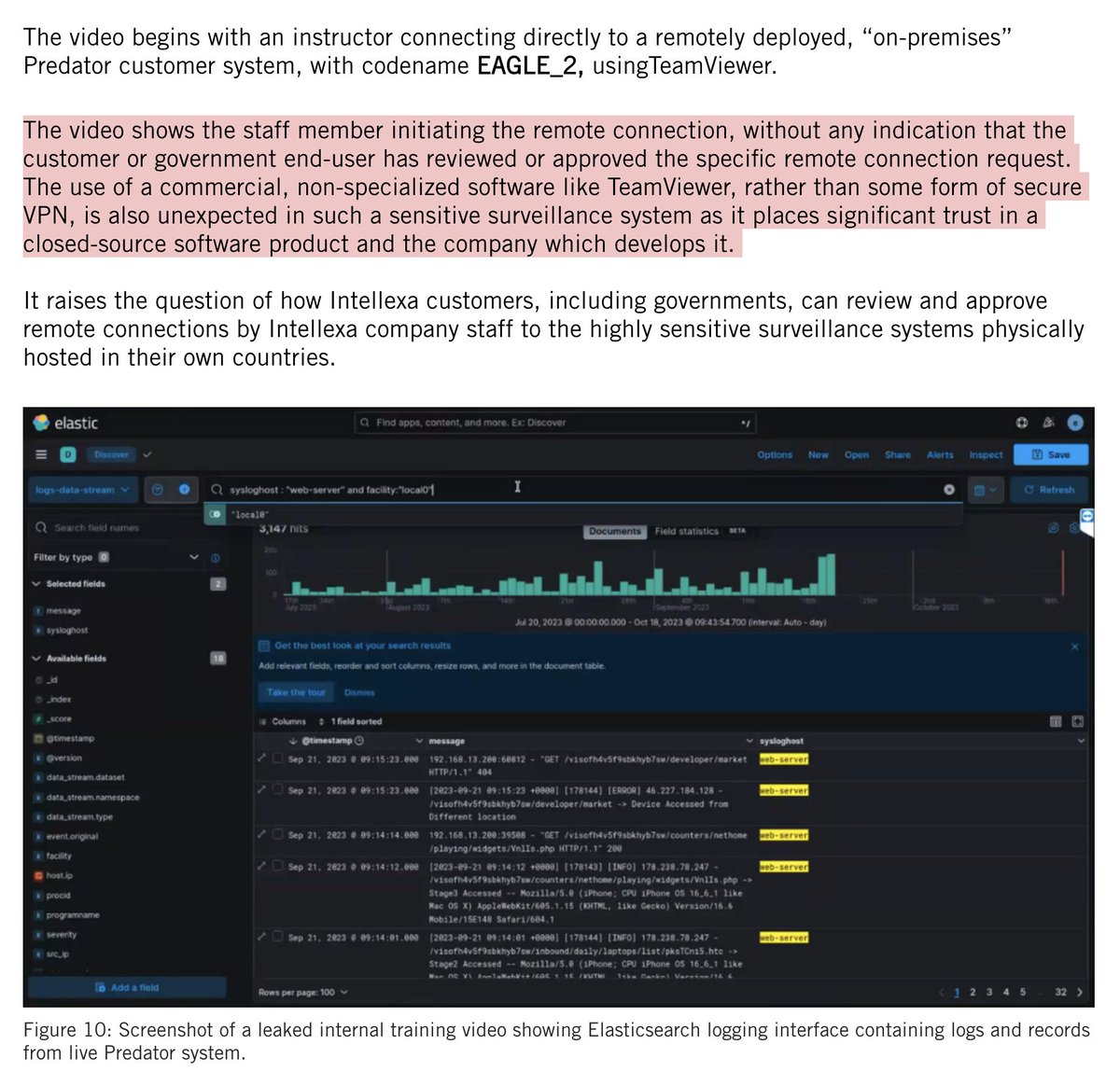
MUST WATCH: investigation by @WSJ shows 100+ Proud Boys coordinating, instigating and leading key elements of the #Capitol breach
Proud Boy 1: "Lets take the f* ** capitol"
Proud Boy 2: "Lets not F*** yell that alright"...
Etc.
wsj.com/video/video-in…
Proud Boy 1: "Lets take the f* ** capitol"
Proud Boy 2: "Lets not F*** yell that alright"...
Etc.
wsj.com/video/video-in…
2/ The investigation walks through the footage (props to @WSJ, there's so much!) starting with Proud Boys staging under the direction of leaders including (now-arrested) Joe Biggs outside the #Capitol 


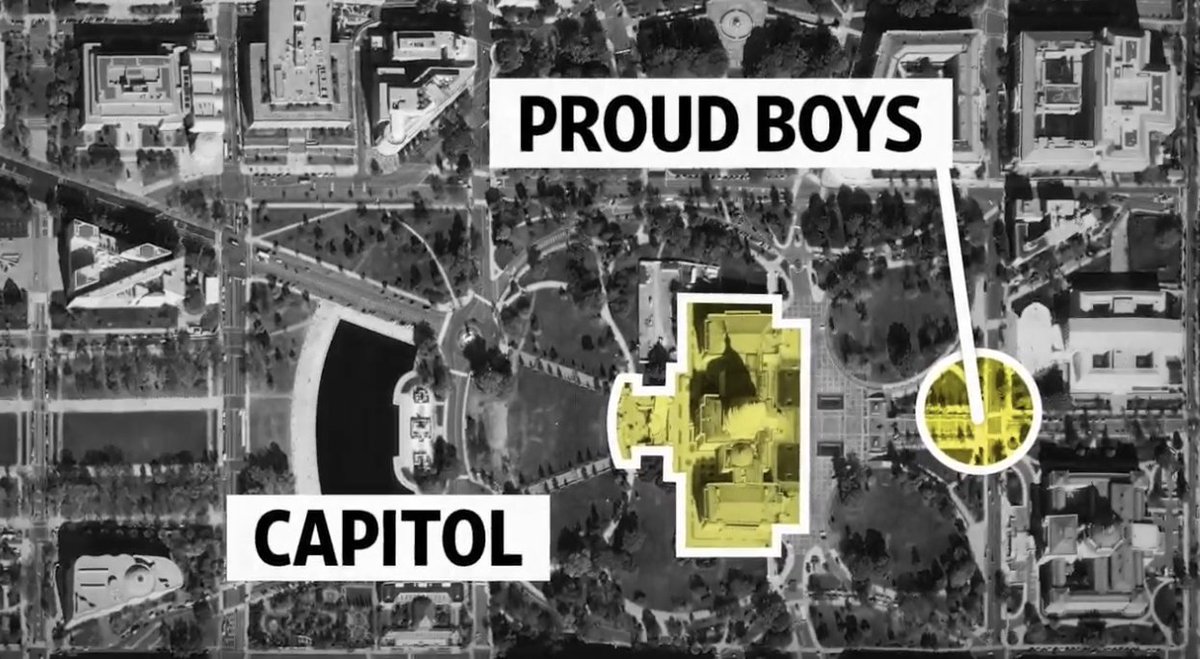


3/ In the staging area, a Proud Boy identified as Dan Scott aka 'Milkshake' yells "lets take the f***ng capitol"
-Milkshake is admonished by another PB.
-Someone makes fun of 'Milkshake' for the indiscretion(?). Some laughter.
-"Don't yell it, do it" says another, quietly.



-Milkshake is admonished by another PB.
-Someone makes fun of 'Milkshake' for the indiscretion(?). Some laughter.
-"Don't yell it, do it" says another, quietly.




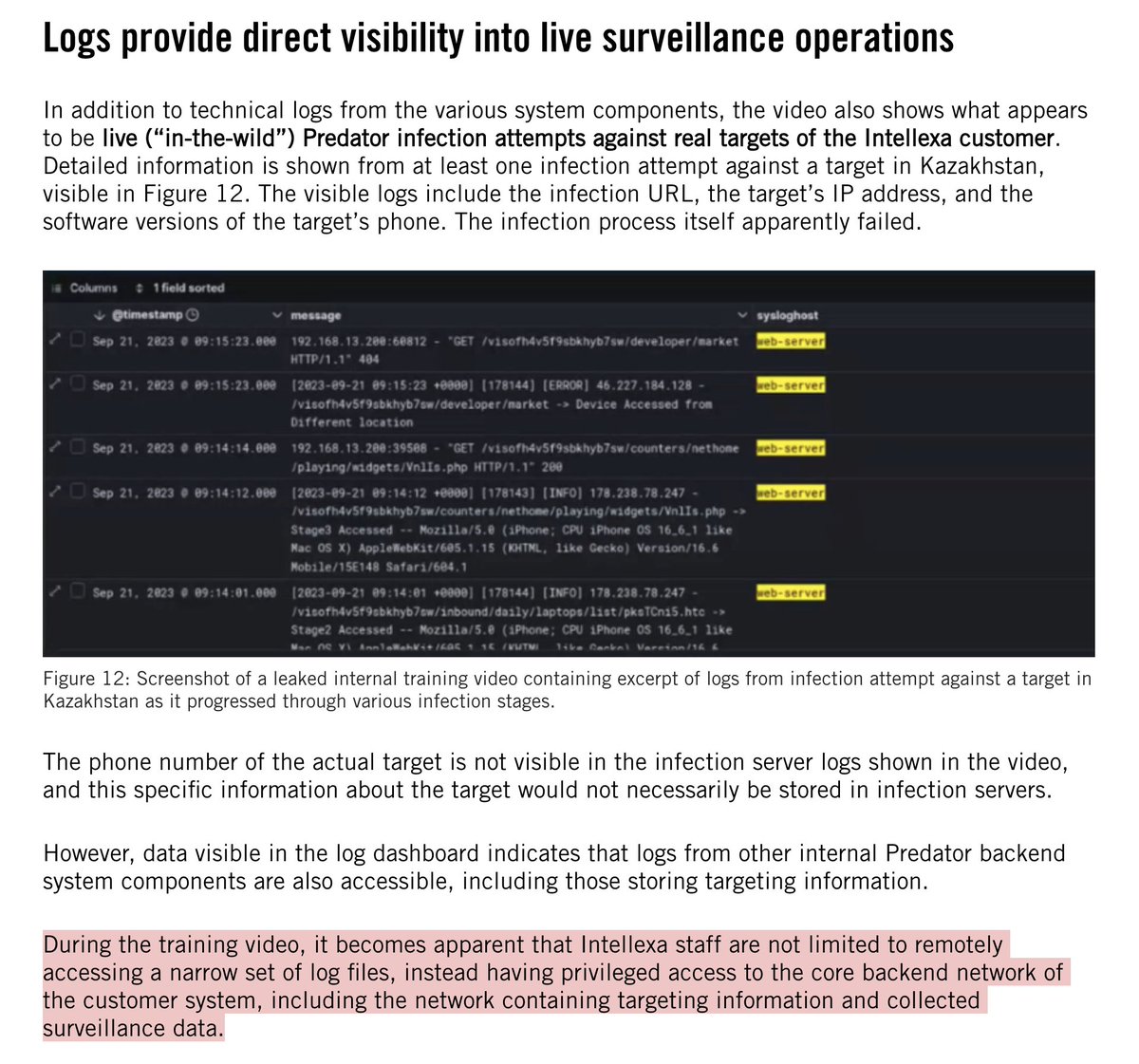
4/ The @WSJ places key Proud Boys from pre-breach meet-ups as instigators of later violence and activity by the crowd.
This absolutely matches what many of us have observed...

This absolutely matches what many of us have observed...

5/ Breach begins: @WSJ finds Proud Boys leader Joe Biggs in the crowd at an outer police cordon, communicating with a man in a red hat.
Minutes later, red hat man is the 1st past the breached police line.


Minutes later, red hat man is the 1st past the breached police line.



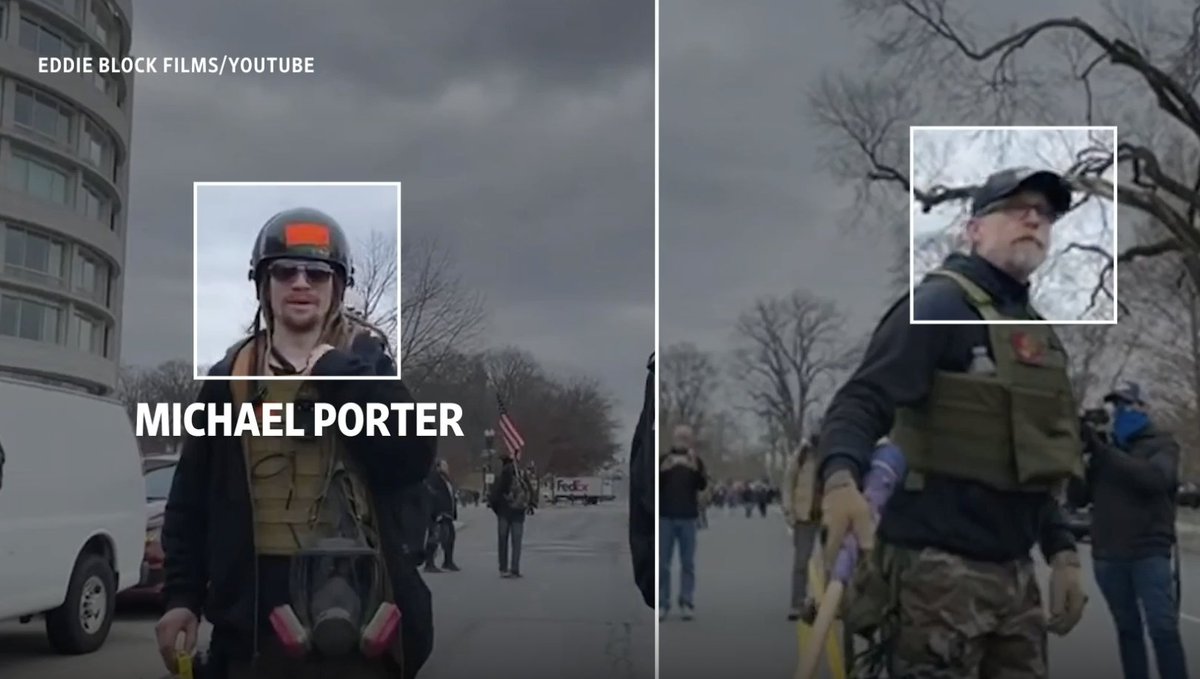
6/ As the first police line goes down we see multiple identifiable Proud Boys at the front. @WSJ names Michael Porter, for example.
Note the orange tape on helmets. This is an identification sign that many of us observed Proud Boys using throughout the day.
Note the orange tape on helmets. This is an identification sign that many of us observed Proud Boys using throughout the day.

7/ Proud Boys stay at the front of the rush of people, squaring off as they encounter #Capitol Police at the West Entrance. The @WSJ spots Proud Boy #Spazzo.
Remember him? He was the earpiece-wearing window breacher.

Remember him? He was the earpiece-wearing window breacher.
https://twitter.com/jsrailton/status/1350148617542238210


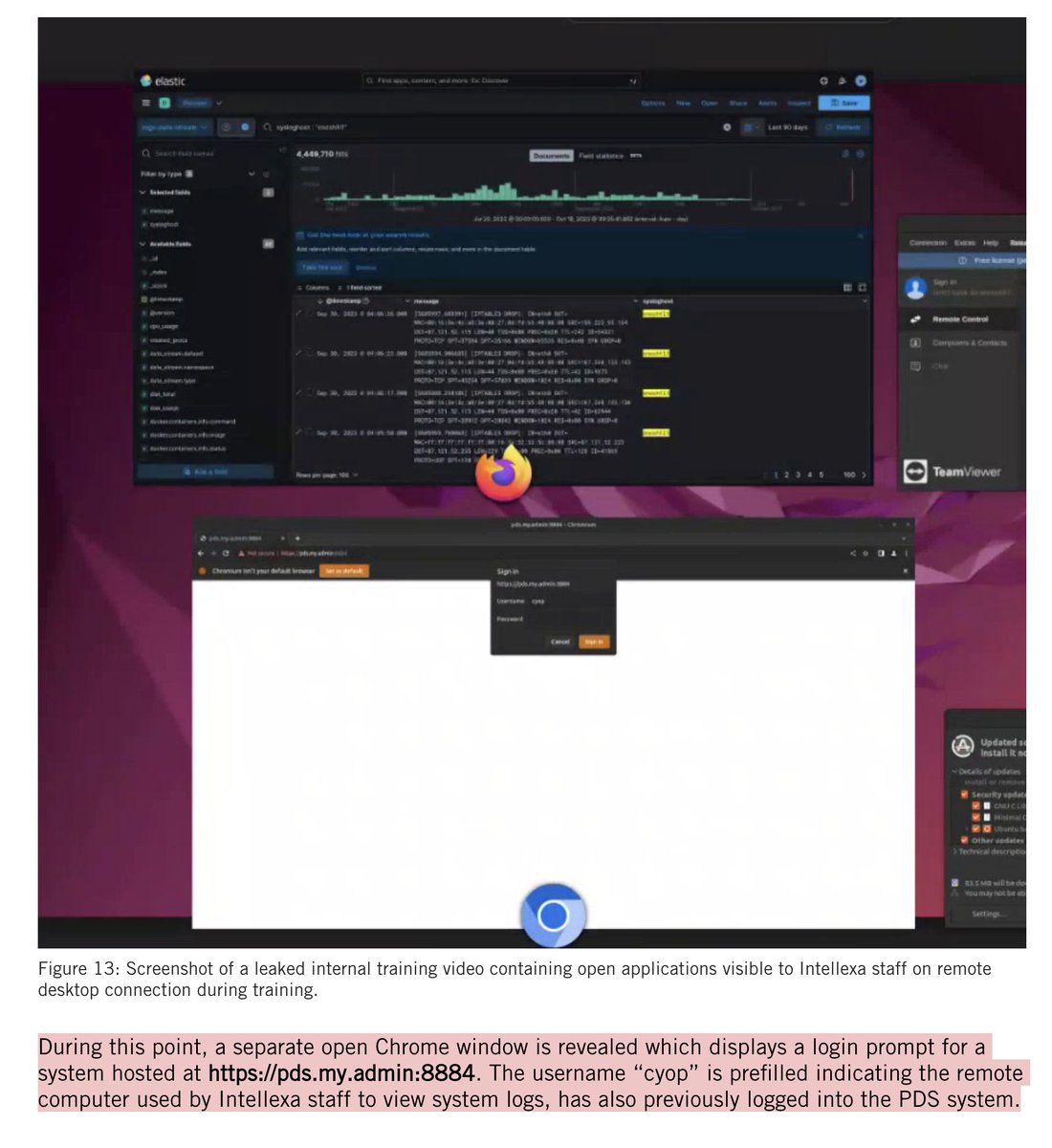
@WSJ 7/ Zen sidebar on window-breacher Dominic ‘Spazzo’ Pezzola: his lawyer claimed to the @WSJ that his radio earpiece was "for listening to music" 

8/ A Proud Boy exhorts the crowd gathering in front of the police line at base of Capitol:
"Do you want your house back?... Take it!"
Note the orange tape. Also, here's now-arrested Robert Gieswein.
Details on how some of us originally ID'd him here👇

"Do you want your house back?... Take it!"
Note the orange tape. Also, here's now-arrested Robert Gieswein.
Details on how some of us originally ID'd him here👇
https://twitter.com/arawnsley/status/1350989535954530315


9/ After staying in the front of the melee w/police... some Proud Boys flank the officers and join a group fighting their way up the left side, through scaffolding and stairs.
Dominic ‘Spazzo’ Pezzola & Gieswein are spotted. Gieswein sprays something at officers...

Dominic ‘Spazzo’ Pezzola & Gieswein are spotted. Gieswein sprays something at officers...


10/ Its 2:12 pm. Now up the stairs and against the building Dominic ‘Spazzo’ Pezzola uses a police shield to breach the window, then steps back and lets others including Gieswein inside accompanied by cries of "Go go go!" Then joins them. 



11/ The breaching party is inside. Men including Gieswein & Spazzo encounter, then chase officer Eugene Goodman up the stairs..
They come incredibly close to the undefended lawmakers in the Senate (door highlighted in blue). Thankfully, Goodman distracts them.

They come incredibly close to the undefended lawmakers in the Senate (door highlighted in blue). Thankfully, Goodman distracts them.


12/ Proud Boys leader Joe Biggs isn't far behind.
"This is awesome"
Pic right: Biggs has told @DailyMail he
- only went into the #Capitol to find a bathroom
- no planned storming...
- he actually meant "awe-inspiring" & also "awful"
SMH.
Source: dailymail.co.uk/news/article-9…

"This is awesome"
Pic right: Biggs has told @DailyMail he
- only went into the #Capitol to find a bathroom
- no planned storming...
- he actually meant "awe-inspiring" & also "awful"
SMH.
Source: dailymail.co.uk/news/article-9…


13/ Shortly after, and now back outside, the main police line is breached. Other Proud Boys make it into #Capitol with this larger group. One takes this selfie.
Another roams halls calling out for @SpeakerPelosi to "come out and play" His lawyer says "comments were in jest"


Another roams halls calling out for @SpeakerPelosi to "come out and play" His lawyer says "comments were in jest"



14/ The @WSJ piece is an excellent, damming illustration of what many of us observed: Proud Boys played a key role at the #Capitol.
Congrats to the team that assembled it & their colleagues that helped out.
Why I'm a @WSJ subscriber. Subscribe here: subscribe.wsj.com
Congrats to the team that assembled it & their colleagues that helped out.
Why I'm a @WSJ subscriber. Subscribe here: subscribe.wsj.com
15/ Coda: Robert Gieswein wore several patches, including Woodland Wild Dogs (his own thing), & has some militia connections.
However, remains unclear (to me) whether his co-presence w/Proud Boys around #Capitol points a longer-term relationship.

However, remains unclear (to me) whether his co-presence w/Proud Boys around #Capitol points a longer-term relationship.
https://twitter.com/jsrailton/status/1351006823915151365

• • •
Missing some Tweet in this thread? You can try to
force a refresh