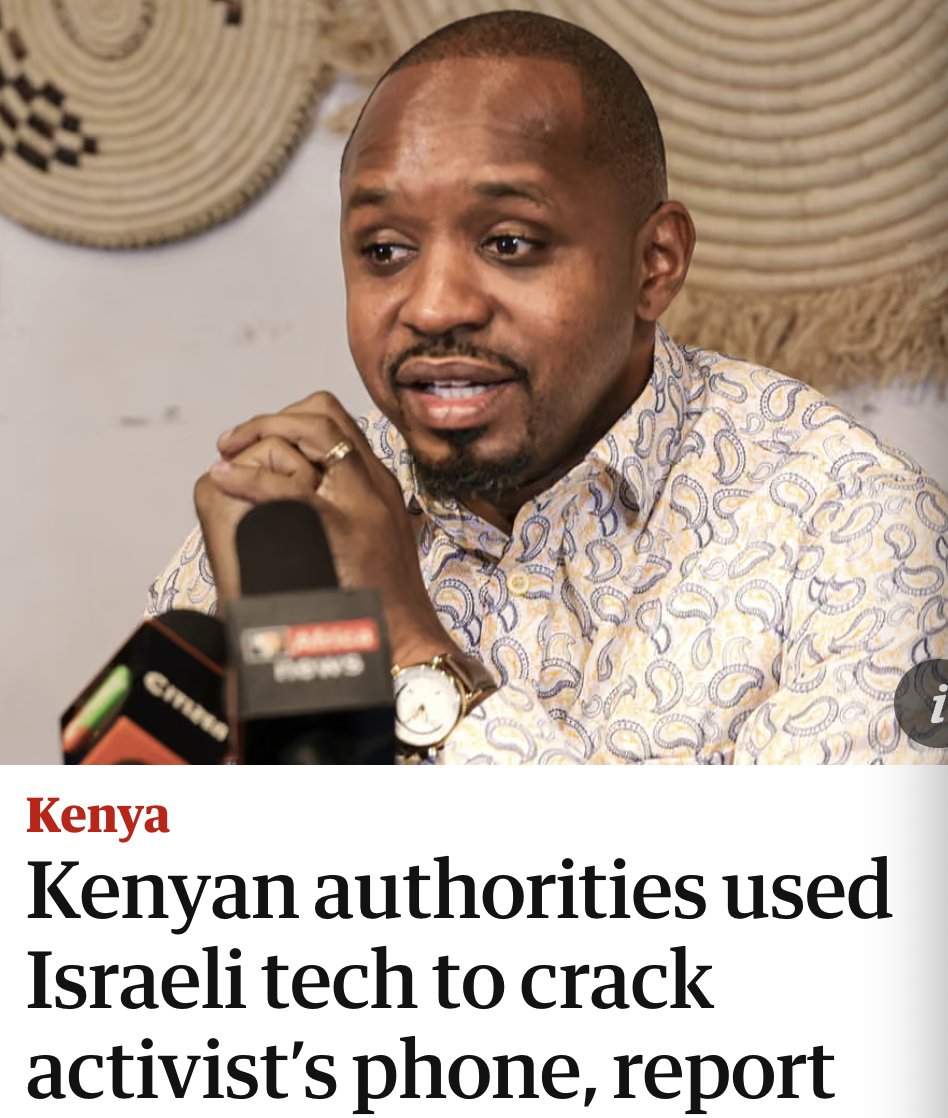
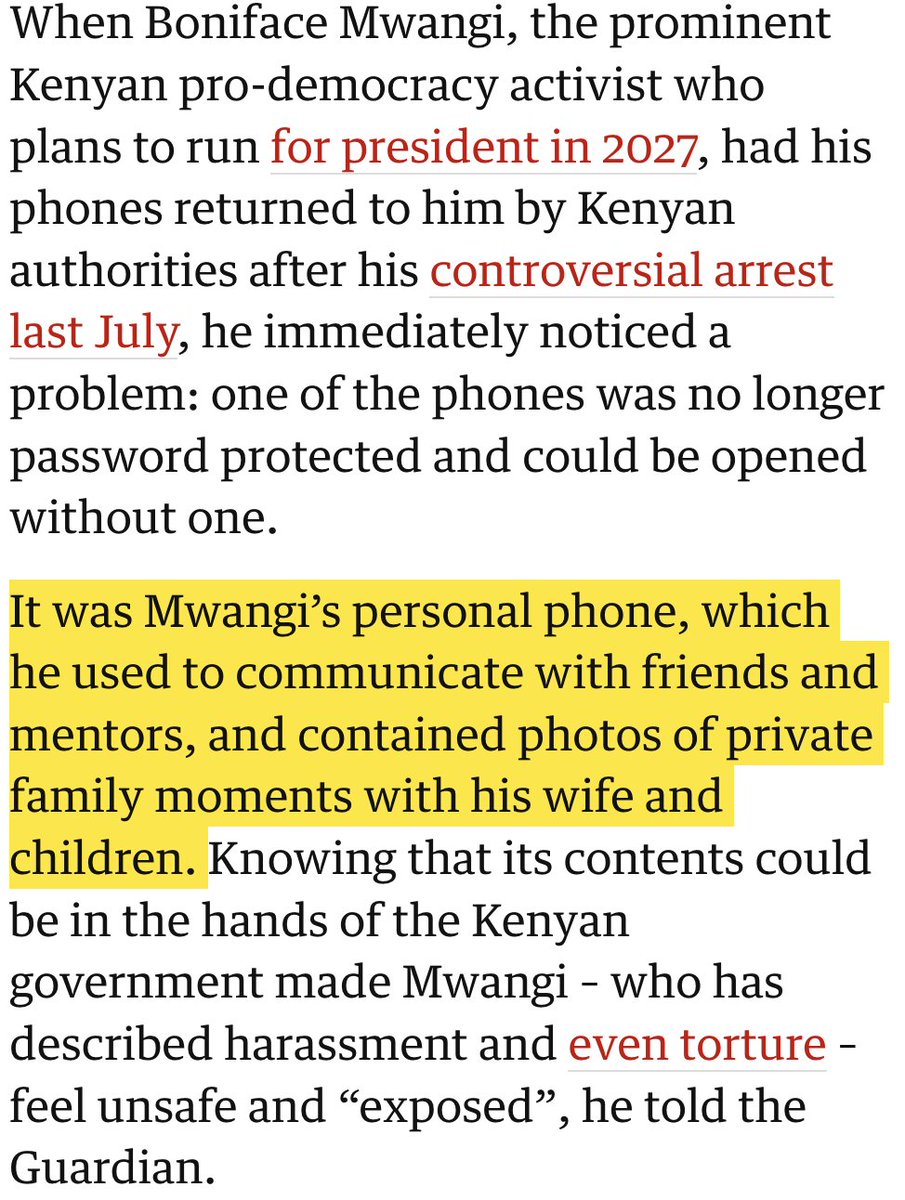
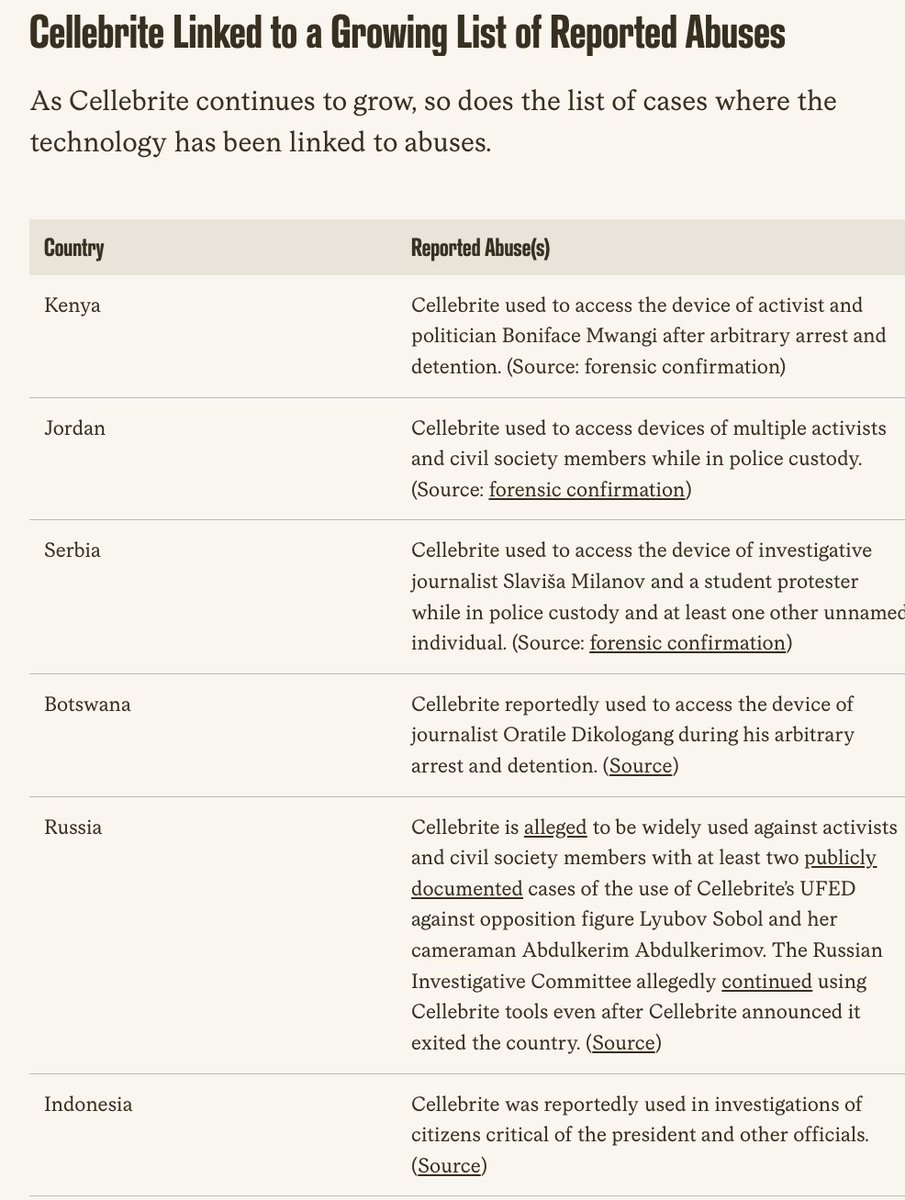
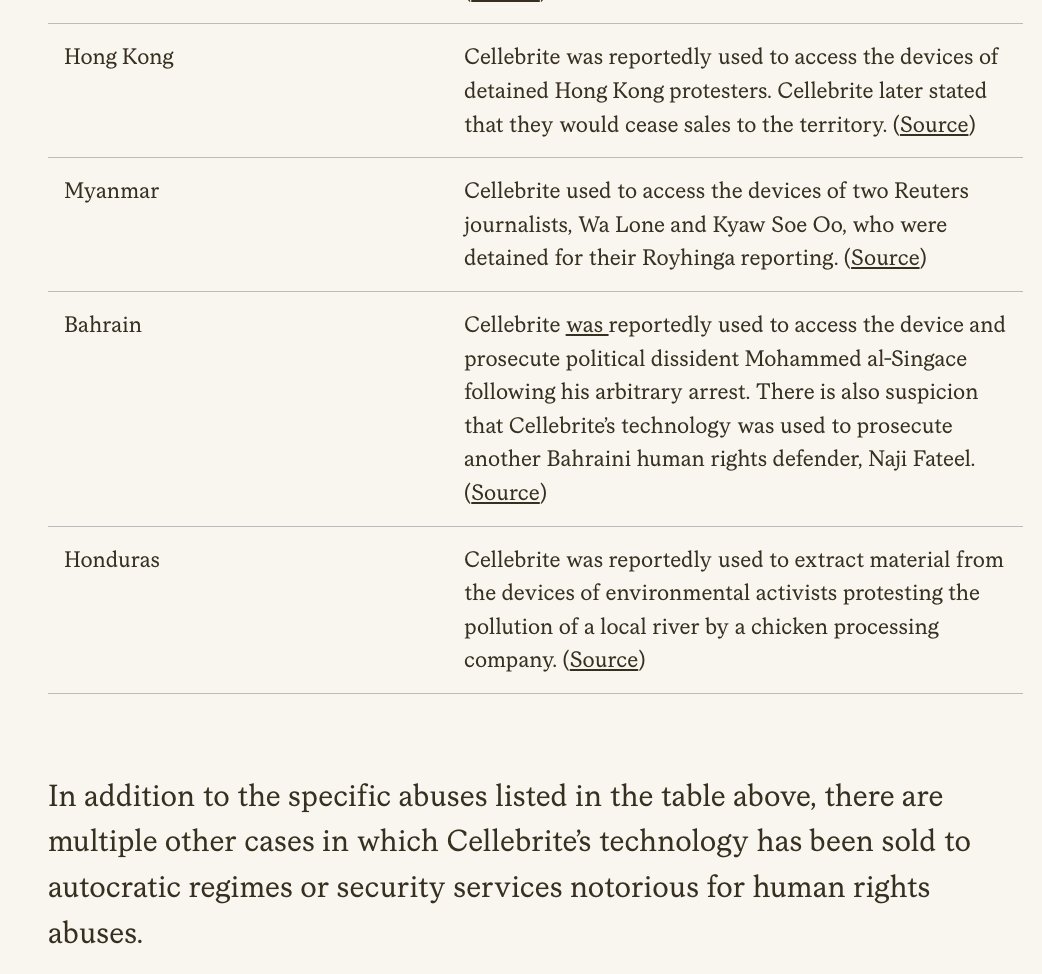
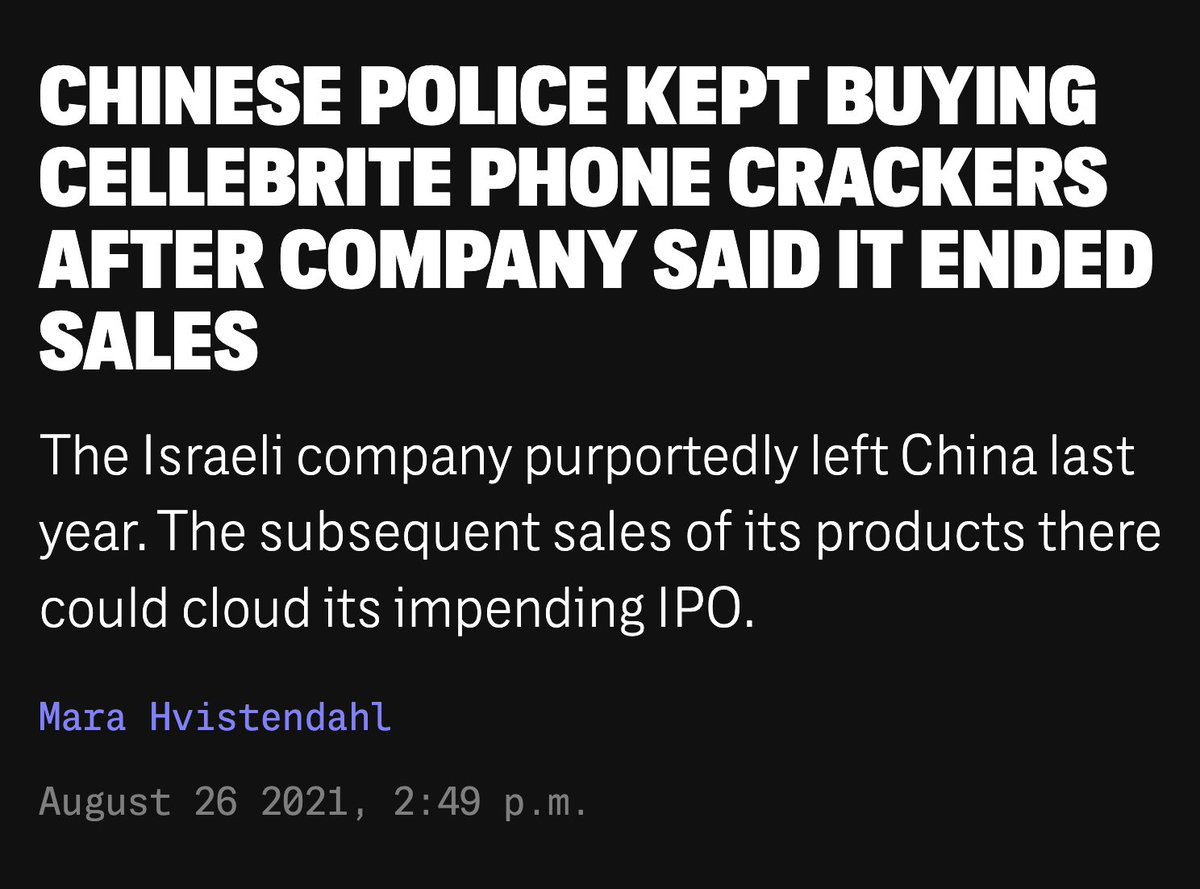
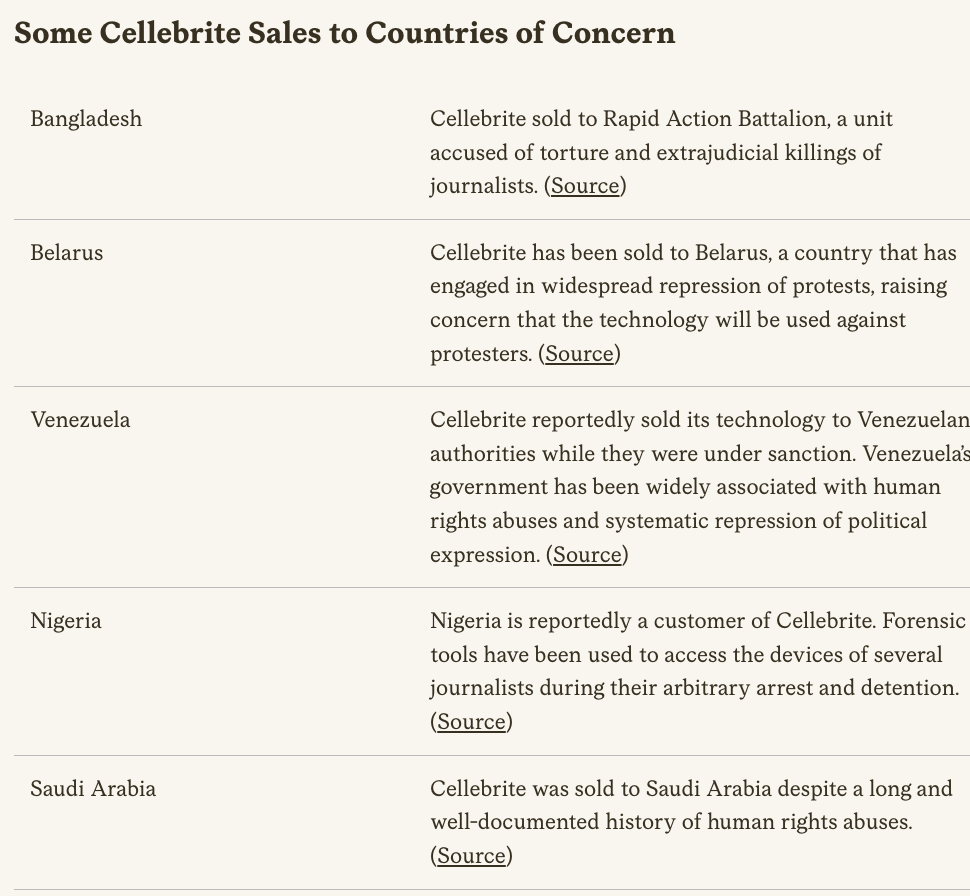
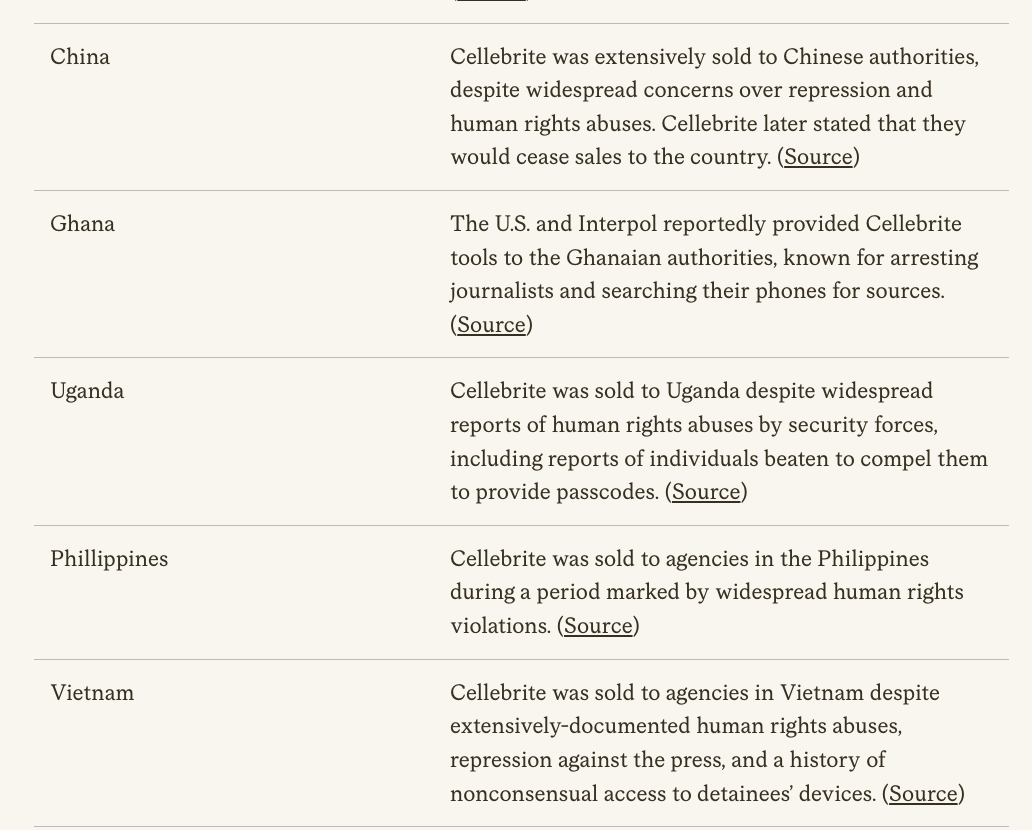
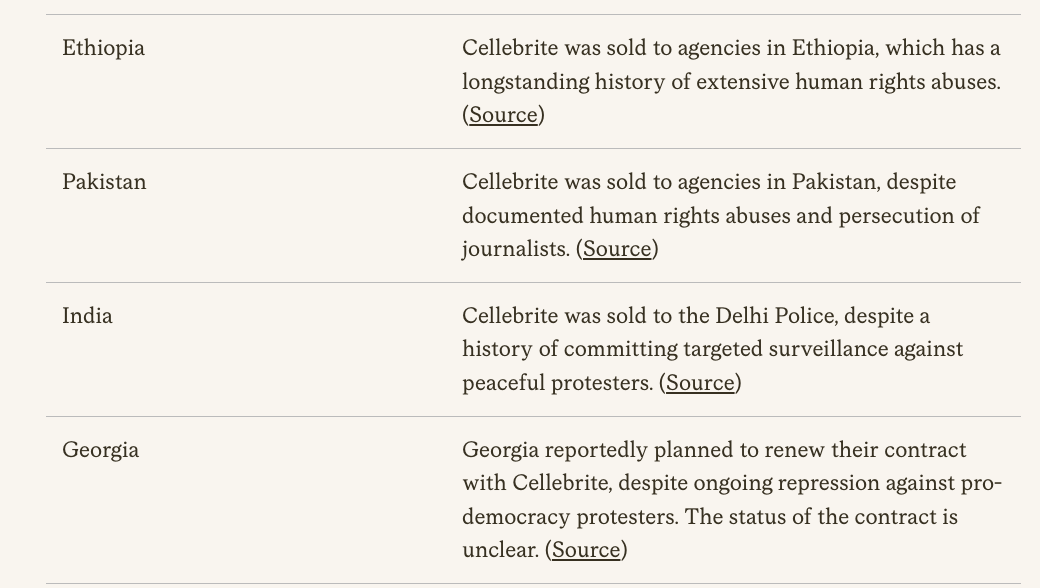
New #OathKeepers indictment is surfacing interesting puzzle pieces, like:
-Coordination between regional Oath Keepers groups
-A Dec. North Carolina training camp & contingent on the 6th.
-Weapons brought up separately
& more
Quick THREAD 1/
Source: justice.gov/usao-dc/press-…


-Coordination between regional Oath Keepers groups
-A Dec. North Carolina training camp & contingent on the 6th.
-Weapons brought up separately
& more
Quick THREAD 1/
Source: justice.gov/usao-dc/press-…



2/ "...our duty as Americans to fight, kill and die for our rights."
By November 2020 there is talk among the conspirators of the need to get violent..
By Dec. 20 hotel reservations are made by CALDWELL for the 6th... and CROWL has attended a North Carolina training camp.
By November 2020 there is talk among the conspirators of the need to get violent..
By Dec. 20 hotel reservations are made by CALDWELL for the 6th... and CROWL has attended a North Carolina training camp.

3/ By Dec 30, WATKINS (Ohio) confirms to CALDWELL (Virginia) that her group will come. They discuss staging, logistics..
CALDWELL says a "full bus 40+" people coming from North Carolina.
[Observation: I suspect we will learn a lot more about NC folks in coming weeks]
CALDWELL says a "full bus 40+" people coming from North Carolina.
[Observation: I suspect we will learn a lot more about NC folks in coming weeks]

4/ "That way the boys don't have to try to schlep weps on the bus"
-CALDWELL to WATKINS on Dec 30, explaining that an unnamed [PERSON THREE] will drive up a truck with weapons separately from one of the bussed-in contingents.
"Leadership only" conference call is named "DC op"

-CALDWELL to WATKINS on Dec 30, explaining that an unnamed [PERSON THREE] will drive up a truck with weapons separately from one of the bussed-in contingents.
"Leadership only" conference call is named "DC op"


5/ Chats describe how CROWL & WATKINS (and others) will "link up" with the "North Carolina crew" On the 4th they depart Ohio, headed for DC.
On the morning of January 6th, they kit up for battle and head to the #Capitol.

On the morning of January 6th, they kit up for battle and head to the #Capitol.
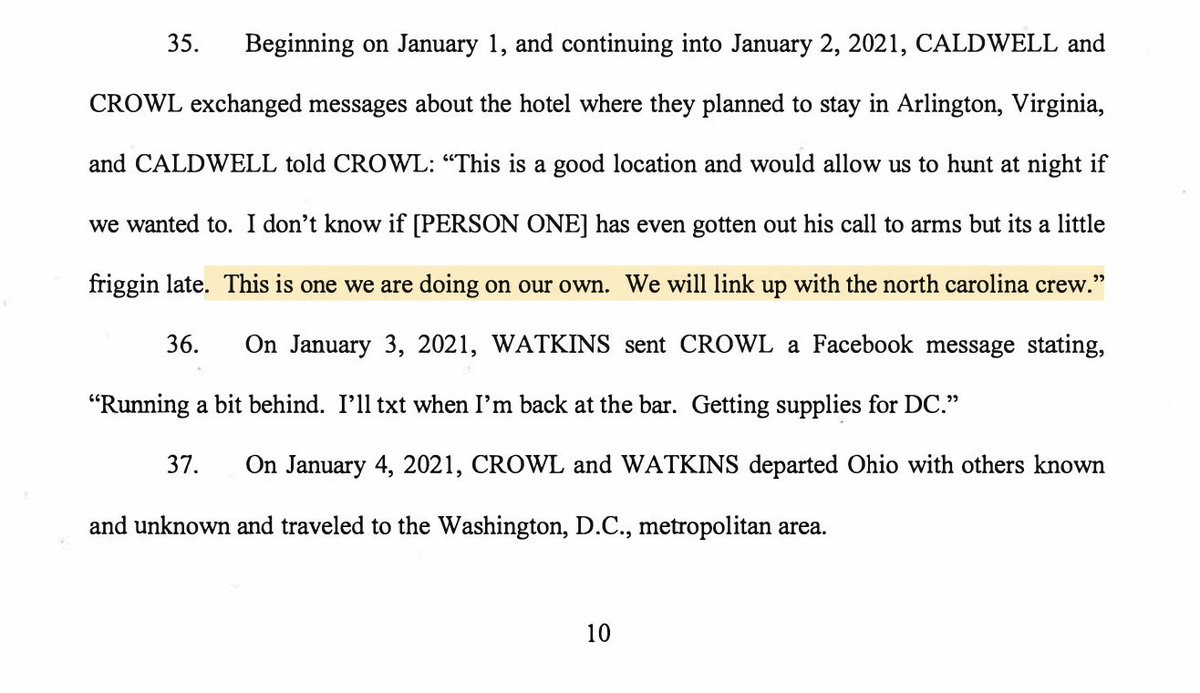

6/ Here they are: CROWL, WATKINS & others in a disciplined, geared-up line... moving up the #Capitol steps on the East side.
Per the indictment, they forced their way past police and into the building.
Footage: @rstevensbrody
Per the indictment, they forced their way past police and into the building.
Footage: @rstevensbrody
7/ Meanwhile, over on the West side of the #Capitol, CALDWELL & unnamed others are in the mob fighting through police lines, up the stairs, and eventually breaching the doors.
By 3:05pm he reports making it inside.
By 3:05pm he reports making it inside.

8/ After the storming of the #Capitol they start trying to hide their tracks, deleting messages, etc.
WATKINS & CROWL return to Ohio. But after they are identified on the 14th (see tweet👇👇) they head to Virginia to stay w/ CALDWELL.

WATKINS & CROWL return to Ohio. But after they are identified on the 14th (see tweet👇👇) they head to Virginia to stay w/ CALDWELL.
https://twitter.com/jsrailton/status/1349791278976921604

Open questions:
-What role did Oath Keepers leader Elmer Stewart Rhodes "[PERSON ONE]" play? He was in crowd (pic).
-Reporting has focused on OH & VA Oath Keepers at #Capitol, but Important to know about others, esp. NC.
Pic: pbs.org/wgbh/frontline…
-What role did Oath Keepers leader Elmer Stewart Rhodes "[PERSON ONE]" play? He was in crowd (pic).
-Reporting has focused on OH & VA Oath Keepers at #Capitol, but Important to know about others, esp. NC.
Pic: pbs.org/wgbh/frontline…

• • •
Missing some Tweet in this thread? You can try to
force a refresh